Even more Android security woes as computer scientists discover permissions gap
All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
Computer and mobile device security is a tough business. There's hype and then there are real threats and so far most in mobile have been hype (but see AVG-gate). Still, Android is either an OS with a lot of security vulnerabilities or everyone just likes to pick on it. Either way, between Carrier IQ earlier this week and now this paper from North Carolina State University, the little robot is having a tough time.
Computer scientists at NCSU created an app called 'Woodpecker' that would search for app vulnerabilities in Androids's permission-based security model. In short, when you install an app in Android, it tells you what that app can access e.g. user info, data, geolocation, recording sound, etc. Basically if you don't think a wallpaper app should have access to say, recording sounds, you prevent the app from installing. The problem is this: apps can unknowingly grant permissions to other apps, allowing a seemingly innocuous program to gain access to functions not agreed to by the user.
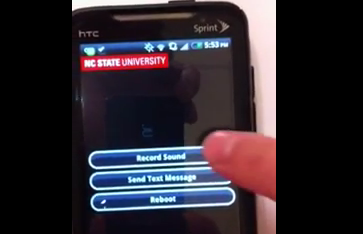
In the paper (PDF), the researchers looked at eight Android phones: HTC Legend, EVO 4G, Wildfire S; Samsung Epic 4G; Motorola Droid, Droid x and Google Nexus One and S. Only on-board, pre-installed software was analyzed e.g. OEM or carrier software, but not third party apps. In short, they found they could install apps that had access to higher level functions not specifically granted by the user via what is called a "confused deputy attack" where "where one app is tricked by another into improperly exercising its privileges". The culprit? OEM apps that unwittingly revealed their higher level permissions to 'Woodpecker--the more OEM apps, the more vulnerable. This is because, according to the researchers, "...app markets do not report the actual permissions granted to an app. Instead they report only the permissions an app requests or embodied in the manifest file".
As can be seen in the video above, an app is installed with these higher level functions but no warning was issued during installation. The question is this: is this a real threat or potential? Looks to be potential only at this point, but then again who knows. The researchers concluded it does "constitute a tangible security weakness" for Android.
"These leaked capabilities can be exploited to wipe out the user data, send out SMS messages (e.g., to premium numbers), record user conversation, or obtain the user’s geo-location data on the affected phones – all without asking for any permission."
Windows Phone seems to be inoculated against such attacks because, in theory, the apps are vetted. But then again, the AVG app did get by Microsoft meaning perhaps even Windows Phone apps could have similar vulnerabilities (what are called "capability leaks"). That AVG app, according to Justin Angel, improperly used the Geo Location (GeoCoordinateWatcher) in a way not granted by the certification guidelines. One thing working in our favor though is the sand-boxed nature of our OS and apps, meaning deep-level functions cannot be touched (unless you hack and interop-unlock, of course).
Source: NCSU; via The Register
All the latest news, reviews, and guides for Windows and Xbox diehards.

Daniel Rubino is the Editor-in-Chief of Windows Central. He is also the head reviewer, podcast co-host, and lead analyst. He has been covering Microsoft since 2007, when this site was called WMExperts (and later Windows Phone Central). His interests include Windows, laptops, next-gen computing, and wearable tech. He has reviewed laptops for over 10 years and is particularly fond of Qualcomm processors, new form factors, and thin-and-light PCs. Before all this tech stuff, he worked on a Ph.D. in linguistics studying brain and syntax, performed polysomnographs in NYC, and was a motion-picture operator for 17 years.
