Cybersecurity
Latest about Cybersecurity

What is 94fbr Minecraft, and is it safe?
By Colton Stradling published
94fbr 94fbr Minecraft boils down to one defining characteristic, but is it worth getting involved in the shady 94fbr Minecraft scene?
Microsoft's GitHub is under siege as security experts claim over 100,000 Github repositories are infected
By Colton Stradling published
GitHub In a report by Apiiro, a security firm, they have concluded that an ongoing attack has infected well over 100,000 Github repositories.
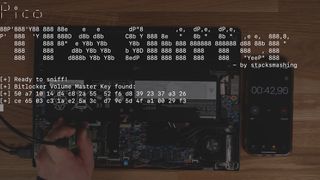
BitLocker vulnerability discovered and cracked using a $10 Raspberry Pi Pico
By Colton Stradling published
Cheap Hack With a Frankenstein of a hack, a Raspberry Pi Pico was used to crack BitLocker on devices with an external TPM.

Russian hacker group breaches email accounts of top Microsoft executives to seek information about ... itself
By Kevin Okemwa published
UH-OH A group of Russian hackers were able to gain access to email accounts belonging to Microsoft's top executives.

Microsoft's GitHub is being abused by hackers and ransomware groups. But can it be fixed?
By Colton Stradling published
GitHub A recent report by the Insikt Group highlighted how hacker groups use GitHub to carry out their attacks.

"Whether a company loses a factory in a fire or millions of files in a cybersecurity incident it may be material to investors" A new SEC rule went into effect requiring public companies to report cybersecurity incidents in 4 days
By Colton Stradling published
Excel FTW From forcing public companies to report cyber incidents within 4 days, to mandating compliance standards for 16 sectors, the SEC is finally holding companies responsible for negligence.

"We are sending a strong message to those who seek to create, sell, or distribute fraudulent Microsoft products for cybercrime: We are watching, taking notice, and will act to protect our customers." Microsoft takes down cybercrime group Storm-1152
By Colton Stradling published
Crime != pay Microsoft estimates Storm-1152 has sold 750 million fake Microsoft accounts. Now Microsoft has seized its domains and U.S. based infrastructure.

"Hundreds of consumer and enterprise-grade devices from various vendors, including Intel, Acer, and Lenovo, are potentially vulnerable" Binarly warns about LogoFAIL
By Colton Stradling published
LogoFAIL LogoFAIL impacts potentially millions of endpoints across hundreds of device models by affecting the UEFI reference code.

Microsoft names new CISO as it aims to combat increasing cybersecurity threats
By Sean Endicott published
Perimeter secured Microsoft will soon have a new chief information security officer for the first time in 14 years. Bret Arsenault will leave his current role and become Microsoft Chief Security Advisor.
Get the Windows Central Newsletter
All the latest news, reviews, and guides for Windows and Xbox diehards.




