InSpectre will quickly check if your PC is vulnerable to Meltdown and Spectre
Curious to see if your PC is vulnerable to Meltdown and Spectre? There's now a simple tool for discerning just that.

All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
Amid the fallout following the disclosure of the Meltdown and Spectre processor exploits in recent weeks, Microsoft, Intel, and other companies have been quick to issue updates to mitigate potential attacks. However, aside from a somewhat complicated PowerShell script, there hasn't been a quick and simple way for average PC users to check whether their systems are patched and protected against each exploit – until now.
InSpectre is a new tool built by Gibson Research that simply lays out whether your PC is vulnerable to Meltdown or Spectre in a clear manner. The tool simply runs as an executable and doesn't require an installation. Once it's run, InSpectre presents you with a simple readout of your system's status, as seen in the screenshot below:
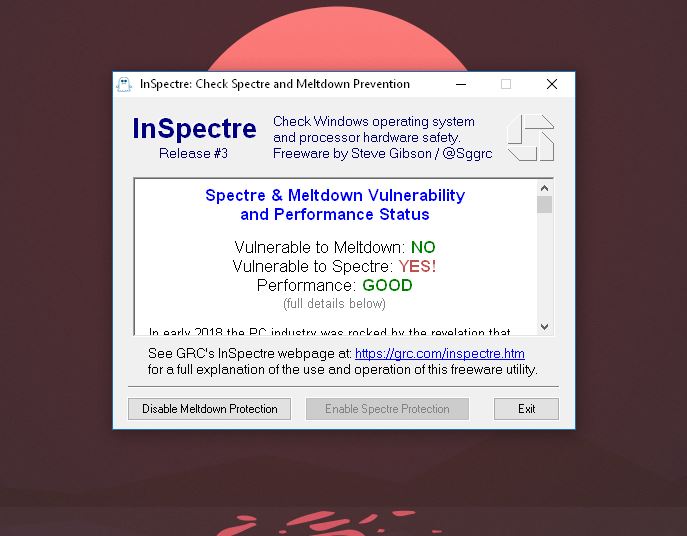
Below the results at the top of the window, you'll also find a brief description of Meltdown and Spectre, as well as a more detailed explanation of your particular PC's status.
InSpectre is an incredibly handy tool if you're still uncertain as to whether your PC is fully patched against each exploit. It's worth noting, however, that the initial release was causing false positives with antivirus programs, but that appears to be cleared up in a subsequent release. However, as a result, Microsoft browsers appear to be flagging the InSpectre website as unsafe. Gibson Research explains:
Windows Defender "SmartScreen" appears to have decided that InSpectre is malware. This also happened briefly after the release of our Never10 utility. In this case, it is likely due to the fact that InSpectre's initial release was triggering anti-virus scanners due to the program's use of a specific registry key used to enable and disable the Meltdown and Spectre protections. The second release obscures its use of that (apparently worrisome) key and now appears to pass through most A/V without trouble. So we are hopeful that this SmartScreen false alarm will disappear soon.
If you'd like to give it a shot, you can download and try InSpectre now from Gibson Research.
Microsoft talks performance impact of Meltdown and Spectre patches on your PC
All the latest news, reviews, and guides for Windows and Xbox diehards.

Dan Thorp-Lancaster is the former Editor-in-Chief of Windows Central. He began working with Windows Central, Android Central, and iMore as a news writer in 2014 and is obsessed with tech of all sorts. You can follow Dan on Twitter @DthorpL and Instagram @heyitsdtl.
