Threat actor Patchwork accidentally attacked itself with a RAT
Patchwork attacking itself allowed Malwarebytes to see how the threat actor operates.
All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
What you need to know
- A threat actor known as Patchwork accidentally infected itself with a Remote Administration Trojan.
- Malwarebytes was able to determine the victims and methodology of Patchwork's attacks and even the local temperature of the threat actor's area.
- Patchwork's Remote Administration Trojan allowed Malwarebytes to see captured keystrokes and screenshots from the malicious group.
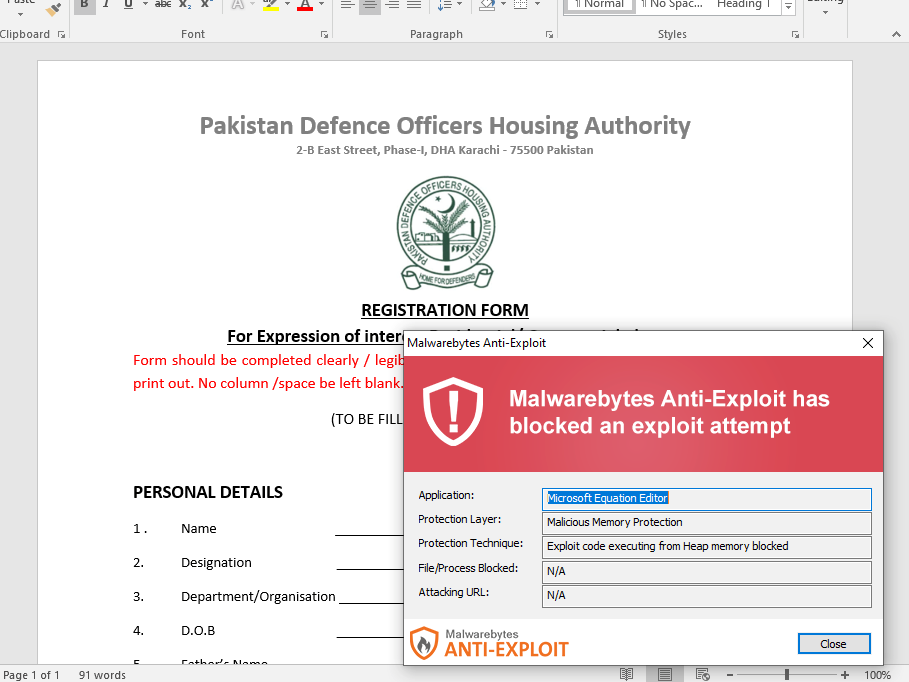
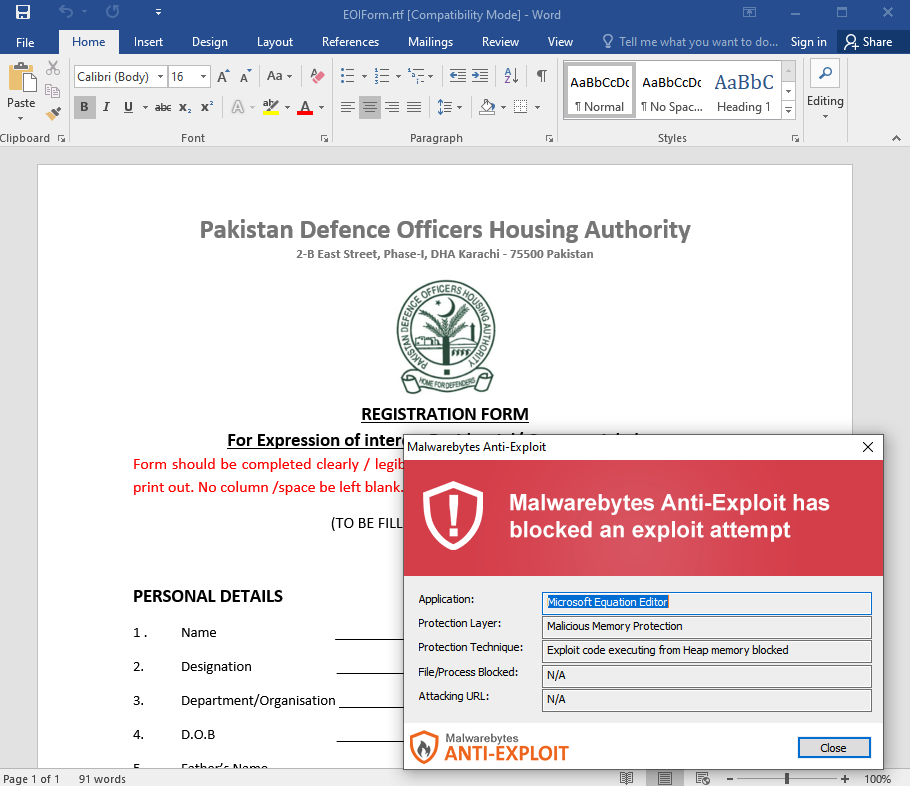
Patchwork, a threat actor based in India, accidentally infected itself with a Remote Administration Trojan (RAT). The ironic incident was discovered by Malwarebytes, which took the opportunity to gain insight as to how Patchwork utilizes RTF files to spread the BADNEWS (Ragnatela) RAT.
"Ironically, all the information we gathered was possible thanks to the threat actor infecting themselves with their own RAT, resulting in captured keystrokes and screenshots of their own computer and virtual machines," explained Malwarebytes.
As part of a recent attack, Patchwork spread malicious files by impersonating Pakistani authorities. Documents were sent out as attachments that appeared to be legitimate and important. Instead, the files contained an exploit that can compromise a computer and then execute the RAT.
The following organizations were successfully compromised by the efforts of Patchwork, according to Malwarebytes:
- Ministry of Defense- Government of Pakistan
- National Defense University of Islam Abad
- Faculty of Bio-Science, UVAS University, Lahore, Pakistan
- International center for chemical and biological sciences
- HEJ Research institute of chemistry, International center for chemical and biological sciences, univeristy of Karachi
- SHU University, Molecular medicine
Patchwork also infected itself with the RAT, which gave Malwarebytes access to quite a bit of information. Malwarebytes was able to see that Patchwork uses VirtualBox and VMWare for development. The security firm also determined that Patchwork uses VPN Secure and CyberGhost to mask its IP address.
Comedically, Malwarebytes was also able to determine the local weather of Patchwork's machines. "Other information that can be obtained is that the weather at the time was cloudy with 19 degrees and that they haven't updated their Java yet."
Malwarebytes notes that Patchwork is not as sophisticated as similar attackers in Russia and North Korea.
All the latest news, reviews, and guides for Windows and Xbox diehards.

Sean Endicott is a news writer and apps editor for Windows Central with 11+ years of experience. A Nottingham Trent journalism graduate, Sean has covered the industry’s arc from the Lumia era to the launch of Windows 11 and generative AI. Having started at Thrifter, he uses his expertise in price tracking to help readers find genuine hardware value.
Beyond tech news, Sean is a UK sports media pioneer. In 2017, he became one of the first to stream via smartphone and is an expert in AP Capture systems. A tech-forward coach, he was named 2024 BAFA Youth Coach of the Year. He is focused on using technology—from AI to Clipchamp—to gain a practical edge.
