Attackers are stealing data with fake Microsoft Store app listings
Attackers are advertising fake applications and websites to get malware onto people's computers.
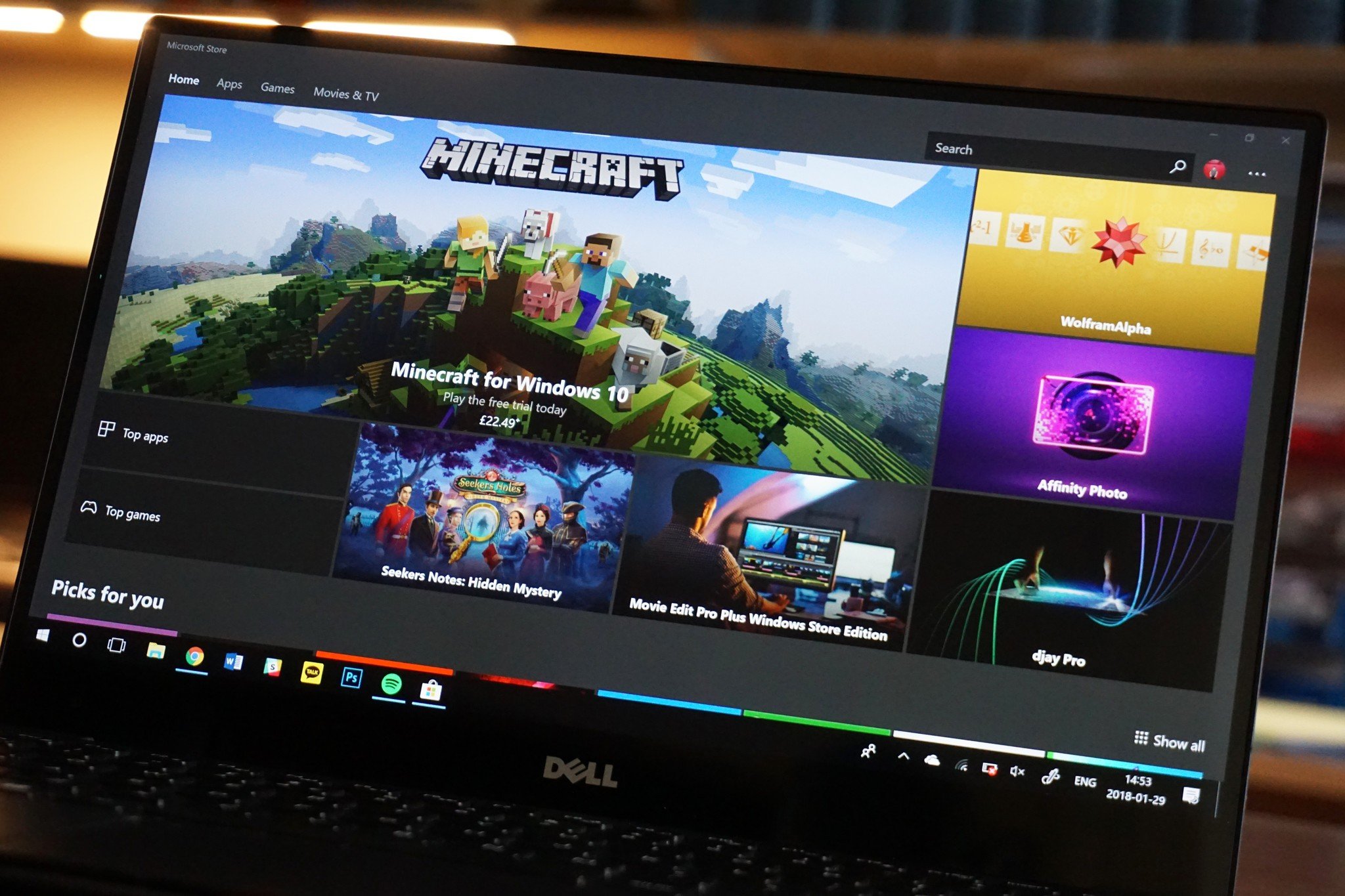
All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
What you need to know
- Attackers are using fake Microsoft Store app listings and websites to get malware onto people's computers.
- The installed malware can be used to still passwords, documents, and cryptocurrency wallets.
- The attacks are said to target countries in South America at the moment.
New malware attacks mimicking the Microsoft Store, Spotify's website, and a PDF converter tool have recently been flagged online. ESET research recently shared images of the fake pages on Twitter. Bleeping Computer spoke with ESET's head of threat detection labs to gain more insight on the attacks. The attacks work by using fake advertising to highlight pages containing malicious software disguised as genuine applications.
One example is the fake Microsoft Store app listing shown below. The listing claims to be for an online chess app. According to BleepingComputer, if you try to download it, you'll instead get a zip file named 'xChess_v.709.zip." The file is actually a piece of information-stealing malware known as "Ficker" or "FickerStealer." The same strategy is used with a fake Spotify page as well as a fake PDF converter page.
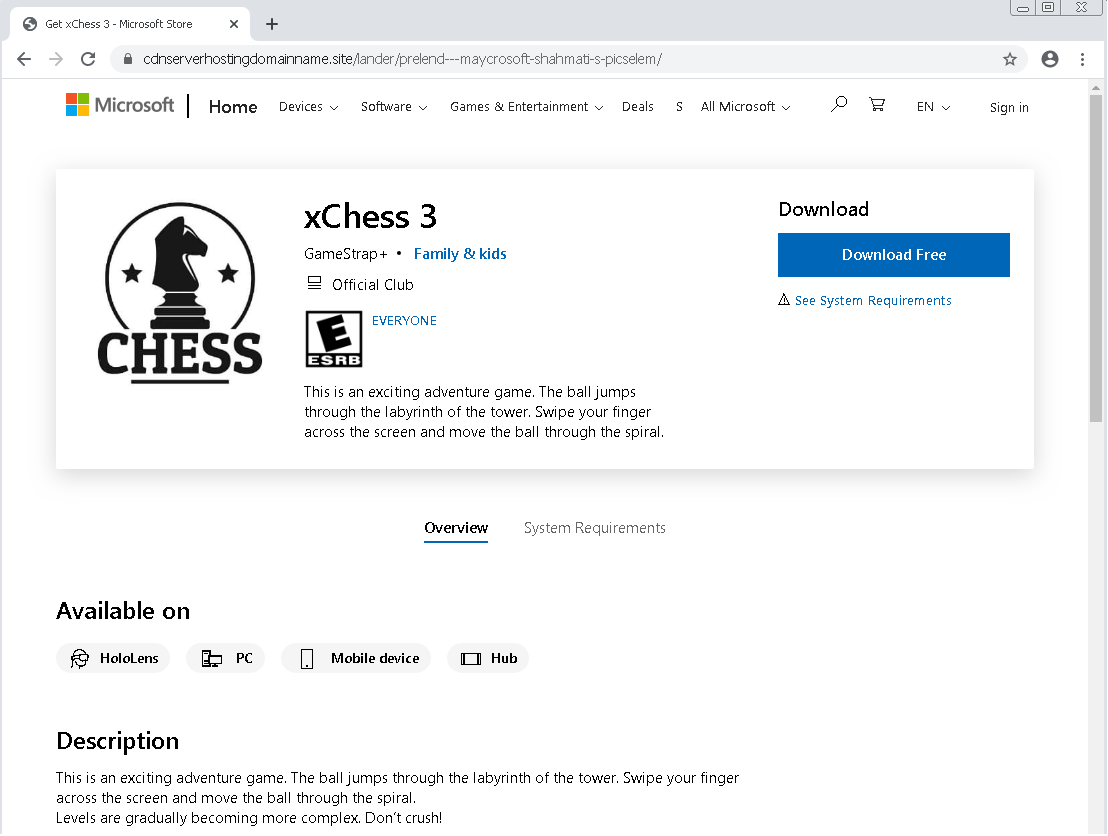
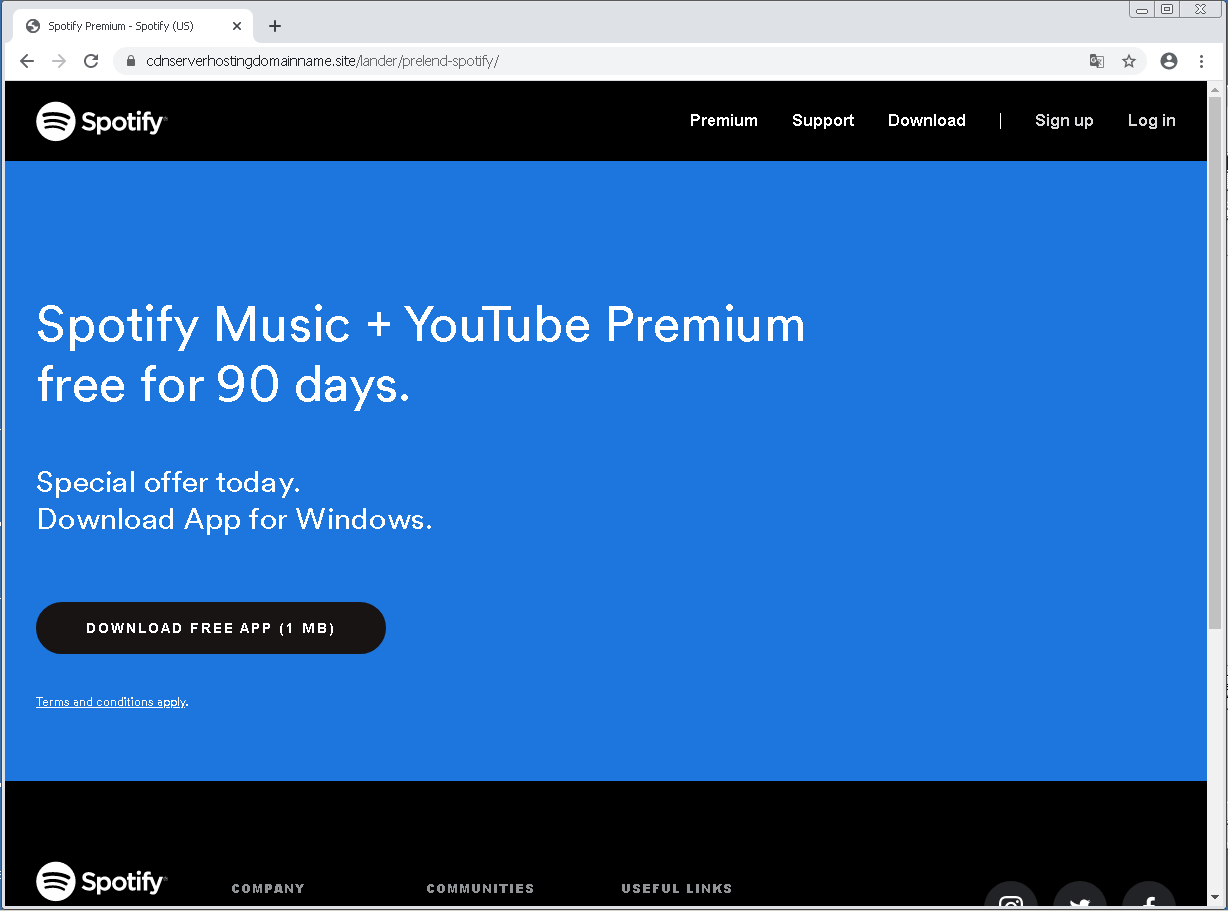
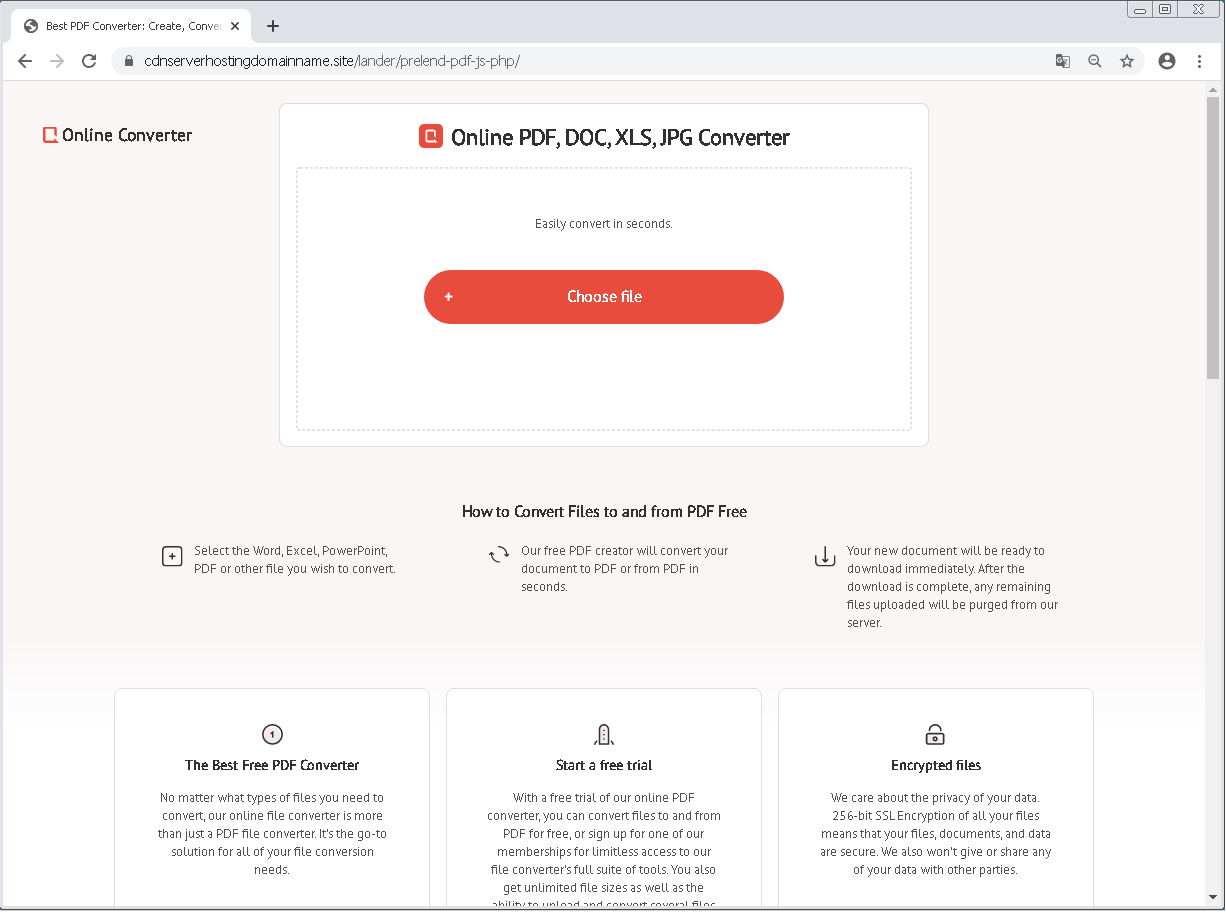
According to ESET research, the attacks are targeting countries in South America.
With the malware utilized in these attacks, threat actors can steal credentials saved within web browsers, messaging clients, and FTP clients. The malware can also steal over 15 cryptocurrency wallets, steal documents, and take screenshots of which apps are active on someone's PC. This valuable information is then sent back to the attacker.
When browsing the web, you should always double-check the URL of any sites you download applications from. If your PC has been attacked, you should scan for malware and change your passwords. You may also want to pick up the best antivirus software to help secure your PC.
All the latest news, reviews, and guides for Windows and Xbox diehards.

Sean Endicott is a news writer and apps editor for Windows Central with 11+ years of experience. A Nottingham Trent journalism graduate, Sean has covered the industry’s arc from the Lumia era to the launch of Windows 11 and generative AI. Having started at Thrifter, he uses his expertise in price tracking to help readers find genuine hardware value.
Beyond tech news, Sean is a UK sports media pioneer. In 2017, he became one of the first to stream via smartphone and is an expert in AP Capture systems. A tech-forward coach, he was named 2024 BAFA Youth Coach of the Year. He is focused on using technology—from AI to Clipchamp—to gain a practical edge.
