From a Bill Gates memo to an industry practice: The story of Security Development Lifecycle

All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
Most people would agree that Microsoft has come a long way from the dark days of frequent malware attacks and security flaws making headlines. Microsoft has now shared the untold, and thrilling, story of the Security Development Lifecycle at SDLstory.com with anecdotes of the early days, and never-before-seen video footage and photos of the key players.
While in the earliest days, hacking was just an underground hobby, the media attention that security attacks received made it fascinating for cybercriminals as an opportunity for fame. The romanticism of breaking the web just because you could do it became a high. But as time went on, the attacks became more and more malicious, exploiting software for financial gain.
These vulnerabilities gained media attention while Microsoft was working on a reactive mode. Incidents like these were so significant that they strained the company’s ability to provide support to customers. And despite their security efforts, the company was losing the trust of customers.
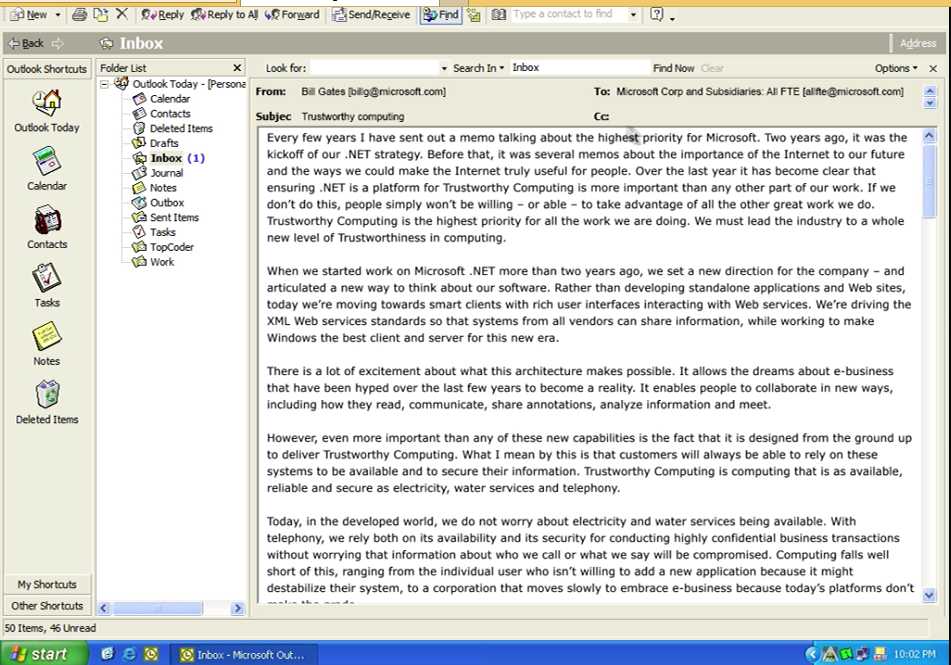
Within all this mess, Bill Gates sent a landmark memo about software security and trust to all full-time Microsoft employees wherein he coined the phrase ‘Trustworthy Computing’.
“… if we don’t do this, people simply won’t be willing — or able — to take advantage of all the other great work we do. Trustworthy Computing is the highest priority."
Not long after the memo, in February 2002, the unthinkable happened. The entire Windows division shut down and diverted all of its developers to security. Everyone was given training to outline expectations and priorities — threat modeling, code reviews, available tools, penetration testing — all designed to modify the default behavior of the system to make it more secure.
Microsoft began reinventing itself as a more secure computing company, and right away there were good results. With new tools, new processes, and a new understanding of the security landscape, integrating security into product development was now a primary focus across Microsoft. And by late 2003, early versions of Microsoft’s SDL began to take shape.
Once SDL got approved by the senior leadership, it was mandated to be embedded into the development cycle, updated periodically, and applied to all products and online services that faced meaningful risk. The increased security of Microsoft’s own software has been dramatic, in part due to the emphasis on continuing to evolve over the past 10 years.
All the latest news, reviews, and guides for Windows and Xbox diehards.
Interestingly, the SDL has had a major impact on the broader industry as well. Early on, Microsoft decided to make the SDL’s tools, processes and guidance available free of charge to any organization that wanted to adapt it to their own business. As a result, the SDL has not only led to measurable improvements in the security and privacy of Microsoft’s software and services, but also to a fundamental shift in software development at many other companies. Two of the world’s largest technology companies, Adobe and Cisco, have adopted it.
Since its inception in 2004, and the external release of SDL tools and resources in 2008, Microsoft's SDL guidance has been downloaded more than 1 million times and reached more than 150 countries. From small developer shops to large enterprises, many are seeing benefits from a ‘baking security in’ approach. The SDL was built on the concept that security should not be an afterthought.
Source: SDL Story

Abhishek is a Former Contributor for Windows Central, covering Windows Phone and more.
