Researchers bypassed Windows Hello, but you probably don't have to worry
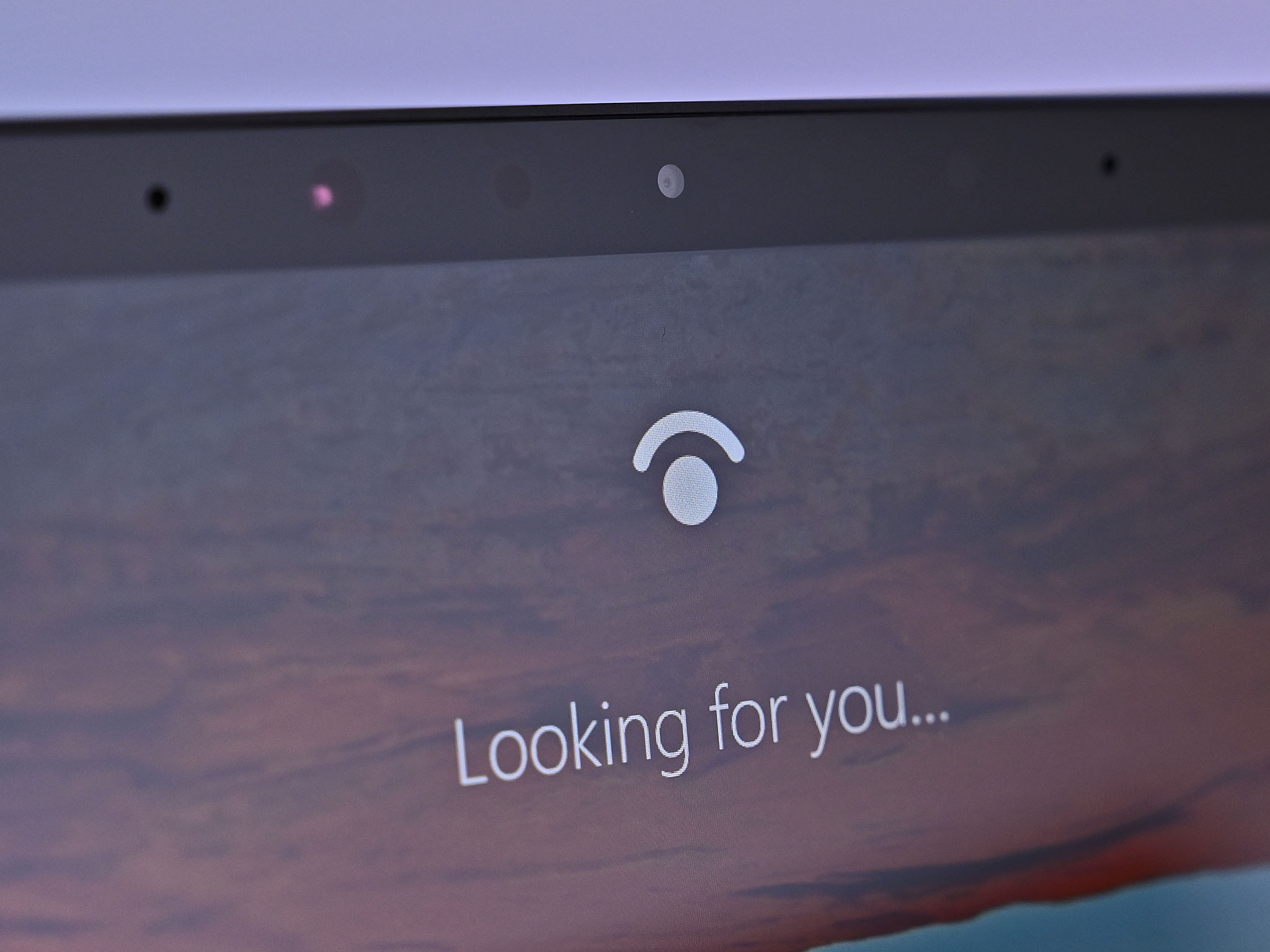
It's possible to bypass Windows Hello facial recognition, but it's complicated enough that most people shouldn't be concerned.
All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
What you need to know
- Researchers found a vulnerability that allows attackers to bypass Windows Hello facial recognition.
- Attacking through the vulnerability requires a person to have an IR image of a target, physical access to a target device, and a specialized piece of USB hardware.
- There's no evidence that this vulnerability has been taken advantage of in the wild.
A group of researchers from CyberArk Labs managed to bypass Windows Hello using a recently discovered vulnerability. CyberArk refers to the vulnerability as a "design flaw" that lets an attacker bypass Windows Hello facial recognition.
In practice, this vulnerability probably isn't much of a concern for most people. In order to take advantage of it, an attacker would need to have an IR image of a target's face, physical access to a potential victim's PC, and have a specialized piece of USB hardware.
Cyberark doesn't have any evidence of attackers taking advantage of the vulnerability in the wild. This new research on Windows Hello focuses on Windows Hello for Business, but CyberArk notes that "potentially any authentication system that allows a pluggable third-party USB camera to act as biometric sensor could be susceptible to this attack without proper mitigation." It adds, however, that it has "not performed practical tests to verify this."
Cameras that support Windows Hello have two sensors, an RGB sensor for visible images and an IR sensor. According to CyberArk, Windows Hello only processes the IR camera frames during the authentication process.
CyberArk was able to bypass Windows Hello by creating a custom piece of USB hardware that transmitted IR frames of a target. Research found that only a single IR frame is required to get around Windows Hello, though an additional frame is needed, which can just be a black frame.
"To summarize what we've learned so far: We have seen that an attacker can create a custom-made USB device that Windows Hello will work with," said CyberArk. "The attacker controls the data that comes from this device. With only one valid IR frame of the target, the adversary can bypass the facial recognition mechanism of Windows Hello, resulting in a complete authentication bypass and potential access to all the victim's sensitive assets."
Microsoft shared a mitigation for the vulnerability on July 13, 2021. CyberArk will present its findings at Black Hat 2021 on August 4-5, 2021.
All the latest news, reviews, and guides for Windows and Xbox diehards.

Sean Endicott is a news writer and apps editor for Windows Central with 11+ years of experience. A Nottingham Trent journalism graduate, Sean has covered the industry’s arc from the Lumia era to the launch of Windows 11 and generative AI. Having started at Thrifter, he uses his expertise in price tracking to help readers find genuine hardware value.
Beyond tech news, Sean is a UK sports media pioneer. In 2017, he became one of the first to stream via smartphone and is an expert in AP Capture systems. A tech-forward coach, he was named 2024 BAFA Youth Coach of the Year. He is focused on using technology—from AI to Clipchamp—to gain a practical edge.