'WannaCry' ransomware: Everything you need to know
One of the biggest cyber attacks in recent days has affected countries all around the world. Here's what you need to know.

All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
It's almost impossible to have missed the news about the global ransomware attack known as "WannaCry." This malicious program has been locking out access to PCs across the globe and demanding Bitcoin payments in order to decrypt the files on the computer.
Attacks of this scale are scary, especially when large organizations such as the British National Health Service (NHS) and one of Spain's largest telecoms providers are among the victims.
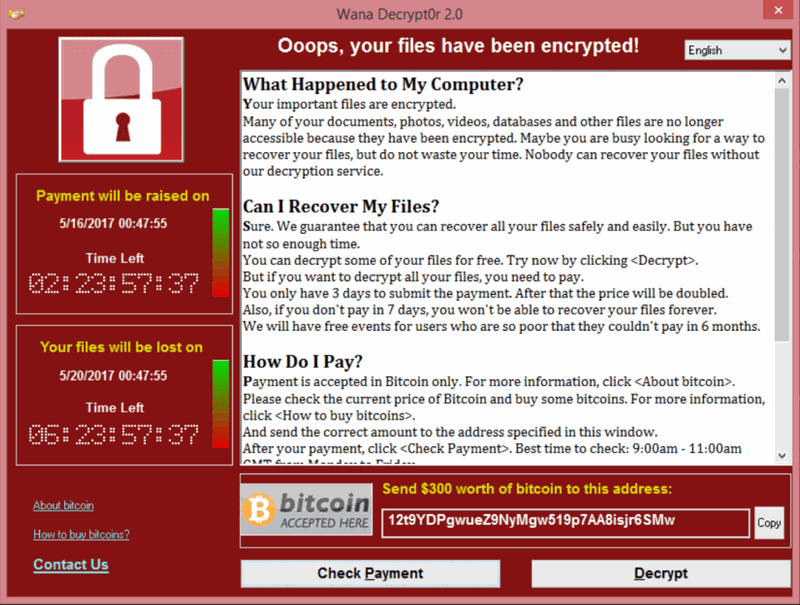
Let's break down some of the facts.
What is WannaCry?
WannaCry is a piece of ransomware that infects computers with the intent of monetary extortion in return for access to the contents of the PCs. It encrypts files, claiming only to let you back in upon receipt of the ransom.
Which platforms does it affect?
So far it only affects Windows systems, with the most well-known target being organizations that are still using Windows XP. WannaCry utilizes an exploit in Windows to get in. The exploits are reportedly ones which were stolen from the U.S. National Security Agency (NSA). The currently supported versions of Windows were quickly patched following the theft, but XP was not.
Microsoft's March 2017 MS17-010 security update is where the necessary patches have been compiled.
How big of an attack is it?
According to European authorities, as many as 10,000 organizations and 200,000 individuals were affected in more than 150 countries. It is being described as unprecedented on a global scale.
All the latest news, reviews, and guides for Windows and Xbox diehards.
How much is the ransom?
Right now, $300 in Bitcoin.
How is it infecting computers?
The underlying tool is believed to be the EternalBlue program developed first by American security services and subsquently leaked. A quick definition on how it spreads is such:
The ransomware is using a known, publicly disclosed exploit in SMBv1 (Server Message Block Version 1). It is an application level protocol used for sharing files and printers in a networked environment.
With regards to clicking on suspect links, the advice always remains the same. Don't click on any links or open any files you may have doubts about. In this case it's not necessarily how you'd wind up with this particular ransomware, but there are plenty of others out there that could be trying to get in this way.
If I get hit, should I pay the ransom?
No way! Remember that these are criminals, and chances are you'll be both out of pocket and without your files if you pay. A British security expert explained why to the BBC:
Victims are also expected to contact the criminals for a key to unlock their files, said security expert Prof Alan Woodward from the University of Surrey."I very much doubt anyone would return your contact request, bearing in mind the attention that is now on this," he told the BBC. "If anyone pays this ransom they are more than likely going to send Bitcoin that will sit in an address for ever more. No point."
These people don't want to be found, so they're unlikely to do anything that would give authorities any kind of edge in tracking them down.
Am I at risk?
Sadly, we're always at some kind of risk on the internet. However, Microsoft stated early on that Windows 10 users, with Windows Update turned on and Windows Defender active, should be protected.
Microsoft spokesman says customers running free antivirus software and have Windows Updates enabled are protected from 'ransomware' attackMicrosoft spokesman says customers running free antivirus software and have Windows Updates enabled are protected from 'ransomware' attack— Sky News Newsdesk (@SkyNewsBreak) May 12, 2017May 12, 2017
If you don't have your updates turned on, then that's a good place to start.
How do you get the files back?
Right now there's not a lot suggesting the files will ever be accessible again. If you don't have a backup, you might have lost your stuff. Good practice is to always back up your important files.
Can you repair your computer?
The folks at Bleeping Computer have a detailed guide. It's not the easiest thing to do, but if you've no alternative then it's worth a look.
Is Microsoft doing anything to help?
Yes. Despite it not really being Microsoft's fault, especially for anyone using the aging Windows XP in 2017, Redmond is jumping in to assist. Official support for XP has long since ended, but Microsoft issued a patch for the OS to try and keep WannaCry at bay. Its success, of course, is dependent on being installed on a non-infected system.
I heard someone cracked it?
A cybersecurity researcher from the UK "accidentally" found a way to slow down the spread of the attack by stumbling upon a so-called "kill switch."
I will confess that I was unaware registering the domain would stop the malware until after i registered it, so initially it was accidental.I will confess that I was unaware registering the domain would stop the malware until after i registered it, so initially it was accidental.— MalwareTech (@MalwareTechBlog) May 13, 2017May 13, 2017
In the simplest form, a domain was found inside the code of the WannaCry program, and by registering this domain it had a dramatic effect, as described to The Guardian:
The kill switch was hardcoded into the malware in case the creator wanted to stop it spreading. This involved a very long nonsensical domain name that the malware makes a request to – just as if it was looking up any website – and if the request comes back and shows that the domain is live, the kill switch takes effect and the malware stops spreading. The domain cost $10.69 and was immediately registering thousands of connections every second.
As long as the domain isn't revoked, the initial strain of WannaCry should begin to fade away. But that's no substitute for making sure your systems are up to date with all the latest patches.
Is it over yet?
The biggest fear over the weekend was that as many returned to work and turned on their machines, a whole new raft of infections would occur. Thankfully, new cases have slowed significantly, and many of the affected have been working to clear the threat since it first emerged.
The NHS in the UK was one of the more high-profile casualties, and while the majority of affected trusts have had the issue resolved, there are still seven suffering the effects going into the new work week.
The warnings are that there will probably be another attempt at an attack, as well.
Your thoughts
That's a quick overview of where things stand right now, but it's an ever-changing situation. We'll do our best to keep on top of the latest details. And if you have anything helpful to share, be sure to leave it in the comments below.

Richard Devine is the Managing Editor at Windows Central with over a decade of experience. A former Project Manager and long-term tech addict, he joined Mobile Nations in 2011 and has been found in the past on Android Central as well as Windows Central. Currently, you'll find him steering the site's coverage of all manner of PC hardware and reviews. Find him on Mastodon at mstdn.social/@richdevine
