What is S/MIME and should you use it for email on Windows Phone?

All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
No matter how technically savvy you consider yourself to be, there's always a good chance you will come across something that you just don't know anything about. For instance, a few of us at Windows Central were chatting online, and someone asked what S/MIME is and whether they should enable in their email settings on their Windows phone.
Having worked in IT for a number of years, I had heard the term S/MIME before. However, I didn't know nearly enough about it to answer the questions. Immediately, we all agreed that it was a good idea for a post. What you now have before you is an attempt to explain what S/MIME is and help guide you in deciding if it is something you should use on your Windows phone.
You may or may not have the option to use S/MIME with your email. If you have a Hotmail or Outlook account on your phone, the option will appear in the Settings section of your email account.
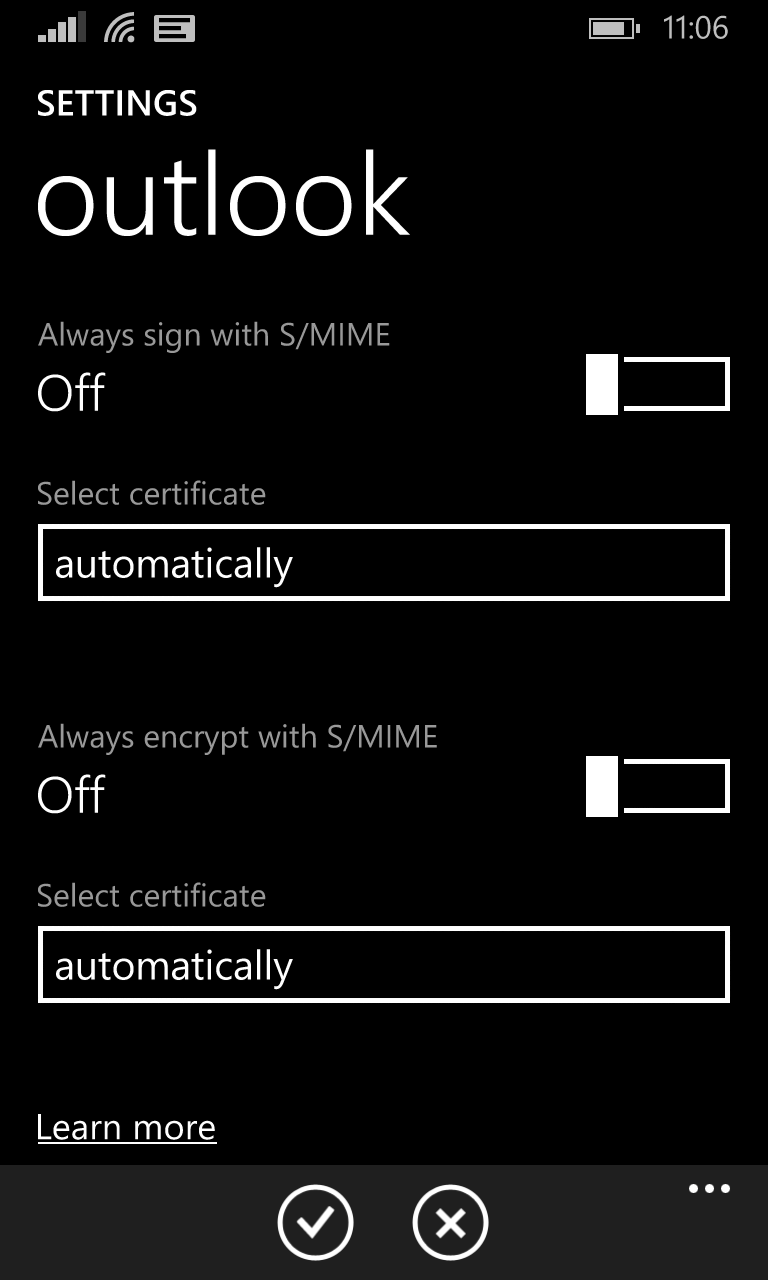
Google and Yahoo accounts do not have these options on Windows Phone. If you are using a business email address through your employer, your IT administrator will tell you whether or not you need to use it.
What is it?
S/MIME stands for Secure/Multipurpose Internet Mail Extensions. To put it simply, it is a universal standard for securely signing and encrypting email. It is essentially used to prove that the email came from the person says it is from.
It works using a unique certificate, a fingerprint of sorts, issued by a third party. That certificate gets recorded in a database, be it a private company's server or a public registry on the internet. When an email is sent using S/MIME, it gets stamped with that digital signature. When the recipient receives the message, the signature gets checked against the sender information to validate that it indeed came from the person it claims to be from.
That same certificate can be used to encrypt email to avoid a third-party from viewing it. Much like encryption programs like PGP, the email gets encrypted using a "public key" derived from the user's digital certificate and a password. Once sent, the recipient uses their "private key," derived the same way, to decrypt the message to make it readable.
All the latest news, reviews, and guides for Windows and Xbox diehards.
While identity validation is always part of a message sent using S/MIME, message encryption is optional.
Is it safe?
Since it was developed to be a universal standard of encryption, S/MIME has been put through its paces to ensure that it is an effective method of securing data. However, that same universality makes it a target as well. Finding a way to crack S/MIME would mean gaining access to an untold wealth of information.
However, there is good news. Firstly, in my (albeit limited) research, I could not find any record of S/MIME being breached. Private/public key-based encryption is difficult to crack by its very nature. That doesn't mean that the NSA hasn't secretly found a way to do it though.
Secondly, the forces behind S/MIME have improved it over time. It is currently in its third iteration, which has added measures of protection. There is no sign of that stopping anytime soon.

What's the downside?
Using S/MIME will indeed affect your current email routine, mostly in the form of some occasional added legwork. First and foremost, because it requires validation from a third party, you must obtain a certificate through a Certification Authority. There are many out there that provide certificates free of charge. The certificate expires, usually every year, so you also need to make sure you renew it.
If you are only using the digital signing feature of S/MIME, there isn't too much downside. A recipient who has S/MIME setup will get verification that you are the legitimate sender of the email. If they or their email provider do not use S/MIME, then they will likely see an attachment on your message named smime.p7s. This lack of support will not cause any issues, other than possible confusion on the part of the recipient.
This scenario is especially common with people who use web-based email services, like Gmail and Yahoo and access their mail from a web browser. If the account is accessed using an email application, like Microsoft Outlook, the S/MIME typically gets decoded correctly.
And if it doesn't, it's not a big deal because the email was sent in plain text. The recipient just can't be sure that you are the actual sender.
As far as encryption goes, there is some more added hoops. Encrypting an email requires that the person on the other end also uses it. Therefore, if you want them to be able decrypt your message that uses your private key, they must have your public key. Otherwise, they just get a garbled mess of an email.
Encrypting a message also adds data to that message, increasing the overall size of it. S/MIME encryption typically triples the size of your message. Given that most emails are pretty small, it shouldn't affect you too much. However, it should be taken into consideration when using S/MIME a lot, as it can pile up on a device with limited storage.
Also keep in mind that encrypting email not only keeps out the bad guys, but the good guys too. Attachments in encrypted emails cannot be scanned by anti-malware services, leaving you unprotected until opening them.
Sounds like a good idea. Should I use it?
For the overwhelming majority of ordinary users, there is no need to sign or encrypt our everyday email. Any email provider worth its salt uses SSL encryption to transmit data, so you are reasonably protected.
Even if we are sending sensitive information, like tax documents or health records, we may find it easier to password protect the documents or combine them into a password protected ZIP file. This situation is also one of the last places on Earth that fax machines are still useful.
That being said we are living in a world where more and more data breaches occur every day. If you feel so inclined, S/MIME can help protect your information and maintain your privacy.
So why the heck is it even an option?
In a word, business. Microsoft is in the business of business and knows that if Windows Phone is going to have any chance in the smartphone wars it is going to have to accommodate enterprise users and technology.
S/MIME is a common component of corporate email, so Windows Phone needs to take that into consideration.
In Summary
S/MIME has been a universal standard in securing email for very long time, and rightfully so. But most of its usages has been in the business world, not the public realm. Implementing it for your personal email is not overly complicated, but does present its challenges.
In the end, it's up to you to decide how useful it would be to you.
Have any of you implemented S/MIME in your personal routine? What is your experience?
References: Wikipedia, Microsoft, Mozilla, JustinRummel.com

Seth Brodeur is a former contributor for Windows Central, covering Windows 10, Windows Phone, and more.
