Microsoft explains unusual phishing campaign that uses Morse code
A complex phishing campaign uses Morse code and segmented components to bypass security.

All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
What you need to know
- Microsoft breaks down a unique phishing campaign that uses a mixture of new and old encoding methods.
- The campaign uses Morse code to encode links to avoid detection.
- Microsoft compares the phishing attack to a jigsaw puzzle because its components are separated to bypass normal security methods.
Microsoft details how an unusual phishing campaign works in a new security post. As is the case with many phishing campaigns, its goal is to get people's usernames, passwords, and other valuable information. Unlike other campaigns, this new attack uses a combination of new encoding methods and Morse code.
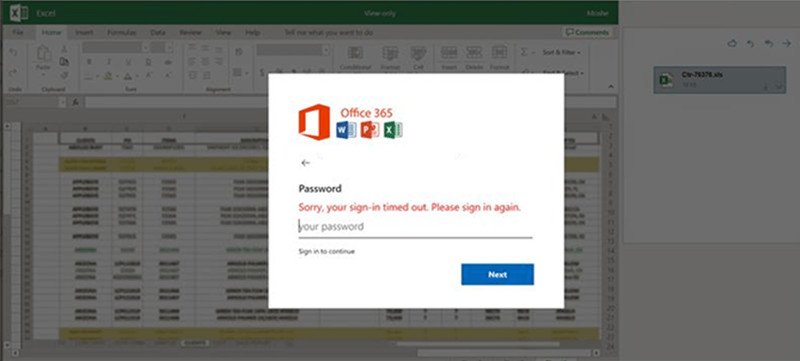
The campaign aims to have people download an XLS attachment, which most people would assume is an Excel file. Instead, opening the file will launch a browser to a fake login screen for what appears to be Microsoft 365. The credentials screen will show a Microsoft logo and in some cases the company logo of a potential victim.
If someone enters their password, they'll be told that the information is incorrect (regardless of its validity). Then, the attacker obtains the victim's password.
The phishing campaign is sophisticated in a few key ways. First, its components are separated into pieces. Second, those pieces are encoded with a mixture of old and new techniques, including Morse code. Lastly, some of the segments aren't in the file attachment that the campaign utilizes. They're in open directories that can be called on by encoded scripts.
Microsoft compares how the campaign works to a puzzle:
In effect, the attachment is comparable to a jigsaw puzzle: on their own, the individual segments of the HMTL file may appear harmless at the code level and may thus slip past conventional security solutions. Only when these segments are put together and properly decoded does the malicious intent show.
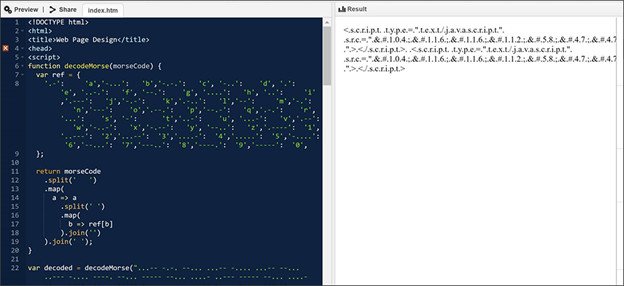
The use of Morse code is a unique way to attempt to have the phishing campaign go undetected. Microsoft explains how Morse code is used in conjunction with other encoding methods:
Morse code is an old and unusual method of encoding that uses dashes and dots to represent characters. This mechanism was observed in the February ("Organization report/invoice") and May 2021 ("Payroll") waves.In the February iteration, links to the JavaScript files were encoded using ASCII then in Morse code. Meanwhile in May, the domain name of the phishing kit URL was encoded in Escape before the entire HTML code was encoded using Morse code.
Microsoft's security post outlines several ways to stay protected from this newly discovered phishing attack, including using Microsoft Defender for Office 365. The company also explains ways to mitigate and detect the attack.
All the latest news, reviews, and guides for Windows and Xbox diehards.

Sean Endicott is a news writer and apps editor for Windows Central with 11+ years of experience. A Nottingham Trent journalism graduate, Sean has covered the industry’s arc from the Lumia era to the launch of Windows 11 and generative AI. Having started at Thrifter, he uses his expertise in price tracking to help readers find genuine hardware value.
Beyond tech news, Sean is a UK sports media pioneer. In 2017, he became one of the first to stream via smartphone and is an expert in AP Capture systems. A tech-forward coach, he was named 2024 BAFA Youth Coach of the Year. He is focused on using technology—from AI to Clipchamp—to gain a practical edge.