Microsoft stops coronavirus-themed cybercrime with help of court order
Microsoft is combatting attacks aimed at tricking people who need help during the coronavirus pandemic.

All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
What you need to know
- Microsoft is combatting phishing attacks by seizing control of domains.
- The newest phishing attacks try to trick people with fake coronavirus-related emails.
- A recent court ruling allowed Microsoft to seize the domains utilized in the attacks.
Microsoft is combatting coronavirus-themed cybercrime by seizing control of domains used as part of the infrastructure of criminal attacks. During the coronavirus (COVID-19) pandemic, attackers have tried to take advantage of people by sending emails claiming to provide help or information related to coronavirus. Microsoft outlines its efforts in a recent blog post.
In addition to several defensive actions that Microsoft takes against these kinds of attacks, Microsoft also takes legal action when necessary. Microsoft recently filed a civil case, which resulted in a court order allowing Microsoft to seize control of key domains. By seizing these domains, Microsoft can make it more difficult for phishing emails to appear authentic.
In December 2019, Microsoft's Digital Crimes Unit (DCU) observed a new phishing scheme aimed at compromising people's Microsoft accounts. These attacks would send emails that appeared to be from Microsoft but were actually attackers maliciously using Microsoft branding and URLs that appear similar to Microsoft's official channels. According to Microsoft, the same criminals behind those attacks began a similar set of attacks that instead phished people with coronavirus-related emails.

For example, malicious emails were sent out with what appears to be an Excel spreadsheet titled "COVID-19 Bonus." The example (shown above) shared by Microsoft appears authentic, as it has the URL "@sharepointonline.com" for the sender and features copied Microsoft OneDrive branding.
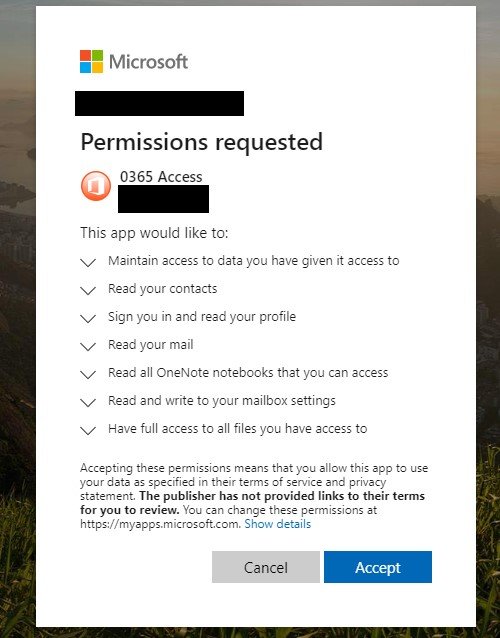
If a person clicks on the deceptive links within the phishing email, they're prompted to grant access to a malicious web application. Microsoft emphasizes that web apps are used frequently by organizations, which means that people could be used to granting them permissions. The malicious web apps would then be able to access people's Microsoft Office 365 account. The prompt (shown below) asks people to grant access to several sensitive pieces of data. The prompt has a copied Microsoft logo and an icon labelled "0365" that appears similar to Microsoft's Office icon.
This type of attack is known as a business email compromise (BEC) attack. According to the FBI's 2019 cybercrime report, BEC attacks cost people over $1.7 billion (via Neowin).
Microsoft lays out some steps that people and businesses can take to further protect themselves from attacks. The company recommends two-factor authentication, learning how to spot phishing schemes, and enabling security alerts for links and files from suspicious websites. Microsoft also recommends checking email forwarding rules for suspicious activity.
All the latest news, reviews, and guides for Windows and Xbox diehards.

Sean Endicott is a news writer and apps editor for Windows Central with 11+ years of experience. A Nottingham Trent journalism graduate, Sean has covered the industry’s arc from the Lumia era to the launch of Windows 11 and generative AI. Having started at Thrifter, he uses his expertise in price tracking to help readers find genuine hardware value.
Beyond tech news, Sean is a UK sports media pioneer. In 2017, he became one of the first to stream via smartphone and is an expert in AP Capture systems. A tech-forward coach, he was named 2024 BAFA Youth Coach of the Year. He is focused on using technology—from AI to Clipchamp—to gain a practical edge.