Windows is a ransomware magnet, according to a new VirusTotal report
Ransomware likes Windows — a lot.

All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
What you need to know
- VirusTotal released a report on ransomware activity.
- It's loaded with statistics on ransomware, including freshness of attack samples, attack volume figures, and which operating systems are getting hit the most.
- Windows was the target for 95% of the ransomware files VirusTotal evaluated in its October 2021 report.
Ransomware is becoming a bigger and bigger deal by the day. The U.S. government is focusing energies on cryptocurrency sanctions in large part to combat ransomware. The attack type has been at the core of national incidents. And now, there's a report on how the ever-expanding problem links back to Windows.
Based on the ransomware files VirusTotal analyzed for its October 2021 report, 95% of all of them are for Windows PCs. A hair over 2% go after Android, and every target of ransomware beyond those two makes up a micro percentage of the overall pie.
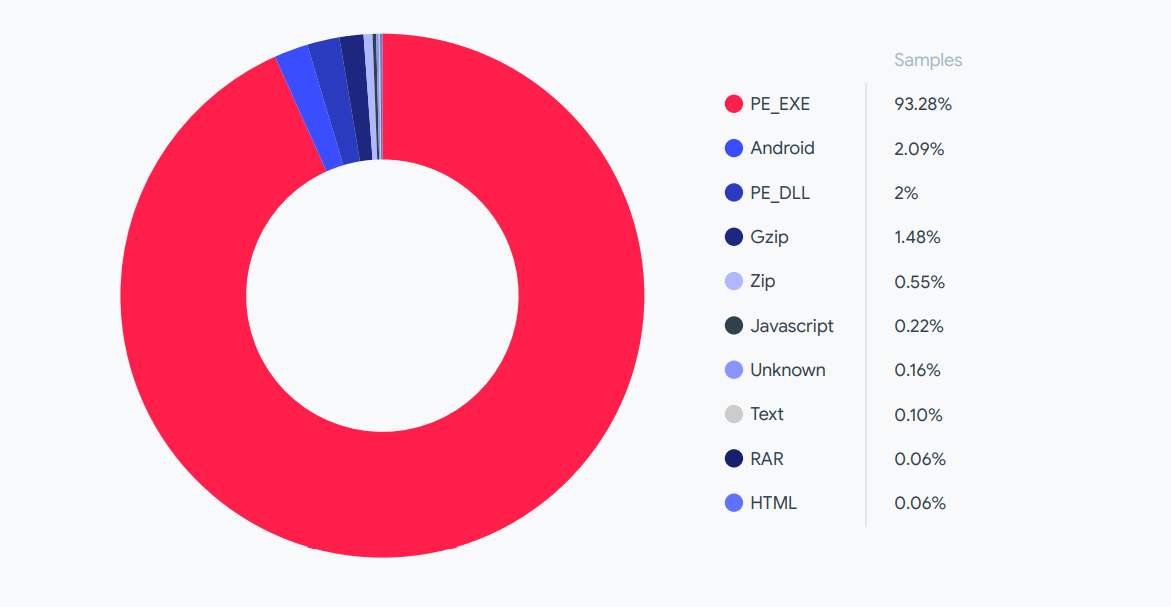
The report goes over loads of other ransomware statistics if you want to find out which countries are the most targeted by the threat (spoiler: Israel saw a big increase in attacks in 2021), how often new families of the software type are cropping up, and more.
This news may or may not come as a surprise to Windows users who constantly see reports of ransomware. Recently, there was LockFile, which targeted Microsoft Exchange servers. There was even the threat of ransomware when it came to basic Windows-based printing activities.
The threat isn't going away anytime soon, hence why it's even now being addressed by Microsoft in an insurance capacity. As the years stretch on, we may see more and more measures being taken by companies and governments to combat the form of cybercrime. Until then, take precautions to not get swept up in the growing ransomware storm.
All the latest news, reviews, and guides for Windows and Xbox diehards.

Robert Carnevale was formerly a News Editor for Windows Central. He's a big fan of Kinect (it lives on in his heart), Sonic the Hedgehog, and the legendary intersection of those two titans, Sonic Free Riders. He is the author of Cold War 2395.
