38 million records exposed, Microsoft Power Apps blamed
Social security numbers, vaccination statuses, and other sensitive pieces of data were left publicly accessible.

All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
What you need to know
- The default settings of Microsoft's Power Apps were blamed for 38 million records being exposed.
- Leaked data includes Social Security numbers, COVID-19 vaccination statuses, and other pieces of sensitive information.
- Microsoft has since changed its default settings for Power Apps.
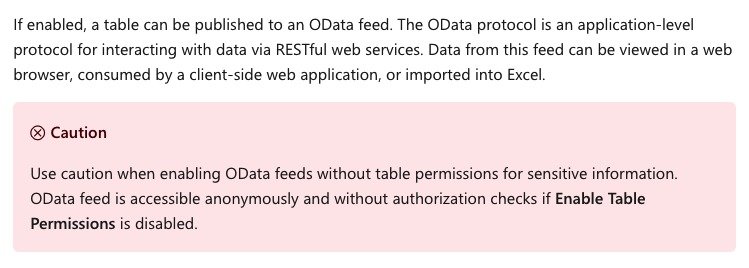
Thousands of web apps left sensitive data exposed online due to misconfigured settings for Microsoft Power Apps. Thirty-eight million records appeared online, including social security numbers, COVID-19 vaccination statuses, home addresses, and phone numbers. American Airlines, J.B. Hunt, Microsoft, and several government bodies are among the affected organizations. UpGuard notified 47 entities regarding the data exposure and reached out to Microsoft about it as well (via WIRED).
The data leaks came as a result of organizations using Microsoft's Power Apps. These can be used to create websites and to manage data, but if misconfigured can result in security risks. Power Apps can be used to manage data that organizations would like to have public, such as the locations of vaccination centers, as well as data that should remain private, such as Social Security numbers. The default settings for Power Apps left data publicly accessible until a recent change from Microsoft.
While Microsoft's service listed the implications of these settings, they were not made clear, according to UpGuard:
The number of accounts exposing sensitive information, however, indicates that the risk of this feature– the likelihood and impact of its misconfiguration– has not been adequately appreciated. On one hand, the product documentation accurately describes what happens if an app is configured in this way. On the other hand, empirical evidence suggests a warning in the technical documentation is not sufficient to avoid the serious consequences of misconfiguring OData list feeds for Power Apps portals.
Microsoft has since enabled table permissions by default. The company has also provided a tool to help Power Apps users diagnose the security of their portals.
Upguard summarizes its thoughts and findings, which spreads blame across multiple parties:
While we understand (and agree with) Microsoft's position that the issue here is not strictly a software vulnerability, it is a platform issue that requires code changes to the product, and thus should go in the same workstream as vulnerabilities. It is a better resolution to change the product in response to observed user behaviors than to label systemic loss of data confidentiality an end user misconfiguration, allowing the problem to persist and exposing end users to the cybersecurity risk of a data breach.
Upguard also states that "Microsoft has done the best thing they can" by switching to enable table permissions by default and providing a diagnostic tool for users.
All the latest news, reviews, and guides for Windows and Xbox diehards.

Sean Endicott is a news writer and apps editor for Windows Central with 11+ years of experience. A Nottingham Trent journalism graduate, Sean has covered the industry’s arc from the Lumia era to the launch of Windows 11 and generative AI. Having started at Thrifter, he uses his expertise in price tracking to help readers find genuine hardware value.
Beyond tech news, Sean is a UK sports media pioneer. In 2017, he became one of the first to stream via smartphone and is an expert in AP Capture systems. A tech-forward coach, he was named 2024 BAFA Youth Coach of the Year. He is focused on using technology—from AI to Clipchamp—to gain a practical edge.