Tricky phishing attack targets Microsoft Teams users — here's how to protect yourself
Between 15,000 and 50,000 inboxes were targeted by a new phishing attack as of last Friday.
All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
What you need to know
- A new phishing attack uses cloned Microsoft imagery to trick people into giving away their Office 365 login details.
- The attack imitates file share and audio notification emails from Microsoft Teams.
- The attack uses several URL redirects that take people to a convincing fake login page.
A new phishing attack was discovered toward the end of last week that aims to steal people's Office 365 login details. The attack used cloned imagery to send convincing emails that pretends to be Microsoft Teams notifications. Clicking on links within the emails goes through several URL redirects to cover up the attack and ends up on a realistic fake Office 365 login page. The page asks people to log in to their Office 365 account, but actually just steals people's login details. Abnormal Security first discovered and reported on the attack.
The phishing attack is particularly dangerous because millions of people are using Microsoft Teams for the first time due to the current global health crisis. With Microsoft Teams reaching 75 million daily active users recently, tens of millions of people are using the service for the first time. As a result, many people won't be familiar with what types of notifications the service sends out. Even if someone is familiar with Microsoft Teams, the phishing attack uses cloned imagery from Microsoft that is convincing.
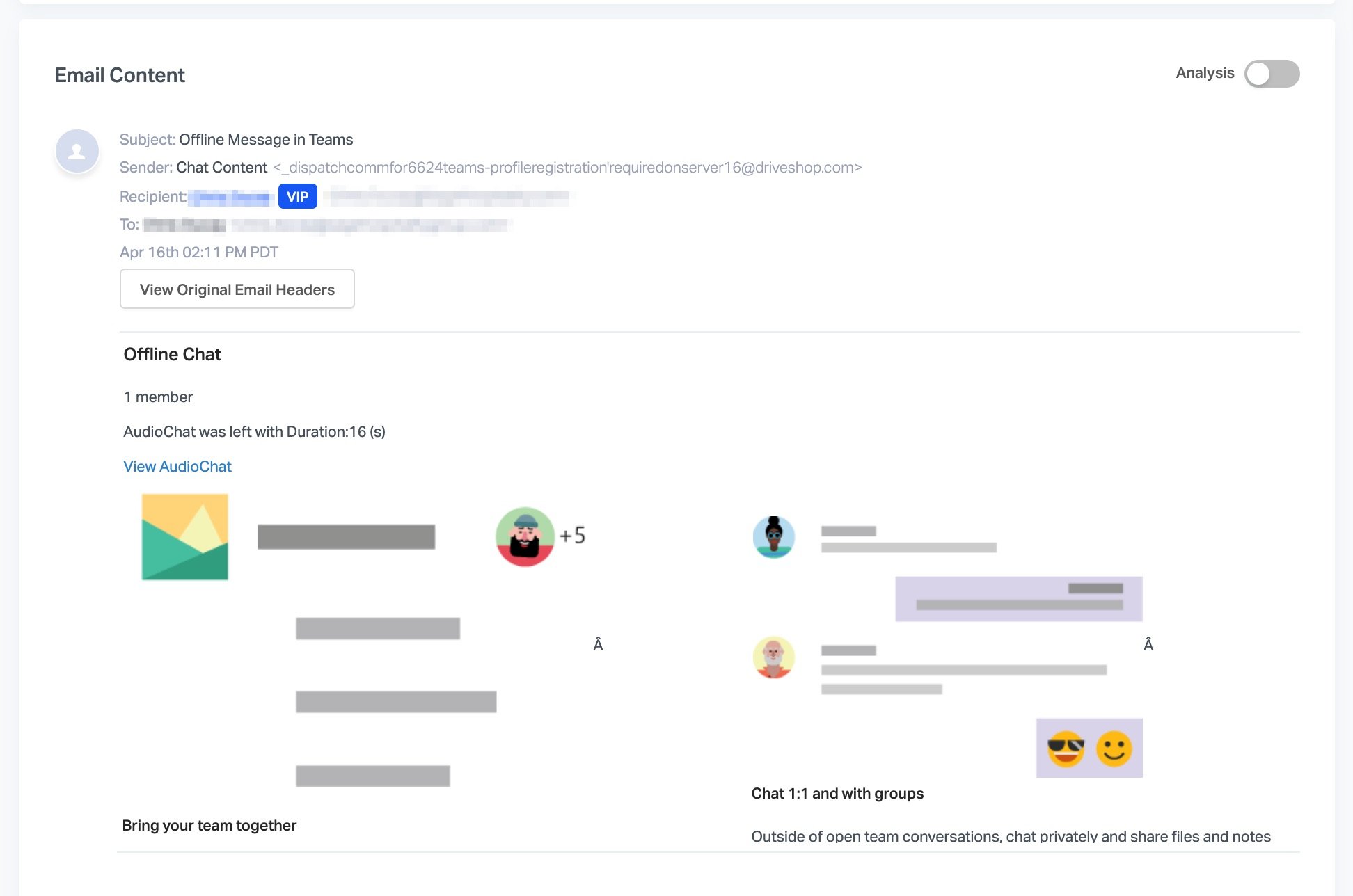
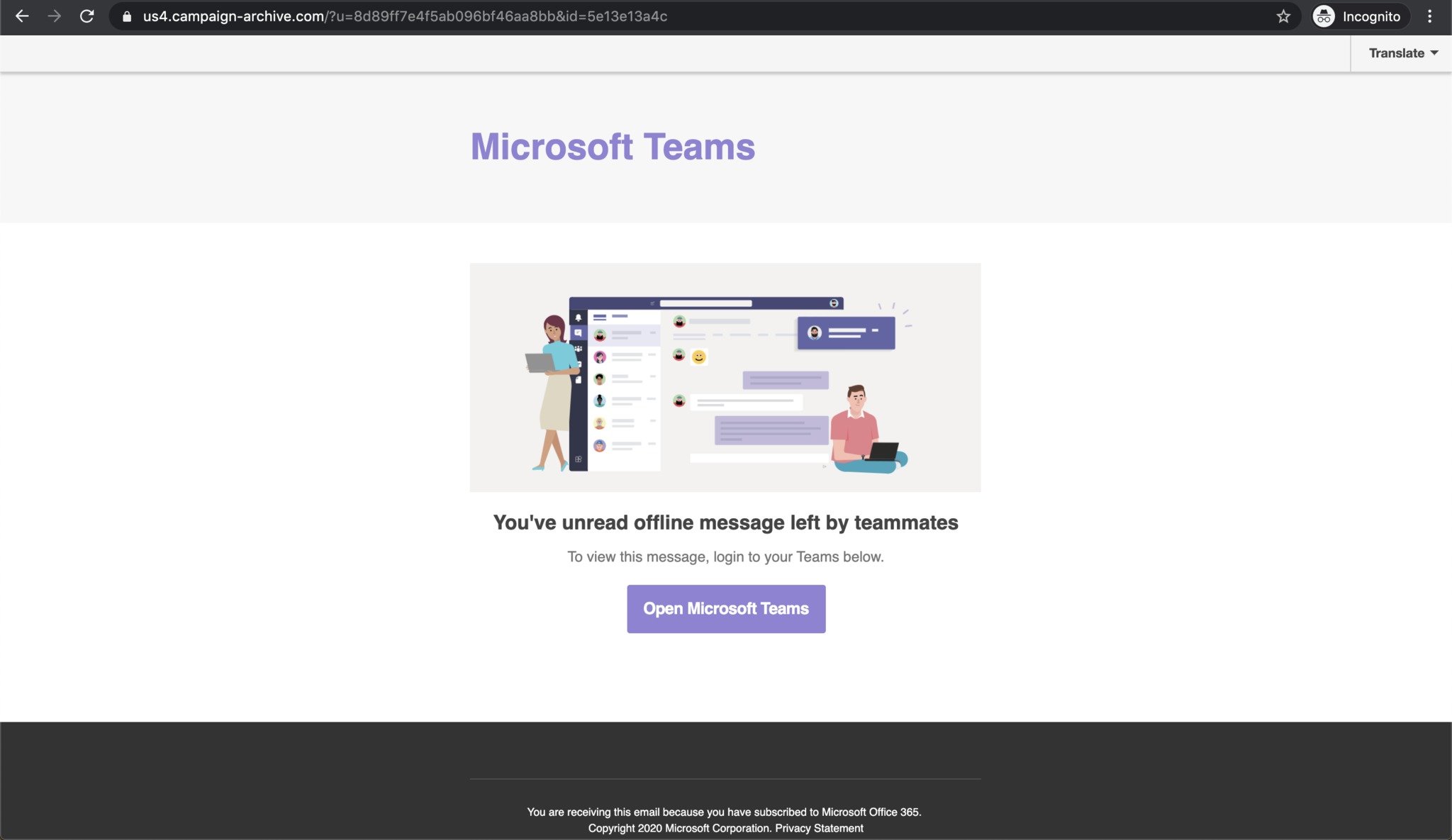
Abnormal Security summarizes how convincing images and URL redirects create an effective attack:
The email and landing page the attackers created were convincing. The webpages and the links the email direct to are visually identical to legitimate Microsoft Teams and Microsoft login pages. Recipients would be hard-pressed to understand that these sites were set up to misdirect and deceive them to steal their credentials.
On May 1, 2020, Abnormal Security reported that between 15,000 and 50,000 inboxes received emails as part of the phishing attack. Abnormal Security highlights that because Microsoft Teams is linked to Office 365, a successful phishing attack on a person's Microsoft Teams account could also grant access to people's Office 365 account. The firm states, "Additionally, since Microsoft Teams is linked to Microsoft Office 365, the attacker may have access to other information available with the user's Microsoft credentials via single-sign on."
To keep yourself protected, make sure the check the URL and source of emails and websites. For example, one attack comes from an email attache to "sharepointonline-irs.com." That website is not affiliated with Microsoft or the IRS. Some of the other URLs used look less convincing, but you should always keep an eye out when clicking on links as some might have URLs that seem reasonable.
All the latest news, reviews, and guides for Windows and Xbox diehards.

Sean Endicott is a news writer and apps editor for Windows Central with 11+ years of experience. A Nottingham Trent journalism graduate, Sean has covered the industry’s arc from the Lumia era to the launch of Windows 11 and generative AI. Having started at Thrifter, he uses his expertise in price tracking to help readers find genuine hardware value.
Beyond tech news, Sean is a UK sports media pioneer. In 2017, he became one of the first to stream via smartphone and is an expert in AP Capture systems. A tech-forward coach, he was named 2024 BAFA Youth Coach of the Year. He is focused on using technology—from AI to Clipchamp—to gain a practical edge.
