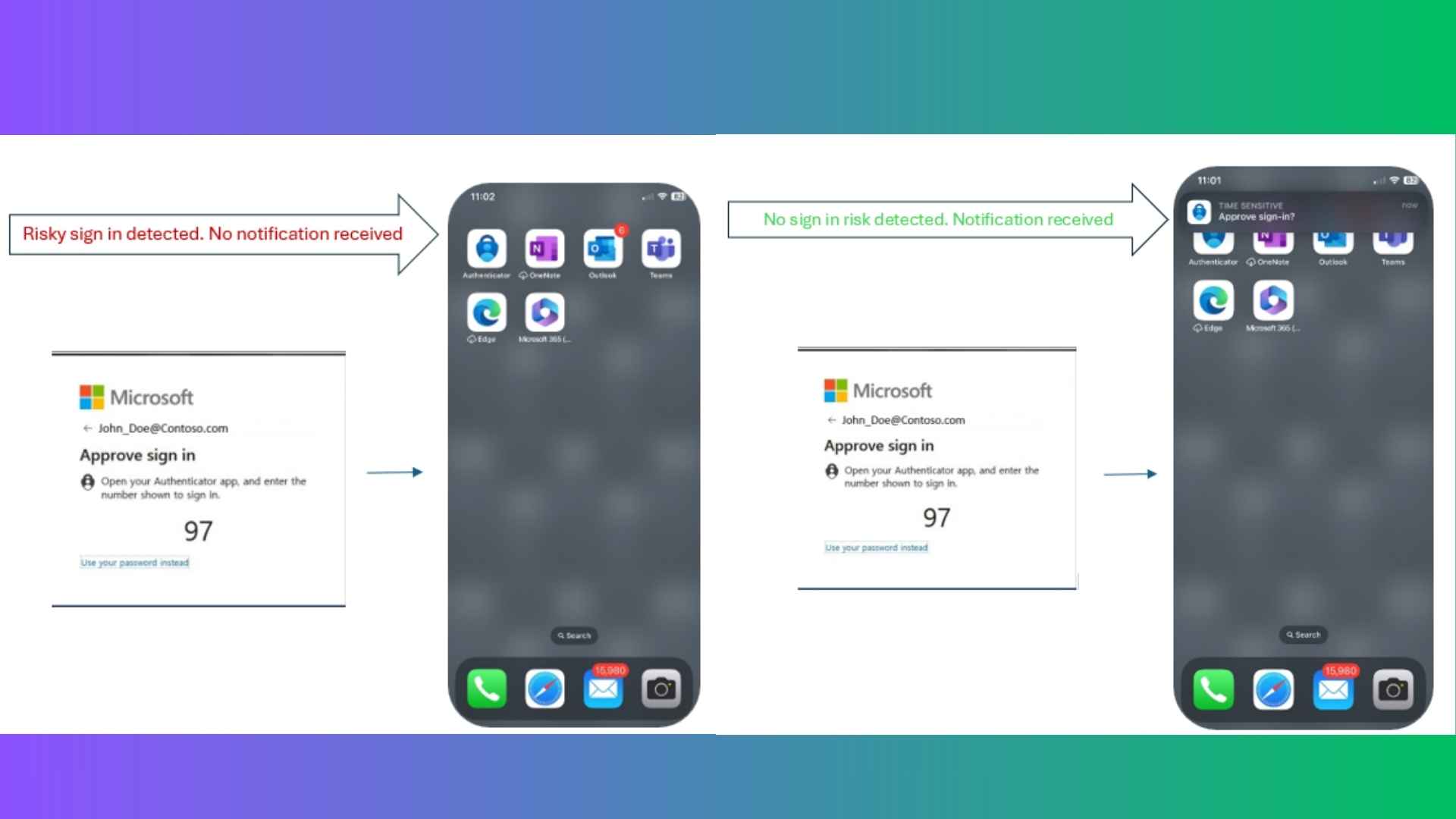
The Microsoft Authenticator app will suppress 'risky' notifications as Microsoft pushes for improved security
Microsoft Authenticator receives better security by default with this one new change.
All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
What you need to know
- Microsoft's Authenticator will now suppress notifications of suspicious logins.
- Attackers will repeatedly try to log in, giving users "MFA fatigue" due to so many notifications.
- If your company allows for simple MFA approval, this can lead to users allowing the MFA to make the notifications stop.
- This new policy by Microsoft will suppress notifications if they are from unconventional sources.
Microsoft Authenticator is a great app if you need MFA (and you do). If you don't know why MFA is necessary, let me break it down for you. Imagine your account or company's network is a house that can only be accessed through a front door. The front door has a handle with a place for a key but also has a deadbolt that doesn't have a key and must be opened from the inside. Only you can open that deadbolt granting access to the house. Your password is the key to unlock the door handle, and the MFA is the deadbolt. Anybody can steal your password or copy your key, but unless they get access to your physical MFA device (usually your phone), they can never gain access to your account or your company's network.
Unfortunately, MFA security is lacking, especially in big companies, as Microsoft's Alex Weinart points out in this post.
"We‘ve repeatedly emphasized the importance of multifactor authentication (MFA) and emphasized that not all MFA is equal – the Authenticator is much more secure than phone authentication (so hang up!)
Alex Weinart - Microsoft
Why is MFA important?
The "phone call" MFA method is notoriously one of the worst ways to MFA because all it takes is the user to press one button on their keypad to allow an attacker access to their entire company's network, and it is the best avenue for MFA bombing attacks. MFA bombing is when an attacker successfully compromises a user's credentials and begins attempting to log in repeatedly. Each time they do this, it sends an MFA prompt. If this was a notification on your Microsoft authenticator app, that would be annoying, but not nearly as annoying as getting a phone call repeatedly for what could be hours.
Unfortunately, some users will decide just to approve the MFA, whether it's an MFA prompt over the phone, SMS, or a notification through Microsoft Authenticator where they have to click "yes," it's me logging in. To be clear, if you have an MFA setup for either personal or business use and you receive an MFA prompt that you did not originate from when you log in, somebody has your password, and you should immediately reset it.
How is Microsoft improving the Authenticator app?
One of the most important things a company can do to remove any chance of an attacker successfully tricking a user into approving an MFA is to implement number matching, as explained in the Microsoft post. How this works is when you log in, a number will appear on the computer screen, and then in the Authenticator app, the user has to input that number. There is no guessing or multiple choice, and the user has no way of knowing the number the attacker has up on their screen.
However, this doesn't eliminate the issue of MFA fatigue, which is when somebody is getting malicious login attempts from a threat actor, they will continue to get notified by the authenticator app of the logins.
We now suppress Authenticator notifications when a request displays potential risks, such as when it originates from an unfamiliar location or is exhibiting other anomalies. This approach significantly reduces user inconvenience by eliminating irrelevant authentication prompts.
Alex Weinart - Microsoft
The post continues to ensure that the login requests are still in the app, and if, for say, you are traveling and the app thinks it is a suspicious login attempt because you are in a new location, you can still log in to the app and manually approve the MFA prompt. This is a nice feature, and as Microsoft has recently decided to revamp their security through AI and other methods, this is likely a push as part of that effort to make security smarter and not harder on the users.
All the latest news, reviews, and guides for Windows and Xbox diehards.
Overall, this is a good change. It doesn't hurt anybody, and if a company has passwordless authentication set up and all an attacker needs is an email or username to send MFA prompts, this is likely a welcome improvement. Microsoft boasts, "We've prevented more than 6 million passwordless and MFA notifications since the deployment began." This change was implemented near the end of September, which is quite a lot of volume in just over a month.
If you're interested in cybersecurity or want to learn more about MFA security and its implementation in Microsoft Entra (previously Microsoft Azure Active Directory), check out this resource from Microsoft.
Do you use Microsoft authenticator? Does your company use number matching? Let us know in the comments.
Microsoft Authenticator | Google Play & Apple Store
Microsoft Authenticator is a great tool for two-factor authentication and password management. Now, it also supports auto-filling addresses and payment information. It's available on iOS and Android.

Colton is a seasoned cybersecurity professional that wants to share his love of technology with the Windows Central audience. When he isn’t assisting in defending companies from the newest zero-days or sharing his thoughts through his articles, he loves to spend time with his family and play video games on PC and Xbox. Colton focuses on buying guides, PCs, and devices and is always happy to have a conversation about emerging tech and gaming news.