Group that leaked exploit behind 'WannaCry' attack promises more to come
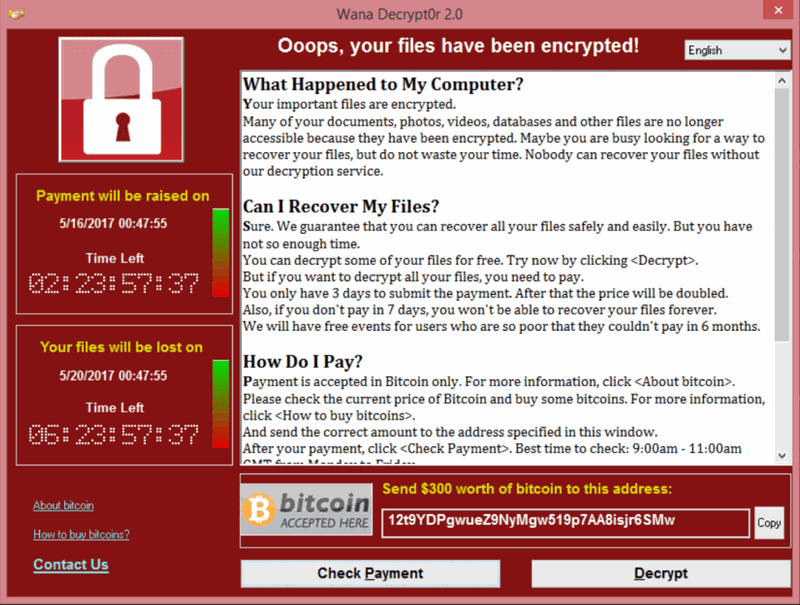
Shadow Brokers, the group that leaked the alleged NSA-developed exploit that was leveraged in the recent massive "WannaCry" ransomware attack, says it is gearing up to release more exploits in the coming months. But any upcoming releases will take a much different form than Shadow Brokers' previous leaks. The hacker group has published a new statement (via The Hacker News) in which it says it will launch a monthly subscription, which the group likens to a "wine of the month club" — only for exploits.
Shadow Brokers claims it will be buying access to a monthly data dump that could include:
- web browser, router, handset exploits and tools
- select items from newer Ops Disks, including newer exploits for Windows 10
- compromised network data from more SWIFT providers and Central banks
- compromised network data from Russian, Chinese, Iranian, or North Korean nukes and missile programs
If true, that's potentially bad news for a number of reasons, not the least of which is the breadth of a potential attack using any exploits that may be released. As we saw with the "WannaCry" ransomware, even an exploit that has already been patched can have a massive impact due to the lag in security updates around the globe.
Though it only affected older versions of Windows without the most recent security updates, WannaCry affected hundreds of thousands of computers worldwide. The consequences of a previously undiscovered exploit getting into the wild could be devastating in the right hands, particularly if Shadow Brokers' claims of exploits for Windows 10 prove true.
'WannaCry' ransomware: Everything you need to know
Further in its statement, Shadow Brokers makes the accusation that U.S. tech firms, including Microsoft, are being paid not to patch vulnerabilities until they are discovered publicly. That runs directly counter to a rather sharp statement released by Microsoft President and Chief Legal Officer Brad Smith, following WannaCry, in which Smith calls for an end to governments stockpiling software vulnerabilities.
All the latest news, reviews, and guides for Windows and Xbox diehards.
Dan Thorp-Lancaster is the former Editor-in-Chief of Windows Central. He began working with Windows Central, Android Central, and iMore as a news writer in 2014 and is obsessed with tech of all sorts. You can follow Dan on Twitter @DthorpL and Instagram @heyitsdtl.