A quick look at security features on Microsoft's new Outlook.com email service
All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
With the launch of Microsoft's Outlook.com, many have been questioning security features of the new email service. The most dominant topic is the limit of 16 characters for passwords. This is a limitation that was also present in Hotmail / Live and has been brought forward into its successor (due to Microsoft's login system). We'll take a look at this issue as well as a quick overview of additional security measures Microsoft has implemented to keep your emails safe.
Password character limitations
A counter question would be do you honestly need more than 16 characters? It's an argument that could span a number of pages in a forum thread or accumulate a hundred or so comments on this article. One side could -- of course -- argue that using as many characters as possible is more secure due to the creation of more possible combinations.
On the other hand, the password "123456789101112131415" is less secure than "3%84Dji8u&L8D", so it's more about how consumers create their account passwords. Using a random generator (or simply having some fun with random combinations in Notepad if you have the time) is always recommended - of course you should always note down what you've decided on. It's amusing to hear / read about company security holes due to employee passwords, "Admin" being the best example. It's certainly not rocket science.
Microsoft has responded to concerns about the 16 character limit, should you be interested to read an official response:
"We are working on increasing this. Unfortunately, for historical reasons, the password validation logic is decentralized across different products, so it's a bigger change than it should be and takes longer to get to market. It's also worth noting that the vast majority of compromised accounts are through malware and phishing. The small fraction of brute force is primarily common passwords like '123456' not due to a lack of complexity."
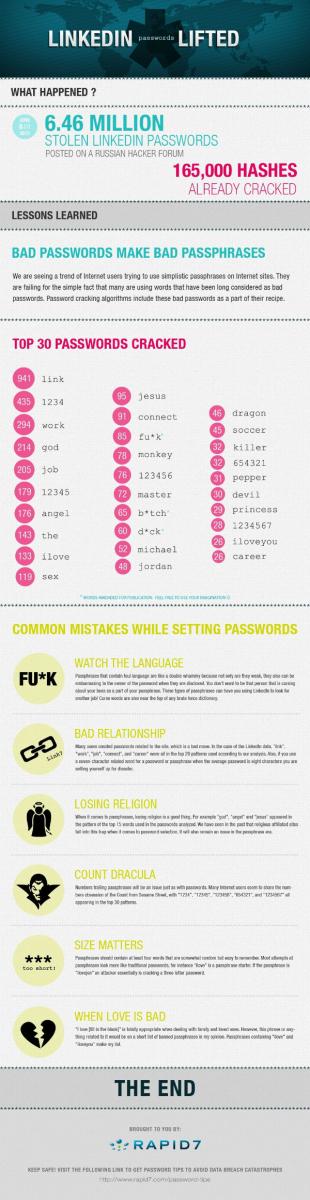
That being said, we can't see an issue with the 16 character limitation. It shouldn't worry consumers when using the service. LinkedIn is a superb example of how security can go horribly wrong. Check out the following Rapid7 infographic (click for larger version) on the most popular passwords that were reportedly already cracked prior to the account passwords being stolen. You'll be surprised by what made the list.
While we can understand the concern for the limitation and that those who are security obsessive would prefer to have a high amount of characters in passwords, it's not the end of the world should you ensure they're randomly generated with a sufficient combination of alphanumeric (and special) characters.
All the latest news, reviews, and guides for Windows and Xbox diehards.
Single-use codes for masking account credentials
Microsoft has also implemented single-use codes for logging into Outlook.com when on a public computer or other devices where the user may be at risk of having their passwords detected. The single-use code enables Microsoft to text a passcode to the user's mobile phone (email and phone number required when attempting to login), which negates the need for the account password.
The single-use code (as the name implies) can only be used once and is invalid once the user has successfully logged in. It's good to have extra protection in place for Outlook.com users to be able to access their email on computers / devices in public places.
Two-factor authentication and no targeted advertising
One of the major reasons Microsoft provides to attract Gmail users is the company will not be reading emails to provide targeted and relevant advertising using its network of publishers - remember the Gmail man? This ensures user data is kept private. While advertising is present on main folder view pages, its in the form of general adverts that will be displayed to everyone.
Microsoft has also responded to a question on Reddit inquiring about two-factor authentication in its global login system:
"Over the last 6 months we have rolled out two-factor authentication in several systems that use Microsoft account. For example, you need to use two-factor auth to buy stuff on xbox.com, to remotely fetch files from other computers on SkyDrive and more. We are learning a lot from this and have more in the works. We see two-factor auth as being an increasingly important piece of our protection suite."
What we can all take away from this is that Microsoft is working hard on further tightening security in its products and backend services. We can expect to see more information and updates applied to enhance protection already implemented. All-in-all, rather good stuff.
Let us know your thoughts in the comments, do you believe Microsoft is doing enough to secure your data in the cloud?

Rich Edmonds was formerly a Senior Editor of PC hardware at Windows Central, covering everything related to PC components and NAS. He's been involved in technology for more than a decade and knows a thing or two about the magic inside a PC chassis. You can follow him on Twitter at @RichEdmonds.

