Microsoft, Google, and Apple want you to say farewell to passwords
Microsoft wants people to move away from passwords, and it's working with the FIDO Alliance to make it easier.
All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
What you need to know
- Alongside Apple and Google, Microsoft announced support for an expanded FIDO standard that will help people go passwordless.
- Soon, people will be able to sign in to services and websites using passwordless authentication across all major platforms.
- Windows, iOS, Android, and macOS devices will work with passwordless login, as will Edge, Chrome, and Safari.
Yesterday, May 5, 2022, was World Password Day. In an ironic celebration, Microsoft commemorated the day by helping people move away from passwords altogether. The company announced support for the expansion of a passwordless standard created by the FIDO Alliance and the World Wide Web consortium. Apple and Google also announced support for the standard, which is a major step forward toward a passwordless future.
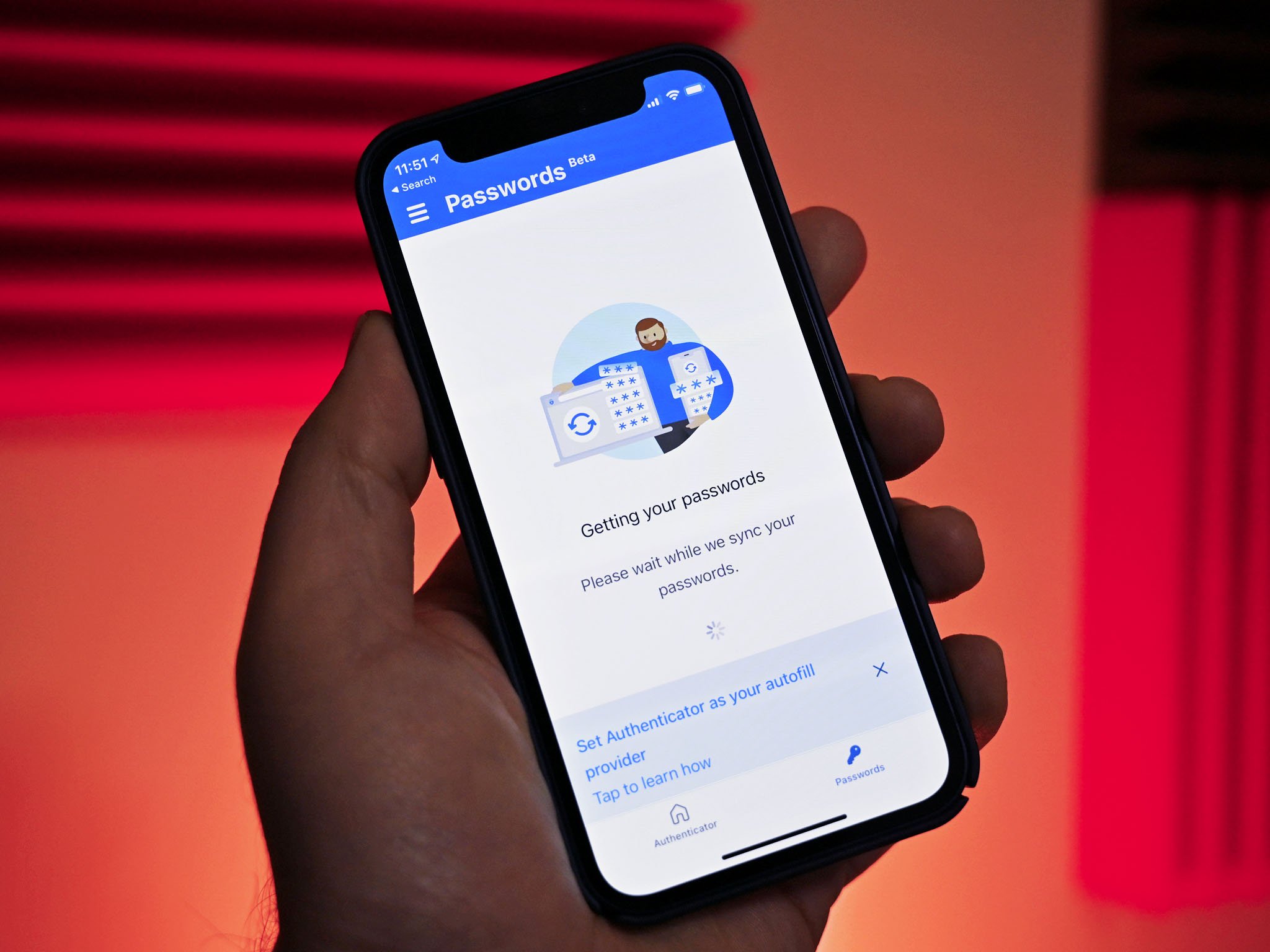
Passwords can be stolen or phished out by attackers. Microsoft argues that it's more secure to use multi-device FIDO credentials. These are also referred to as passkeys and allow people and organizations to shift away from insecure passwords.
The idea is that people will be able to verify their identity by logging into a physical device, such as a smartphone. This could be done with a fingerprint, face unlock, or a PIN and used to log in to websites and services, all without requiring a password.
Microsoft highlighted in a Tech Community post that biometric information never leaves a device. "Passkeys are a safer, faster, easier replacement for your password. With passkeys, you can sign in to any supported website or application by simply verifying your face, fingerprint or using a device PIN," added the company.
It's already possible to use Windows Hello to sign in to sites that support passkeys. Soon, people will be able to sign in to their Microsoft account with a passkey using an Apple or Google device.
I'm SO excited about today's news! After 6+ years of effort, we have an open standard for passwordless authentication that Microsoft, Google and Apple (yes, even Apple!) have all agreed to build into their OS's and browsers https://t.co/YUJwPIWz8RI'm SO excited about today's news! After 6+ years of effort, we have an open standard for passwordless authentication that Microsoft, Google and Apple (yes, even Apple!) have all agreed to build into their OS's and browsers https://t.co/YUJwPIWz8R— Alex Simons (@Alex_A_Simons) May 5, 2022May 5, 2022
The cross-device and cross-OS support of passkeys is — ahem — key to the operation. "With passkeys on your mobile device, you're able to sign in to an app or service on nearly any device, regardless of the platform or browser the device is running," said Microsoft vice president for security, compliance, identity, and privacy Vasu Jakkal in a statement to the Verge. "For example, users can sign-in on a Google Chrome browser that's running on Microsoft Windows—using a passkey on an Apple device."
Alongside its support for the FIDO standard, Microsoft announced new capabilities to help enterprises go passwordless. Windows 365, Azure Virtual Desktop, and Virtual Desktop Infrastructure all support passwordless login in preview builds of Windows 11. It's also on the way to Windows 10.
All the latest news, reviews, and guides for Windows and Xbox diehards.
Microsoft Authenticator will soon support using multiple passwordless accounts. The capability will ship to iOS devices this month and to Android users in the future.
Microsoft has pushed people to go passwordless for five years. The company shared that 240 million people now sign in to Microsoft services each month without using a password. 330,000 people have removed their passwords from their Microsoft accounts in the past six months as well.

Sean Endicott is a news writer and apps editor for Windows Central with 11+ years of experience. A Nottingham Trent journalism graduate, Sean has covered the industry’s arc from the Lumia era to the launch of Windows 11 and generative AI. Having started at Thrifter, he uses his expertise in price tracking to help readers find genuine hardware value.
Beyond tech news, Sean is a UK sports media pioneer. In 2017, he became one of the first to stream via smartphone and is an expert in AP Capture systems. A tech-forward coach, he was named 2024 BAFA Youth Coach of the Year. He is focused on using technology—from AI to Clipchamp—to gain a practical edge.
