'Petya' ransomware: Everything you need to know
There's another massive ransomware attack sweeping across the world. Here's what you need to know to stay safe.

All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
Little more than a month has passed since the notorious WannaCry ransomware attack hit headlines across the world. Now, sadly, we're in a period of another such attack, and this time it's dubbed "Petya" or "GoldenEye."
The basic problem is the same as the WannaCry outbreak: PCs are infected, locked up and files encrypted with a ransom demanded for access to the blocked files. It's not exactly the same as WannaCry, nor is it currently as widespread, but it's still important to know what you're dealing with.
7 tips to keep your Windows PC protected against malware
What you need to know about the Petya Ransomware
What is Petya?
Petya is a piece of ransomware that infects computers with the intent of monetary extortion in return for access to the contents of the PCs. It encrypts files, claiming only to let you back in upon receipt of a ransom.
Which platforms does it affect?
It's a Windows-only affair, and Microsoft already released a patch in March that should protect users, assuming it's installed.
Microsoft's March 2017 MS17-010 security update is where the necessary patches have been compiled.
How does Petya spread?
Petya tries to infect PCs using two methods, moving on to the second if the first fails. Once again, as with WannaCry, Petya utilizes the leaked EternalBlue exploit first developed by American security services.
All the latest news, reviews, and guides for Windows and Xbox diehards.
If that fails because the system has been properly patched, for example, it moves on to the second method, which is to use two Windows administrative tools. Unlike WannaCry, Petya looks to spread within local networks without seeding itself externally, perhaps limiting its early global impact somewhat.
As reported by The Guardian, there is a secondary "vaccine" that may prevent infection on a specific PC, but it leaves Petya free to try and spread to others:
For this particular malware outbreak, another line of defence has been discovered: 'Petya' checks for a read-only file, C:\Windows\perfc.dat, and if it finds it, it won't run the encryption side of the software. But this "vaccine" doesn't actually prevent infection, and the malware will still use its foothold on your PC to try to spread to others on the same network.
What regions are affected by Petya?
The outbreak is reported to have surfaced in Eastern Europe, with the Ukraine in particular being hit hard. Organizations in France, the UK, Russia, Denmark and the U.S. are also confirmed as being affected.
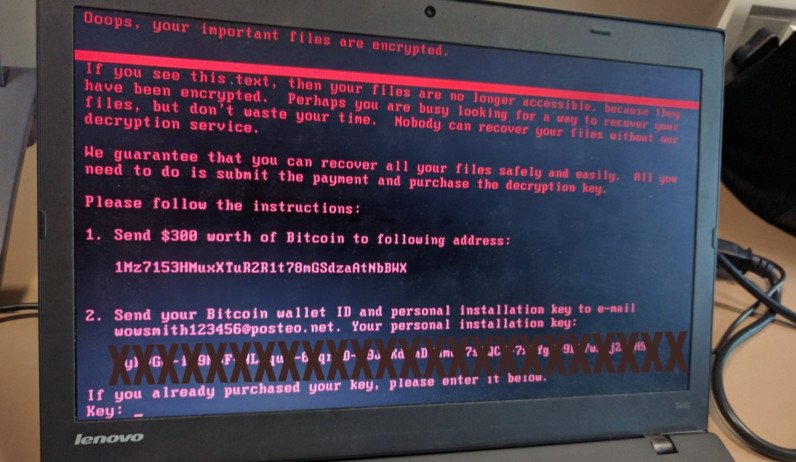
How much is Petya's ransom?
Right now, $300 in Bitcoin.
If I get hit, should I pay the ransom?
No way! Remember that these are criminals, and chances are you'll be both out of pocket and without your files if you pay. These people don't want to be found, so they're unlikely to do anything that would give authorities any kind of edge in tracking them down.
In this case, there's also the issue of how the ransom is being collected. Instead of a unique wallet per user as with WannaCry, Petya is stuffing it all into one. And that has presented its own problems. Users have to send an email to get their decryption codes, and as reported by The Verge, that email address has been shut down:
But in the wake of today's globe-spanning infections, Posteo announced today that all account access to the "wowsmith" address have been blocked, making it impossible for the group to read or respond to any messages sent to the address.
Chances are you won't get the key you need even if the miscreants behind the attack ever planned on sending it out.
Am I at risk of Petya infection?
Sadly, we're always at some kind of risk on the internet. As detailed above, Microsoft already released a patch to mitigate at least the EternalBlue exploit, so the first port of call is to make sure that patch is installed.
If you don't have your updates turned on, that's a good place to start. Some people may not like "forced updates" but in most cases you shouldn't ignore them.
How do you get the files back?
Right now there's not a lot suggesting compromised files will ever be accessible again. If you don't have a backup, you might have lost your stuff. It's good practice to always back up your important files.
Is there anything I can do if I am affected?
It appears that there is. This tweet by Hacker Fantastic details what is actually the encryption process and how you can throw a spanner in the works.
If machine reboots and you see this message, power off immediately! This is the encryption process. If you do not power on, files are fine. pic.twitter.com/IqwzWdlrX6If machine reboots and you see this message, power off immediately! This is the encryption process. If you do not power on, files are fine. pic.twitter.com/IqwzWdlrX6— hackerfantastic.crypto (@hackerfantastic) June 27, 2017June 27, 2017
You still can't use your PC but the data you have stored on it will apparently be OK.
Your thoughts
That's a quick overview of where things stand right now, but it's an ever-changing situation. We'll do our best to keep on top of the latest details. And if you have anything helpful to share, be sure to leave it in the comments below.

Richard Devine is the Managing Editor at Windows Central with over a decade of experience. A former Project Manager and long-term tech addict, he joined Mobile Nations in 2011 and has been found in the past on Android Central as well as Windows Central. Currently, you'll find him steering the site's coverage of all manner of PC hardware and reviews. Find him on Mastodon at mstdn.social/@richdevine