Microsoft talks more about putting in Windows Hello support in Edge browser
Microsoft is currently testing the addition of Windows Hello security support in Insider builds of Windows 10's Microsoft Edge browser. The company is revealing more information on those plans, including how website developers can add support for this feature on their sites.
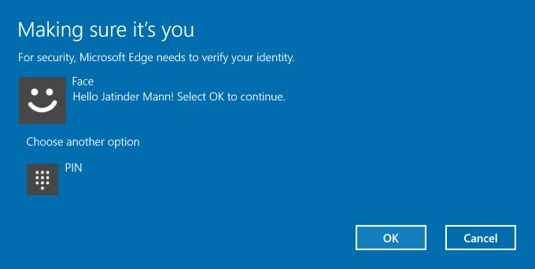
In order to authenticate a user, the server sends down a plain text challenge to the browser. Once Microsoft Edge is able to verify the user through Windows Hello, the system will sign the challenge with a private key previously provisioned for this user and send the signature back to the server. If the server can validate the signature using the public key it has for that user and verify the challenge is correct, it can authenticate the user securely.These keys are not only stronger credentials – they also can't be guessed and can't be re-used across origins. The public key is meaningless on its own and the private key is never shared. Not only is using Windows Hello a delightful user experience, it's also more secure by preventing password guessing, phishing, and keylogging, and it's resilient to server database attacks.
Microsoft says site developers can use the Web Authentication API to begin prototyping and testing for the addition of Windows Hello support in Edge. The company is working with both the FIDO Alliance and W3C Web Authentication working group to help standardize these APIs so that all websites can benefit from these additional security measures.
All the latest news, reviews, and guides for Windows and Xbox diehards.

John Callaham was a former contributor for Windows Central, covering Windows Phone, Surface, gaming, and more.
