New 'Bad Rabbit' ransomware attack spreading across Europe
Following in the footsteps of WannaCry and Petya, a new strain of ransomware is now making its way across Russia and Europe.
All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
A new ransomware attack is now spreading across Europe in an outbreak that carries echoes of the WannaCry and Petya attacks that hit scores of PCs earlier in 2017. Called Bad Rabbit, the malware appears to have most strongly impacted Russian and Ukrainian organizations thus far, though similar attacks have been spotted in Turkey and Germany as well.
According to Kaspersky researchers, Bad Rabbit has already infected a number of Russian media outlets, including the Interfax news agency and Fontanka.ru. Odessa International Airport has also reported a cyberattack, but it's not immediately clear whether the two are related. According to ZDNet, the Kyiv Metro's payment systems also appear to be impacted.
Kaspersky explains that the ransomware appears to be targeting corporate networks in a manner similar to the Petya ransomware, but it isn't clear at this point whether Bad Rabbit is related to Petya. Meanwhile, ESET researchers claim to have identified the malware as Diskcoder.D, which is a variant of Petya.
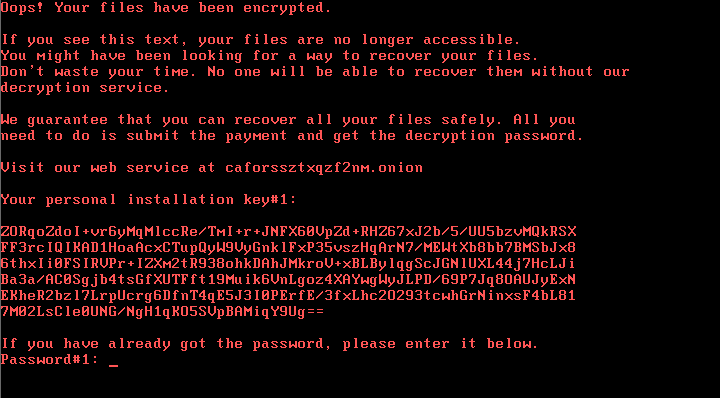
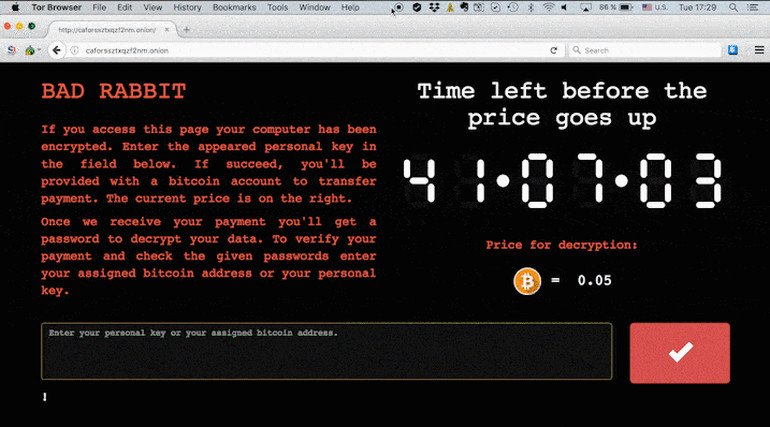
Once infected, victims of the Bad Rabbit attack are directed to a darknet website with a note that demands 0.05 bitcoin (currently around $280) as ransom. The website also features a timer counting down to when the price will increase. It's not yet clear, Kaspersky says, whether it's possible to recover the files encrypted by Bad Rabbit. However, Kaspersky says you can protect yourself by blocking execution of files "c: \ windows \ infpub.dat" and "C: \ Windows \ cscc.dat." If you are infected, experts advise against paying the ransom.
All the latest news, reviews, and guides for Windows and Xbox diehards.

Dan Thorp-Lancaster is the former Editor-in-Chief of Windows Central. He began working with Windows Central, Android Central, and iMore as a news writer in 2014 and is obsessed with tech of all sorts. You can follow Dan on Twitter @DthorpL and Instagram @heyitsdtl.
