Microsoft issues emergency Windows patch for PrintNightmare vulnerability [Updated]
Microsoft recently released an out-of-band patch for Windows that addresses the PrintNightmare vulnerability.
All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
What you need to know
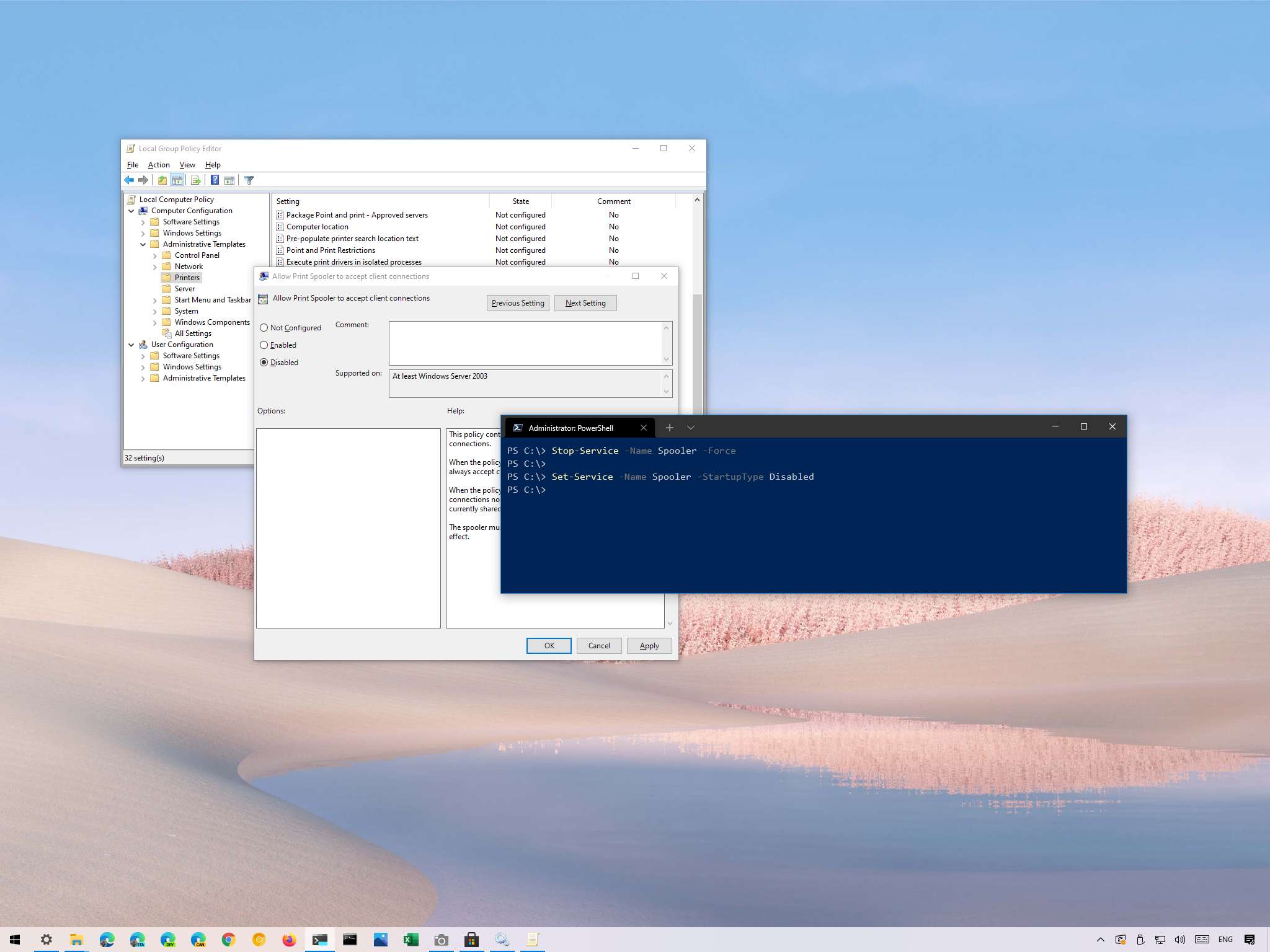
- Microsoft released a critical emergency Windows patch that addresses the PrintNightmare vulnerability.
- If exploited, the vulnerability allows attackers to install programs, create new accounts, and create, view, or delete data.
- The patch is available for Windows 10, Windows 8.1, Windows 7, and multiple versions of Windows Server.
Update July 7, 2021 at 5:05 pm ET: Individuals are finding ways to get around Microsoft's patch, meaning PrintNightmare vulnerabilities remain an active issue. This article's text has been updated to reflect new information.
Microsoft has issued a critical emergency patch for a flaw in the Windows Print Spooler service. The vulnerability is known as PrintNightmare. When exploited, it allows attackers to "install programs; view, change, or delete data; or create new accounts with full user rights," according to Microsoft. The problem is, reports are coming in indicating that the patch doesn't actually fix the entire issue (see below).
The security patch is available for several versions of Windows 10, Windows 8.1, Windows Server 2019, Windows Server 20212 R2, Windows Server 2008, and Windows RT 8.1. It's also available for Windows 7, which is surprising considering the operating system is out of support.
Updates for Windows 10 version 1607, Windows Server 2016, and Windows Server 2012 are not available at this time but will be released soon, according to Microsoft.
PrintNightmare was revealed after researchers published a proof-of-concept exploit, seemingly by accident.
Microsoft's executive summary of the vulnerability includes the following update (emphasis added):
UPDATE July 6, 2021: Microsoft has completed the investigation and has released security updates to address this vulnerability. Please see the Security Updates table for the applicable update for your system. We recommend that you install these updates immediately. If you are unable to install these updates, see the FAQ and Workaround sections in this CVE for information on how to help protect your system from this vulnerability. See also KB5005010: Restricting installation of new printer drivers after applying the July 6, 2021 updates.
The fact the patch is available for Windows 7 indicates the severity of the issue since Windows 7 has been out of support since January 14, 2020. However, there's one major problem with Microsoft's efforts: They aren't enough to stop the threat.
All the latest news, reviews, and guides for Windows and Xbox diehards.
Security researcher Matthew Hickey stated that Microsoft's fix only patches up one element of the vulnerability (via BleepingComputer).
The Microsoft fix released for recent #PrintNightmare vulnerability addresses the remote vector - however the LPE variations still function. These work out of the box on Windows 7, 8, 8.1, 2008 and 2012 but require Point&Print configured for Windows 2016,2019,10 & 11(?). 🤦♂️ https://t.co/PRO3p99CFoThe Microsoft fix released for recent #PrintNightmare vulnerability addresses the remote vector - however the LPE variations still function. These work out of the box on Windows 7, 8, 8.1, 2008 and 2012 but require Point&Print configured for Windows 2016,2019,10 & 11(?). 🤦♂️ https://t.co/PRO3p99CFo— hackerfantastic.crypto (@hackerfantastic) July 6, 2021July 6, 2021
Via local privilege escalation, threat actors can still target vulnerabilities. Worse yet, according to other reports, there are ways for individuals to bypass Microsoft's patch entirely and target vulnerable systems via remote code execution in addition to the aforementioned local privilege execution.
Dealing with strings & filenames is hard😉
New function in #mimikatz 🥝to normalize filenames (bypassing checks by using UNC instead of \\server\share format)
So a RCE (and LPE) with #printnightmare on a fully patched server, with Point & Print enabled
> https://t.co/Wzb5GAfWfd pic.twitter.com/HTDf004N7rDealing with strings & filenames is hard😉
New function in #mimikatz 🥝to normalize filenames (bypassing checks by using UNC instead of \\server\share format)
So a RCE (and LPE) with #printnightmare on a fully patched server, with Point & Print enabled
> https://t.co/Wzb5GAfWfd pic.twitter.com/HTDf004N7r— 🥝 Benjamin Delpy (@gentilkiwi) July 7, 2021July 7, 2021
0patch has released a patch that it claims is capable of defending against the problems Microsoft's official patch cannot. However, installing Microsoft's July 6 patch will disable 0patch's benefits, so you'll have to go with one or the other.

Sean Endicott is a news writer and apps editor for Windows Central with 11+ years of experience. A Nottingham Trent journalism graduate, Sean has covered the industry’s arc from the Lumia era to the launch of Windows 11 and generative AI. Having started at Thrifter, he uses his expertise in price tracking to help readers find genuine hardware value.
Beyond tech news, Sean is a UK sports media pioneer. In 2017, he became one of the first to stream via smartphone and is an expert in AP Capture systems. A tech-forward coach, he was named 2024 BAFA Youth Coach of the Year. He is focused on using technology—from AI to Clipchamp—to gain a practical edge.
