Beginner's guide to Windows 10 encryption
All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
In order to add a layer of protection to the sensitive data on your PC, you might want to encrypt it. Encryption essentially means that you're turning data into something unreadable without proper authentication.
Encrypting a drive or a folder or a file generally means you have a single password that must be used in order to decrypt and access. Not only does this stop outside parties from hacking their way into your files, it also protects in the event that you forget your PC somewhere or, worst case, it's stolen.
There are two encryption methods built into Pro, Enterprise, and Education versions of Windows 10. For everyone else, there's a third way to encrypt your data. Let's take a look at how all three work to help you choose which encryption method is best for you.
Encrypting File System
Encrypting File System (EFS) is a file encryption service in Windows 10 Pro, Enterprise, and Education editions. It's very easy to use, often requiring just a couple of clicks to encrypt a file or folder. When the user who encrypted the files is logged in, the files are accessible. If another user is logged in, the files are inaccessible. For that reason, you want to choose a strong password for the account on your PC.
Compared to BitLocker whole-drive encryption, EFS isn't quite as secure. Windows itself creates the encryption key, and it is saved locally. The key is also protected with encryption, but it's not the same level of security you'd find with a Trusted Module Platform (TPM) chip.
Despite the steps taken to protect EFS keys, someone with the time and means could eventually decipher the key. A user might also forget to manually encrypt a sensitive file, further leaving it open to snooping. Finally, since the entire drive is not encrypted, there's a chance of data leaking into temporary files where it could potentially be accessed.
EFS is best viewed as a quick way to protect files and folders on a PC with multiple users. Not even administrators have access to the encrypted files, and, if your password was changed without your knowledge, your encrypted files would remain encrypted.
All the latest news, reviews, and guides for Windows and Xbox diehards.
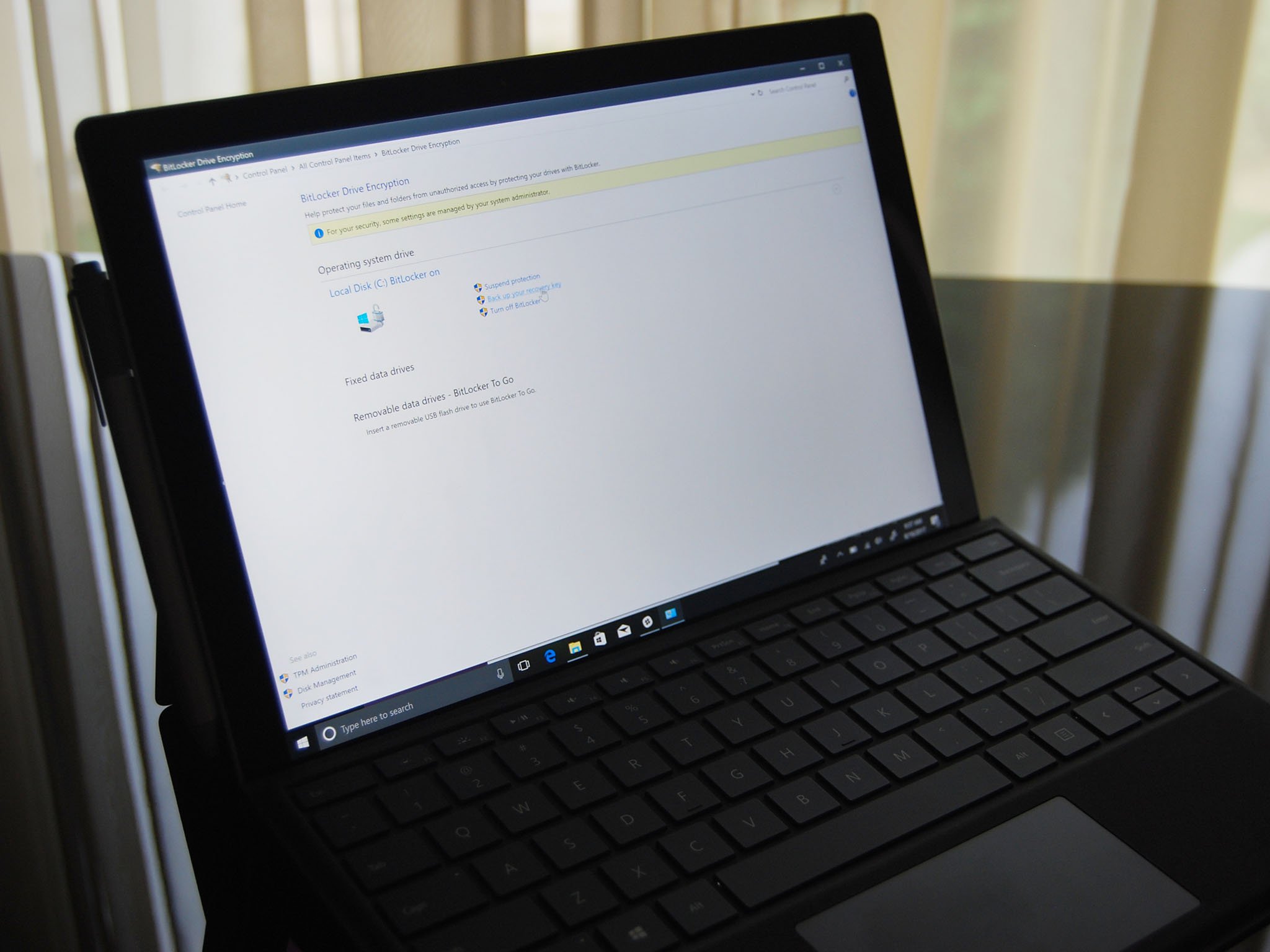
BitLocker
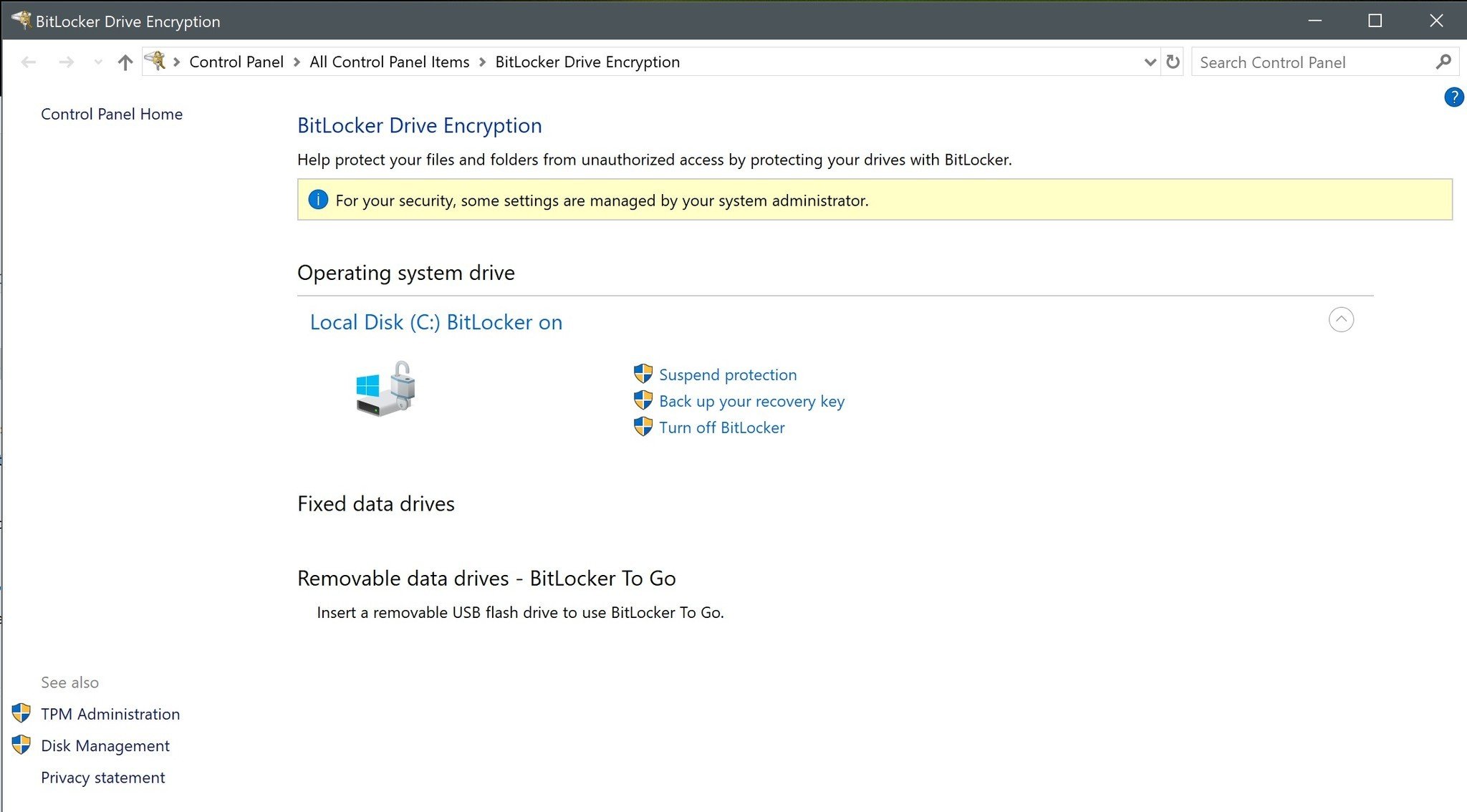
BitLocker is another drive encryption feature special to Windows Pro, Enterprise, and Education. While it's generally recommended that the PC has a Trusted Platform Module (TPM) chip, there is a way you can turn on BitLocker without.
A TPM chip is a special bit of hardware added to your motherboard that is used to hold bits of encryption keys. TPM chips are designed to sniff out unauthorized or tampering users quickly, in which case the chip will not give up the part of the decryption key it's holding.
Rather than choosing single files and folders for encryption, BitLocker encrypts your entire drive. No matter the user logged in, the drive remains encrypted. Any new files you create will fall under the same layer of protection, so there's no chance you'll forget to encrypt a sensitive file. To unlock a drive that's protected with BitLocker, you can either enter a password or you can set up a USB drive that, when inserted, unlocks the PC.
How to use BitLocker Drive Encryption on Windows 10
Third-party encryption software
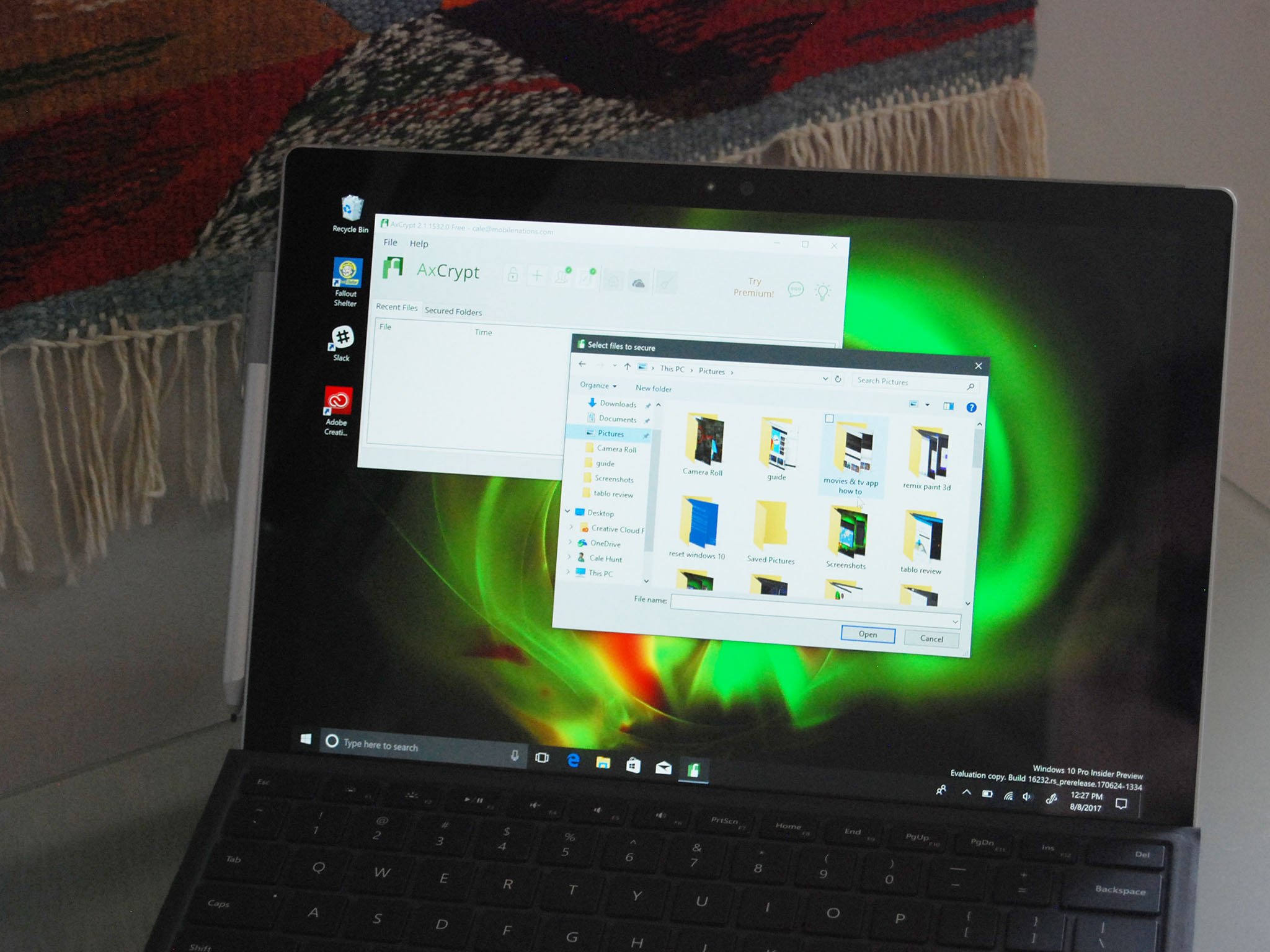
Until EFS and BitLocker become available in Windows 10 Home (any time now, Microsoft), there are numerous third-party encryption programs that can fill the void.
These programs differ in what they can protect. Some will encrypt whole drives, just like BitLocker, while others will encrypt files and folders, just like EFS. The best encryption software also usually comes with a bunch of extra features, like file shredders, cloud storage, and password managers.
The best encryption software also lets you set a master password that is only saved where you choose. That means that you can write it down, save it to a USB drive, or keep it in your head. Without the password, your files will remain encrypted forever. Software-based encryption is open to certain attacks, but in most cases, encryption is still better than no encryption.
See the best third-party encryption software
More resources

Cale Hunt brings to Windows Central more than nine years of experience writing about laptops, PCs, accessories, games, and beyond. If it runs Windows or in some way complements the hardware, there’s a good chance he knows about it, has written about it, or is already busy testing it.