How to fix Zoom's Windows 10 user-info and password-leak problems
The Zoom client has a vulnerability that can leak your Windows 10 sign-in information, and until there's a permanent fix, you can use this workaround.
All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
As the health crisis continues around the world, many people are turning to Zoom to communicate using voice and video with colleagues to work from home and stay connected with family and friends. However, a new vulnerability has recently been discovered with the desktop application by security researcher Matthew Hickey (@HackerFantastic) and Twitter user Mitch (@g0dmode) that could allow hackers to obtain people's Windows login name and password.
According to an investigation published by BleepingComputer, the problem is caused because how the Zoom client handles a Uniform Resource Locator (URL). When you use the Zoom chat, any URL you send is converted into a hyperlink (for example,
https://windowscentral.com), which is convenient to open websites using the default web browser.
The only caveat is that if you send a Universal Naming Convention (UNC) path (for example,
\\192.1.1.112\file-sharing-folder), Zoom will also convert the path into an actionable link. If anyone clicks the link, Windows 10 (or another version) will try to connect to a remote host using the Server Message Block (SMB) network file-sharing protocol. When this happens, the system will also send your sign-in name and NT Lan Manager (NTLM) credential hash.
Although the hash containing your username and password are not sent in clear-text, the information can be quickly obtained within seconds using many tools freely available online. In addition to someone stealing your credentials, malicious individuals can also use this vulnerability to launch applications on the local device when the link is actioned.
In this Windows 10 guide, we'll walk you through the steps to temporarily fix the security vulnerability that could allow attackers to obtain your device sign-in credentials until there's a permanent fix.
All the latest news, reviews, and guides for Windows and Xbox diehards.
- How to fix Zoom sign in credential leak using Group Policy
- How to fix Zoom sign in credential leak using Registry
How to fix Zoom sign in credential leak using Group Policy
If you're running Windows 10 Pro (or Enterprise), the easiest way to prevent the credential leak vulnerability while using Zoom is using the Local Group Policy Editor.
To prevent sending your credentials to a remote server with Zoom, use these steps:
Important: This is a temporary workaround, if you configure this policy on a computer joined into a domain or on a device connected to a file-sharing server, such as Network Attached Storage (NAS), you'll have problems accessing the files on the remote computer.
- Open Start.
- Search for gpedit.msc and click OK to open the Local Group Policy Editor.
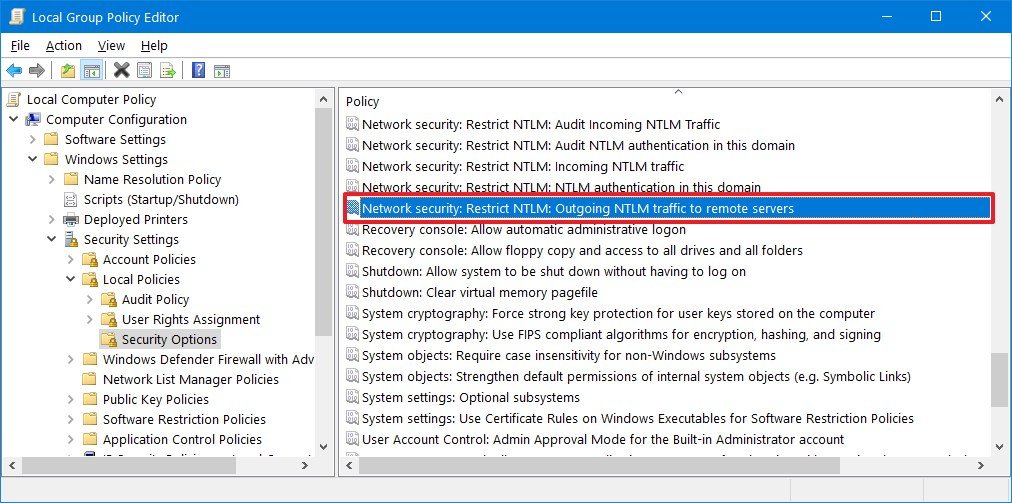
- Browse the following path:
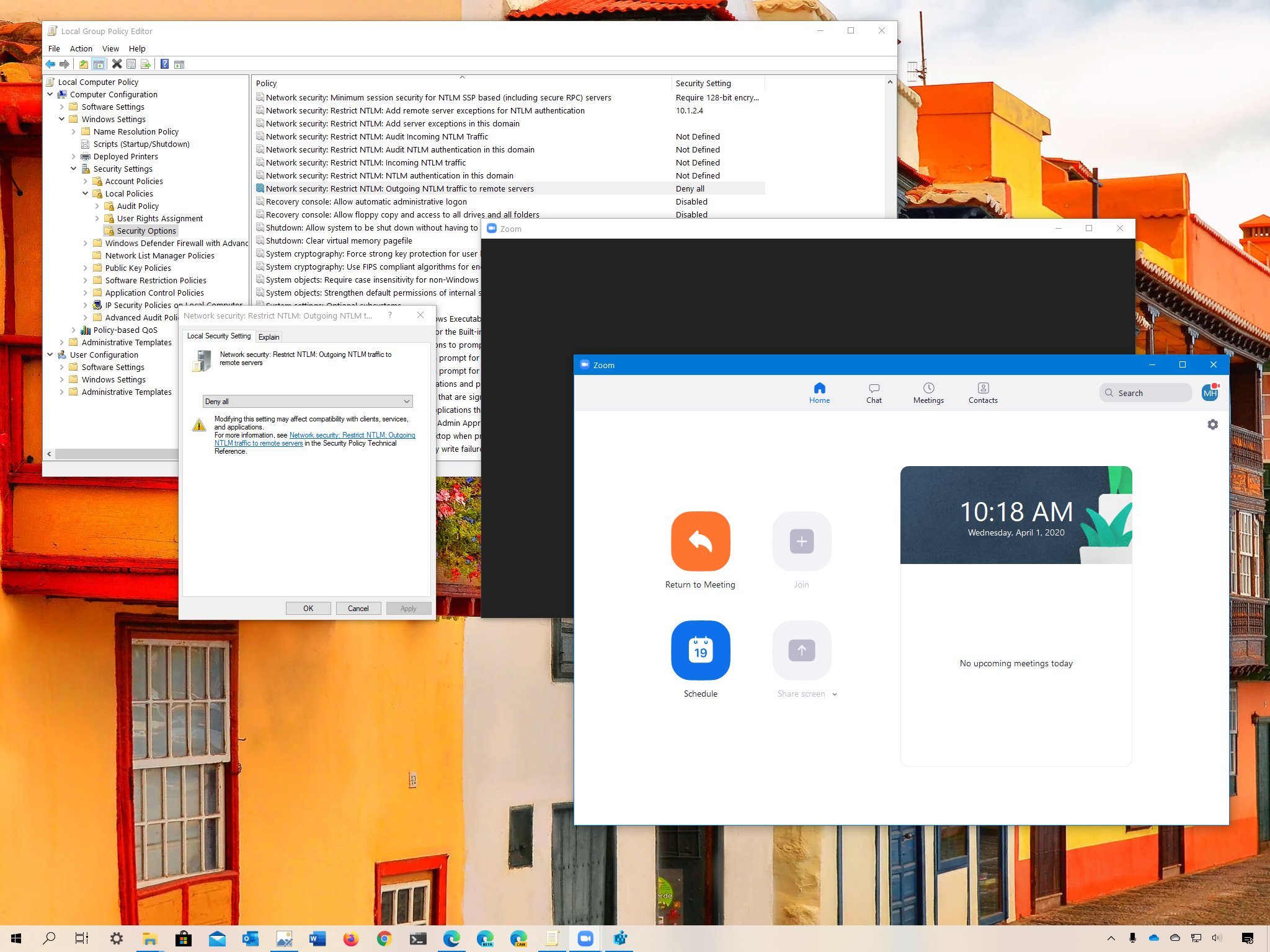
Computer Configuration > Windows Settings > Security Settings > Local Policies > Security Options - On the right side, double-click the Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers policy.
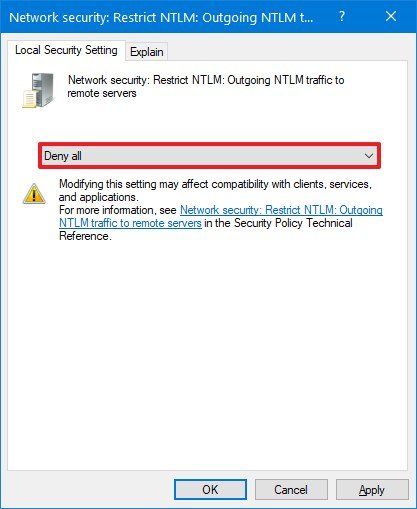
- Select the Deny All option.
- Click the Apply button.
- Click the OK button.
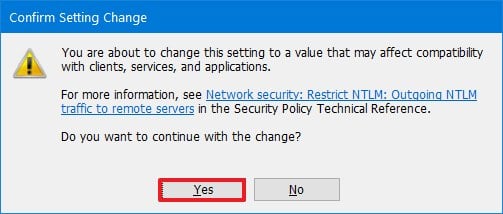
- Click the Yes button to confirm.
Once you complete the steps, when using the Zoom client app on Windows 10, the sign-in NTLM credentials won't be sent to a remote host when accessing a share.
In the case you change your mind, you can roll back the previous settings using the same instructions, but on step No. 5, select the Allow all option.
Configuring an exception (optional)
If you're configuring this policy on a device that needs to connect to a remote server, you can create an exception to access the files or service with these steps:
- Open Start.
- Search for gpedit.msc and click OK to open the Local Group Policy Editor.
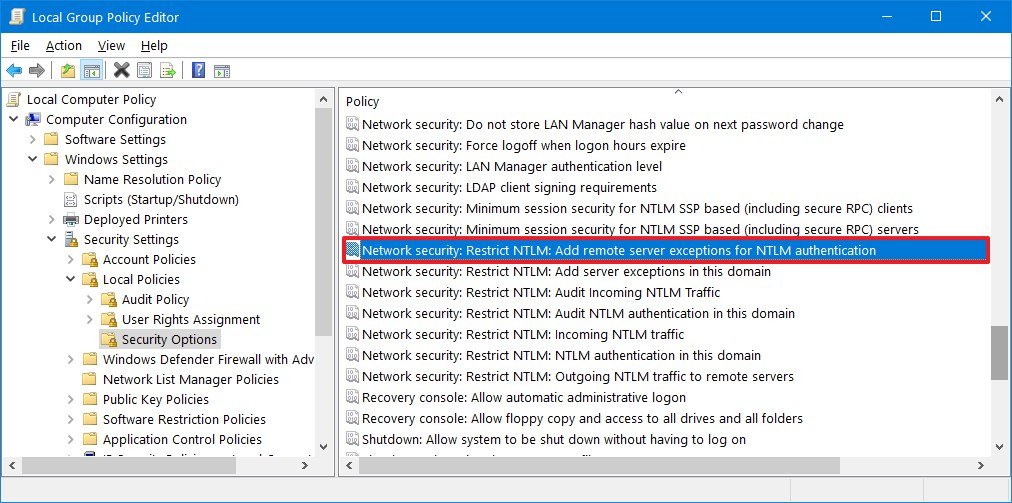
- Browse the following path:
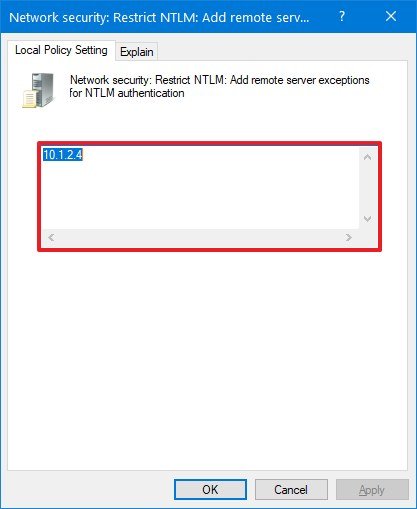
Computer Configuration > Windows Settings > Security Settings > Local Policies > Security Options - On the right side, double-click the Network security: Restrict NTLM: Add remote server exceptions for NTLM authentication policy.
- Specify the TCP/IP address of the remote server you'll be trying to access resources.
- Click the Apply button.
- Click the OK button.
After you complete the steps, Zoom should no longer send your Windows sign-in credentials to a remote host, and you should be able to continue accessing files on a remote server.
When you no longer need this configuration, you can undo the changes with the same instructions, but on step No. 5, make sure to clear the exception list.
How to fix Zoom sign in credential leak using Registry
In the case you're running Windows 10 Home, you won't have access to the Local Group Policy Editor, but you can prevent Zoom from sending your credentials to a remote host by modifying the Registry.
Warning: This is a friendly reminder that editing the Registry is risky, and it can cause irreversible damage to your installation if you don't do it correctly. It's recommended to make a full backup of your PC before proceeding. Also, this is a temporary workaround. If you configure this policy on a computer connected to a file-sharing server, such as Network Attached Storage (NAS), you're likely not able to access files on the remote server.
To prevent leaking your device sign-in information when using Zoom, use these steps:
- Open Start.
- Search for regedit and click the top result to open the Registry.
- Browse the following path:
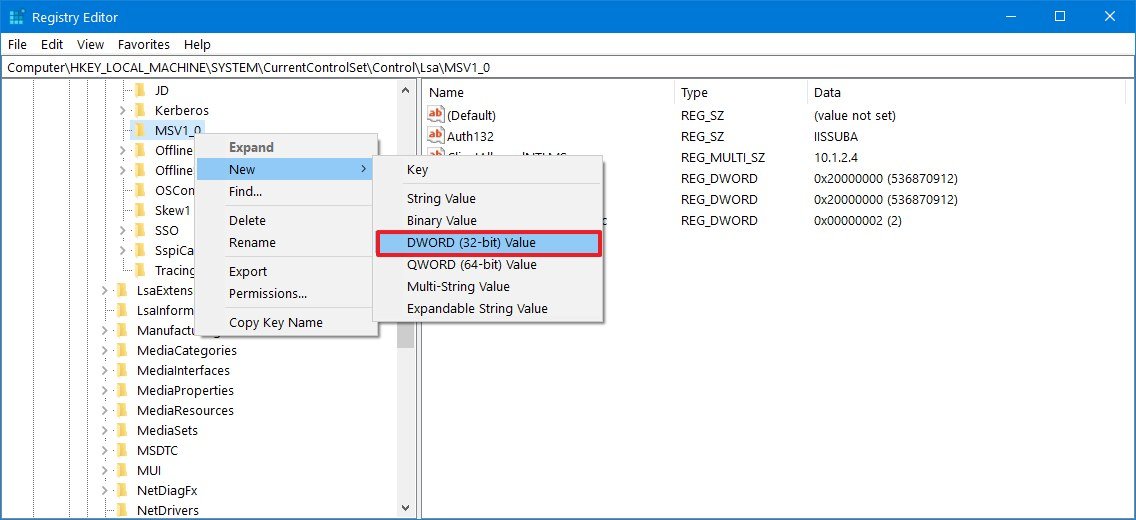
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0Quick tip: On Windows 10, you can now copy and paste the path in the Registry's address bar to quickly jump to the key destination. - Right-click the MSV1_0 key, select New, and click on DWORD (32-bit) Value.
- Name the key RestrictSendingNTLMTraffic and press Enter.
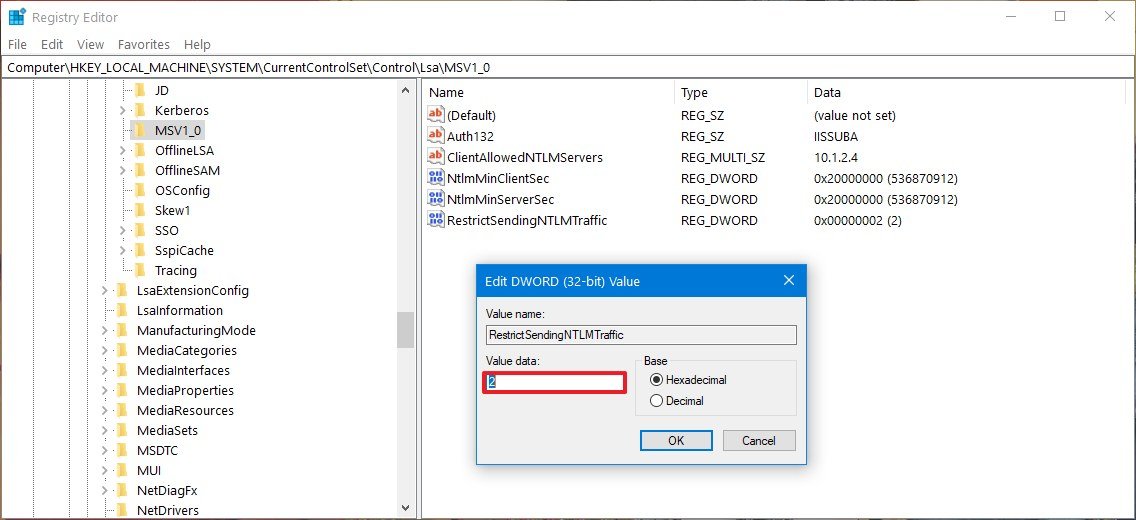
- Double-click the newly created DWORD and set the value from 0 to 2.
- Click the OK button.
After you complete the steps, the Zoom client should no longer send your NTLM credentials over the network to a remote host that someone can use to steal your device sign-in information.
You can always revert the changes by using the same instructions, but on step No. 5, make sure to right-click the RestrictSendingNTLMTraffic key and select the Delete option.
Configuring an exception (optional)
If you're configuring this policy on a device that needs to connect to a remote server, you can create an exception to access the files or service with these steps:
- Open Start.
- Search for regedit and click the top result to open the Registry.
- Browse the following path:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0Quick tip: On Windows 10, you can now copy and paste the path in the Registry's address bar to quickly jump to the key destination. - Right-click the MSV1_0 key, select New, and click on DWORD (32-bit) Value.
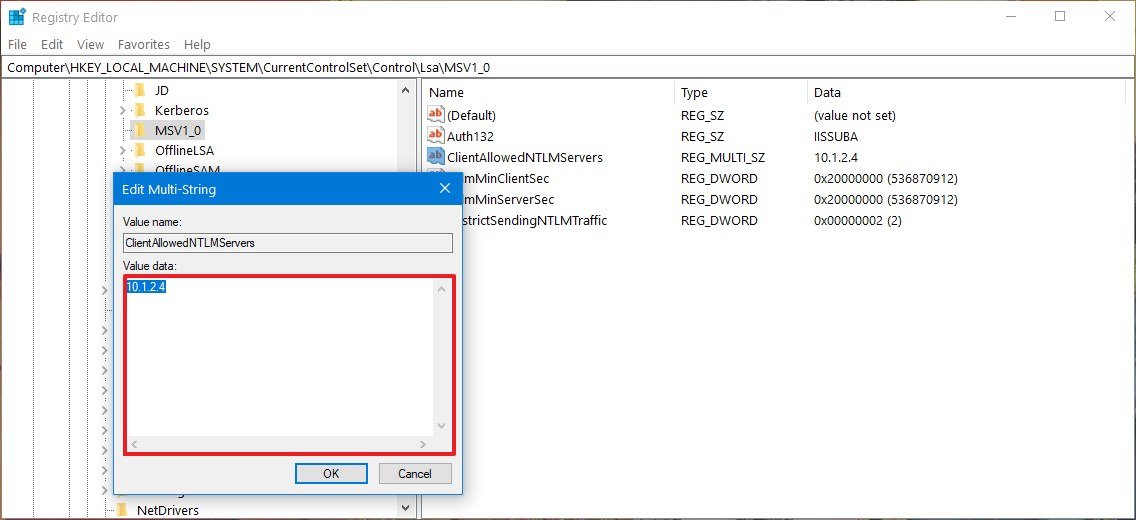
- Name the key ClientAllowedNTLMServers and press Enter.
- Double-click the newly created DWORD and specify the TCP/IP address of the remote server you'll be trying to access resources.
- Click the OK button.
Once you complete the steps, you should be able to continue accessing files on a remote server while stopping the Zoom desktop client from potentially sending your NTLM credentials over the network.
When you no longer need the configuration, you can undo the changes by using the same instructions, but on step No. 5, make sure to right-click the ClientAllowedNTLMServers key and select the Delete option.

Mauro Huculak has been a Windows How-To Expert contributor for WindowsCentral.com for nearly a decade and has over 22 years of combined experience in IT and technical writing. He holds various professional certifications from Microsoft, Cisco, VMware, and CompTIA and has been recognized as a Microsoft MVP for many years.