How to enable Controlled folder access to protect data from ransomware on Windows 10
Windows 10 has an anti-ransomware feature. Here's how to configure it on your computer.
All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
On Windows 10, "Controlled folder access" is an intrusion-prevention feature available with Microsoft Defender Exploit Guard, which is part of the Microsoft Defender Antivirus. It's been designed primarily to stop ransomware from encrypting and taking your data hostage, but it also protects files from unwanted changes from other malicious applications.
The anti-ransomware feature is optional on Windows 10. When enabled, it uses a mechanism to track the apps (executable files, scripts, and DLLs), trying to make changes to files in the protected folders. If the app is malicious or not recognized, the feature will block the attempt in real time, and you'll receive a notification of the suspicious activity.
If you want to safeguard your data with an extra layer of security, you can enable and customize Controlled folder access using the Windows Security app, Group Policy, and even PowerShell.
In this how-to guide, I will walk you through the steps to enable the Controlled folder access feature on your device to prevent ransomware attacks.
How to enable ransomware protection from Windows Security
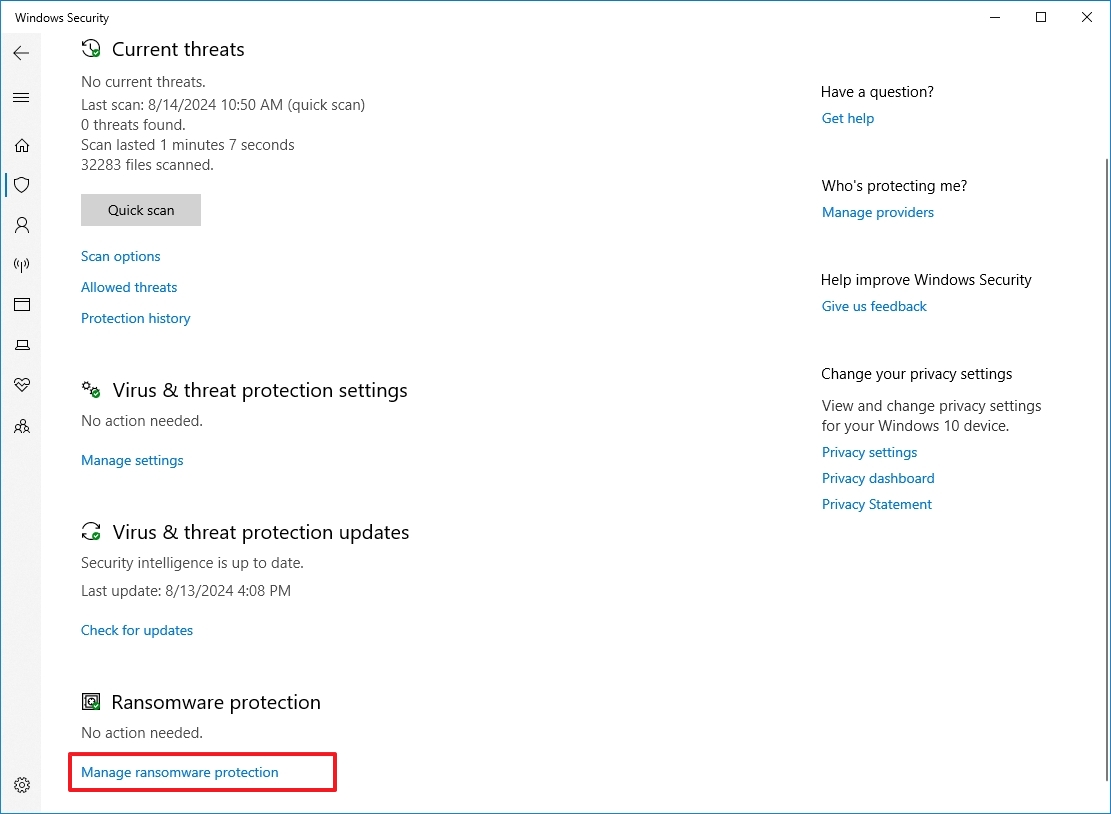
To enable Controlled folder access on Windows 10, use these steps:
- Open Start.
- Search for Windows Security and click the top result to open the app.
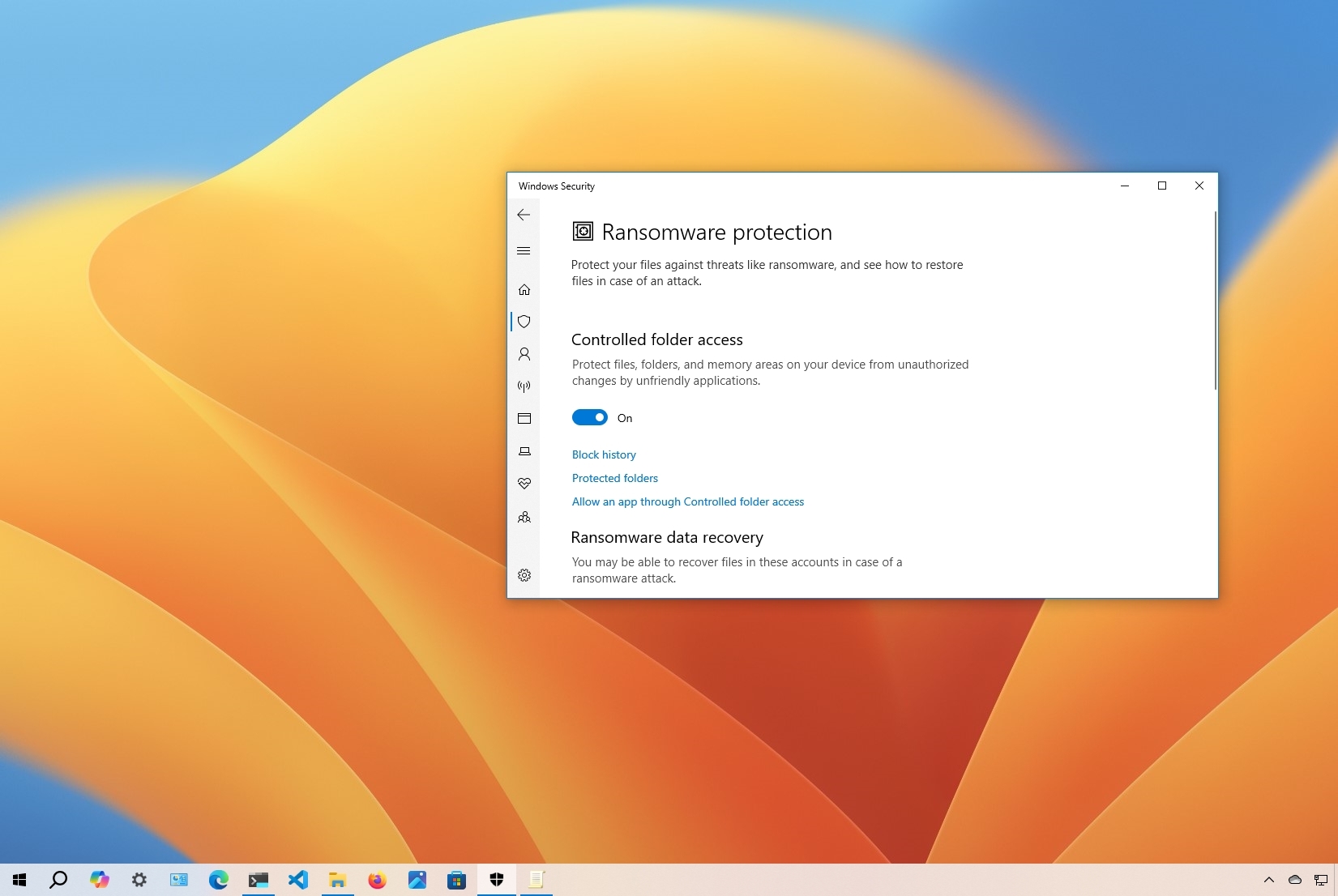
- Click on Virus & threat protection.
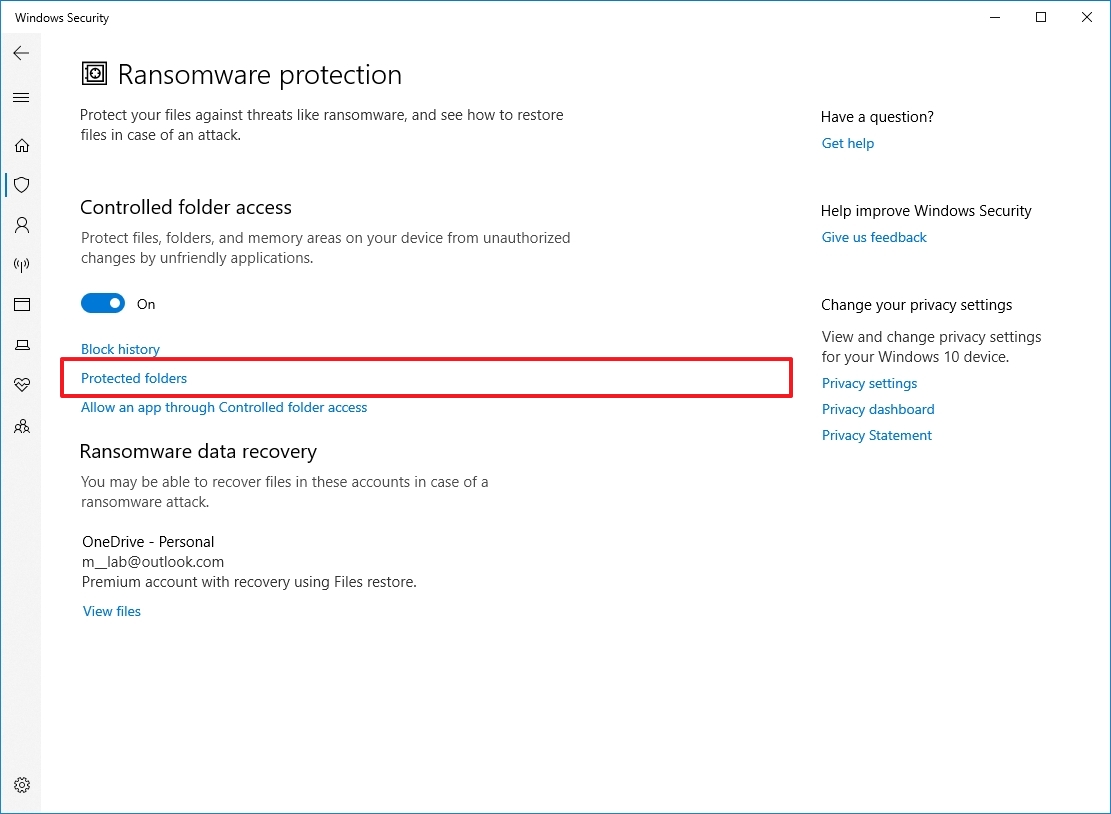
- Click the "Manage ransomware protection" option under the "Ransomware protection" section.
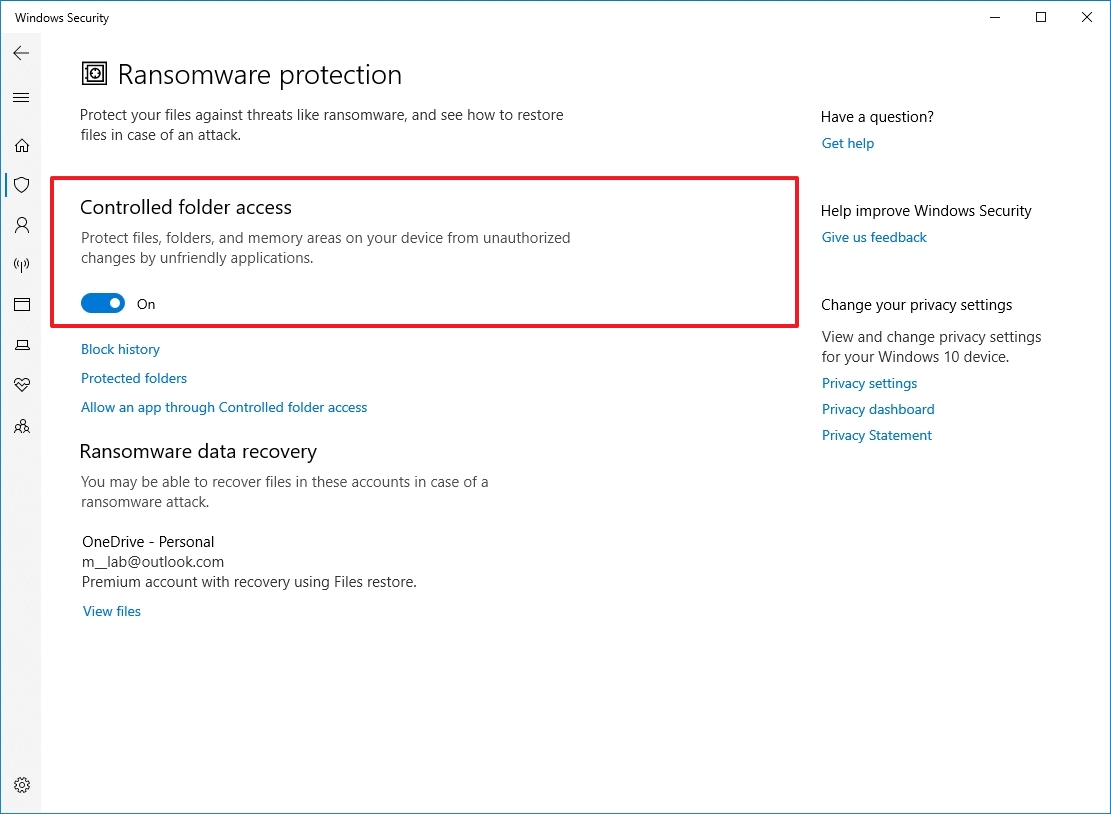
- Turn on the "Controlled folder access" toggle switch.
Once you complete the steps, Microsoft Defender Antivirus will start protecting your files and folders from unauthorized access by malicious programs like ransomware.
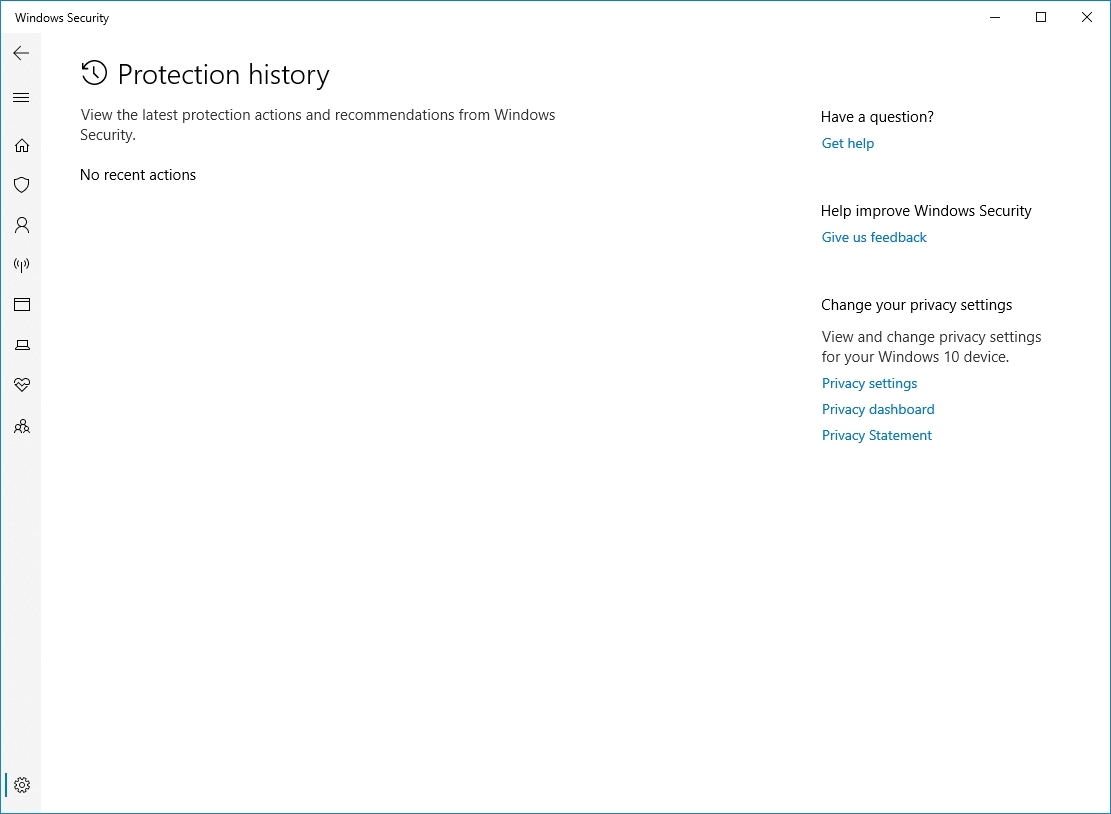
View block history
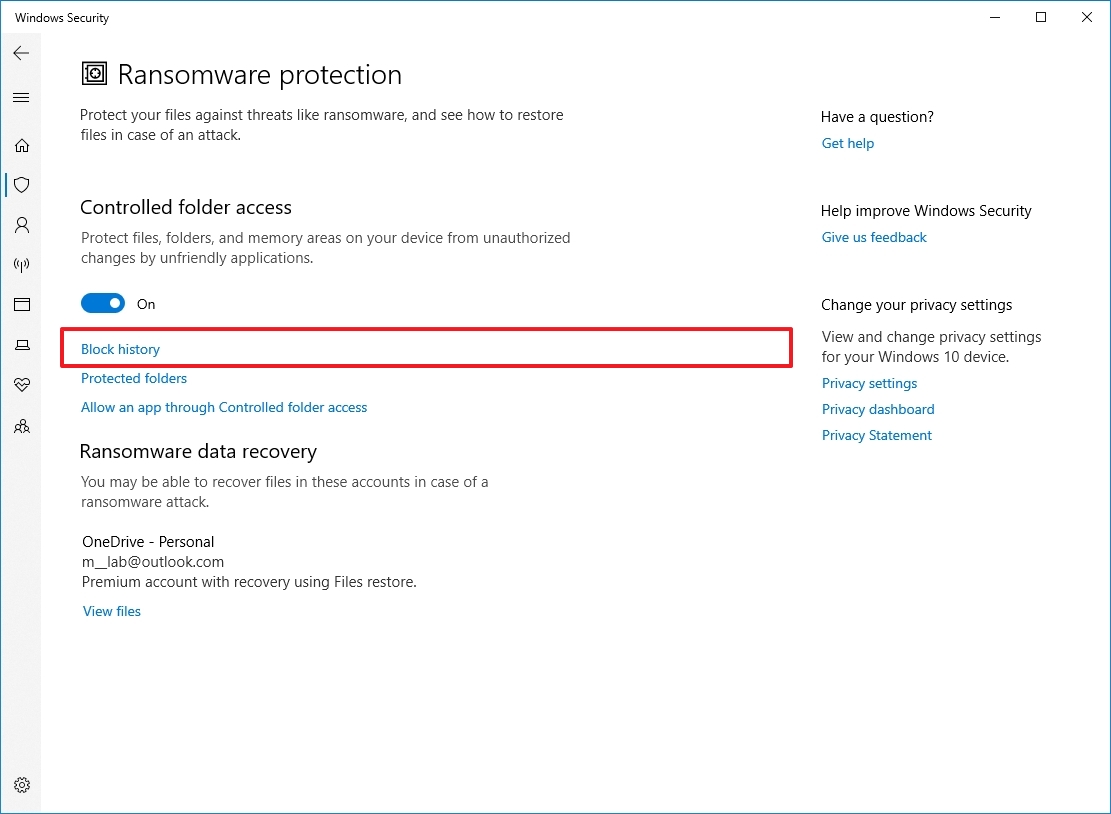
To view a list of blocked items by the anti-ransomware solution, use these steps:
All the latest news, reviews, and guides for Windows and Xbox diehards.
- Open Start.
- Search for Windows Security and click the top result to open the app.
- Click on Virus & threat protection.
- Click the Manage ransomware protection option under the "Ransomware protection" section.
- Click the Block history option.
- Confirm the items that have been blocked.
The page is the same page to view the protection history available through the main page of the Microsoft Defender Antivirus. However, accessing it from this area applies a filter to list only the history of "Controlled folder access."
Add new location for protection
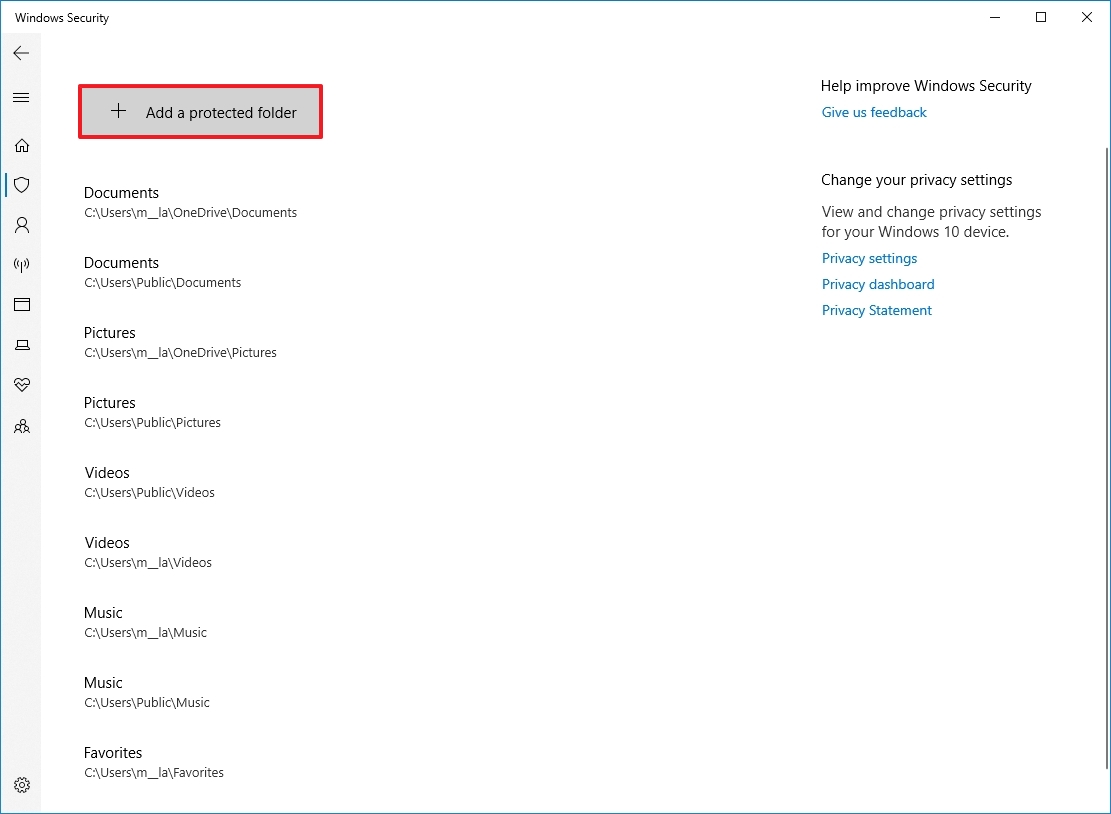
By default, the security feature protects the Documents, Pictures, Videos, Music, Desktop, and Favorites folders. Although it's not possible to modify the default list, if you have files in a different location, you can manually add other paths.
To add a new folder location for protection, use these steps:
- Open Start.
- Search for Windows Security and click the top result to open the app.
- Click on Virus & threat protection.
- Click the "Manage ransomware protection" option under the "Ransomware protection" section.
- Click the Protected folders option.
- Click the "Add a protected folder" button.
- Select the new location.
- Click the Select Folder button.
After you complete the steps, the anti-ransomware feature will monitor and protect the new locations.
If the storage configuration changes, and you need to remove a location, you can follow the same instructions, but in step 5, select the location and click the "Remove" button.
Whitelist apps with Controlled folder access
On Windows 10, Controlled folder access can detect the apps that can safely access your files, but in the case one of the apps you trust is blocked, you'll need to allow the app manually.
To whitelist an app with Controlled folder access, use these steps:
- Open Start.
- Search for Windows Security and click the top result to open the app.
- Click on Virus & threat protection.
- Click the "Manage ransomware protection" option under the "Ransomware protection" section.
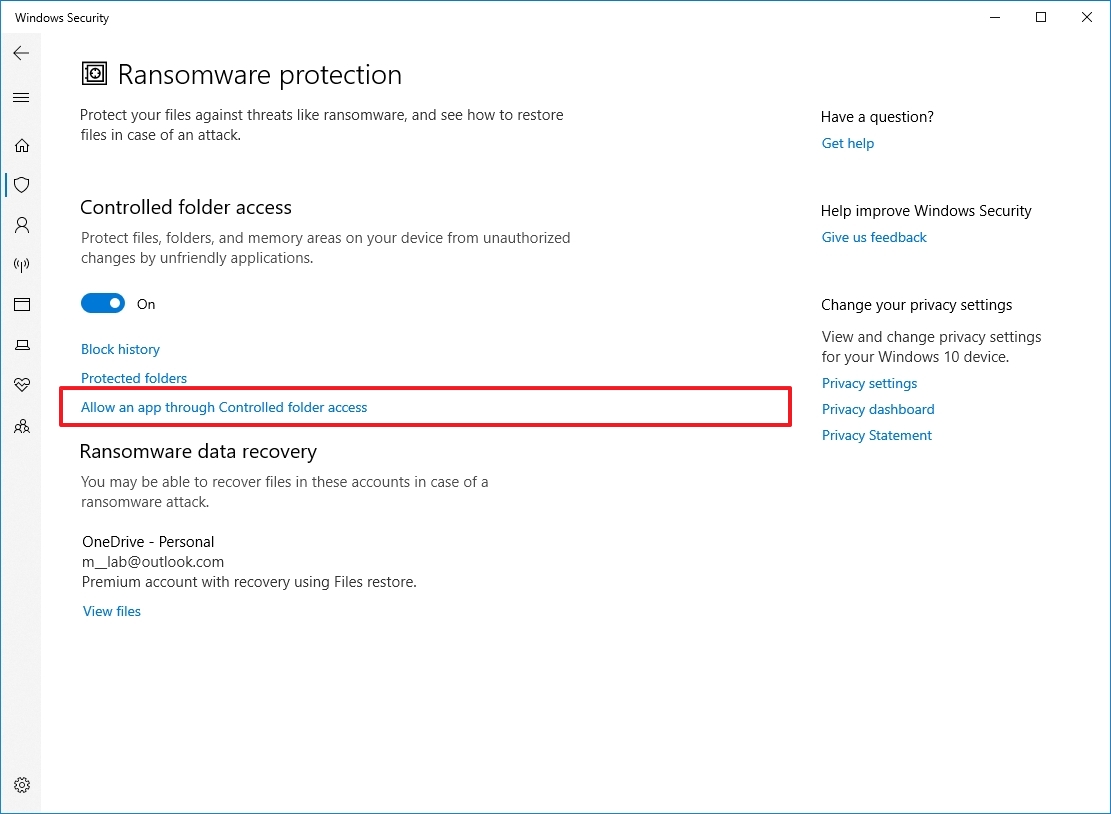
- Click the "Allow an app through Controlled folder access" option.
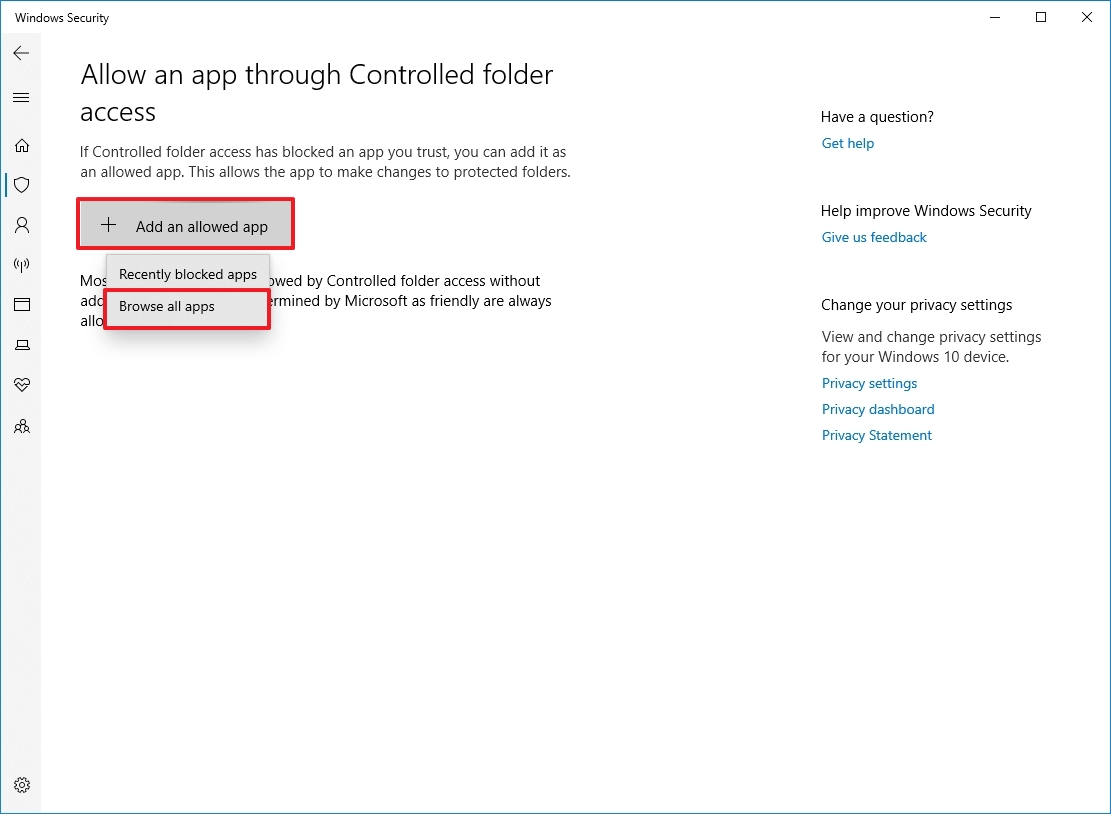
- Click the "Add an allowed app" button.
- Select the "Recently blocked apps" option to whitelist an app you trust has been flagged as malicious. Or click the "Browse all apps" option.
- Select the app executable (for example, chrome.exe) you want to allow through this feature.
- Click the Open button.
Once you complete the steps, the app won't be blocked by the feature, and it'll be able to make changes to files.
How to enable ransomware protection from Group Policy
To enable Windows 10's ransomware protection with Group Policy, use these steps:
- Open Start.
- Search for gpedit and click the top result to open the Local Group Policy Editor.
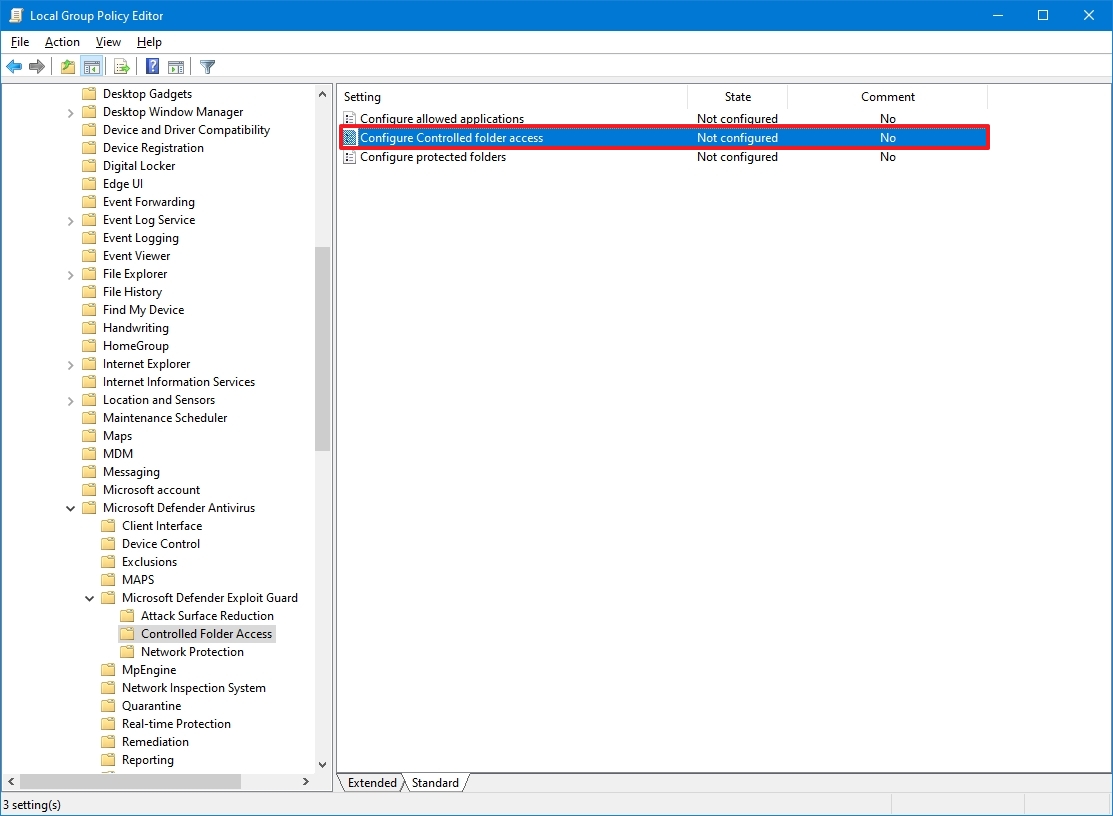
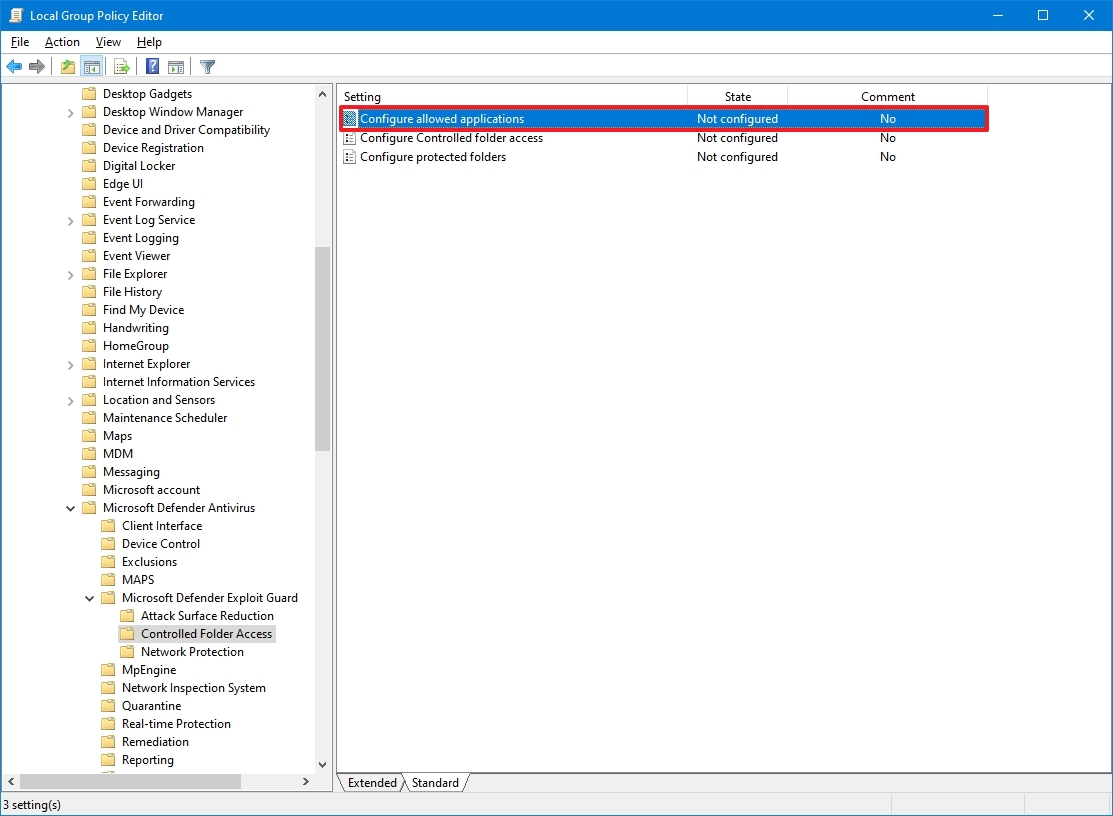
- Browse the following path: Computer Configuration > Administrative Templates > Windows Components > Microsoft Defender Antivirus > Microsoft Defender Exploit Guard > Controlled Folder Access
- Double-click the "Configure Controlled folder access" policy on the right side.
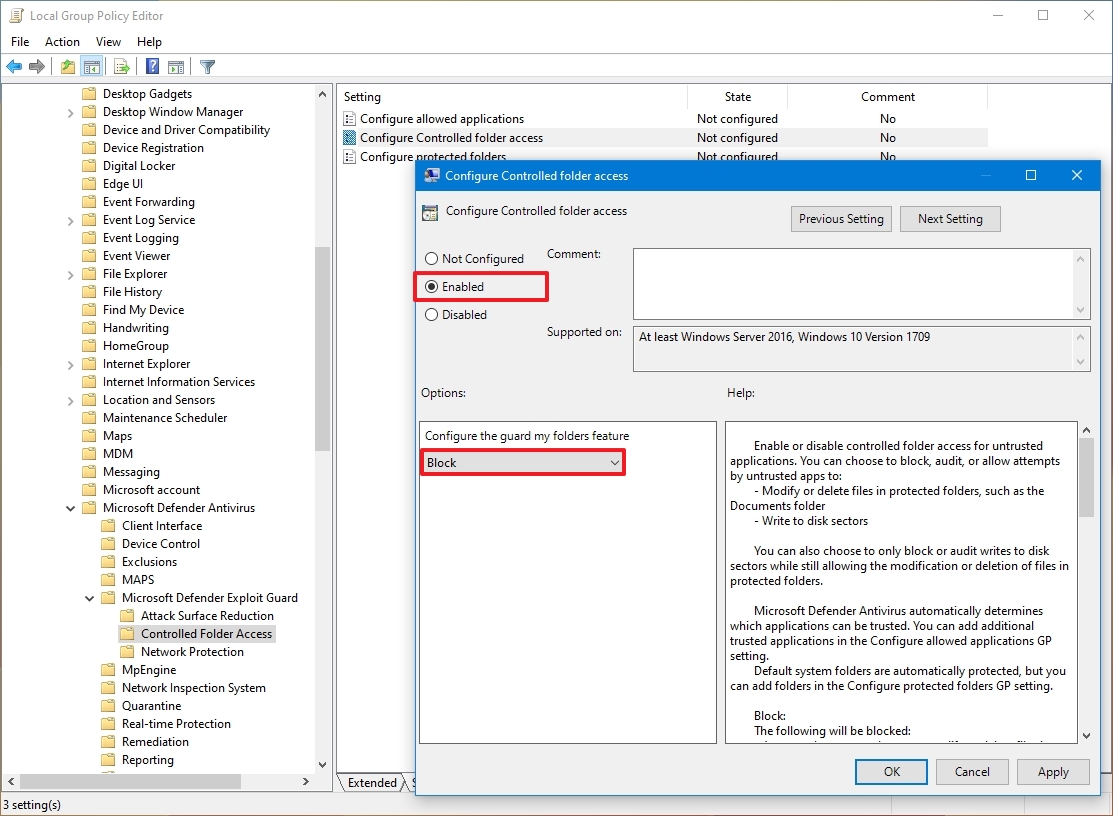
- Select the Enabled option.
- Select the Block option under the "Options" section.
- Click the Apply button.
- Click the OK button.
After you complete the steps, Controlled folder access will start monitoring and protecting your files stored in the default system folders.
The only caveat of using this method is that any future configuration will have to be made through Group Policy. If you open Windows Security, you'll notice the "This setting is managed by your administrator" message and the Controlled folder access option will appear grayed out.
You can revert the changes using the same instructions, but in step 5, select the "Not Configured" option.
Add new location for protection
If you must protect data located in a different location, you can use the "Configure protected folders" policy to add the new folder.
To include a new location for protection with Control folder access, use these steps:
- Open Start.
- Search for gpedit and click the top result to open the Local Group Policy Editor.
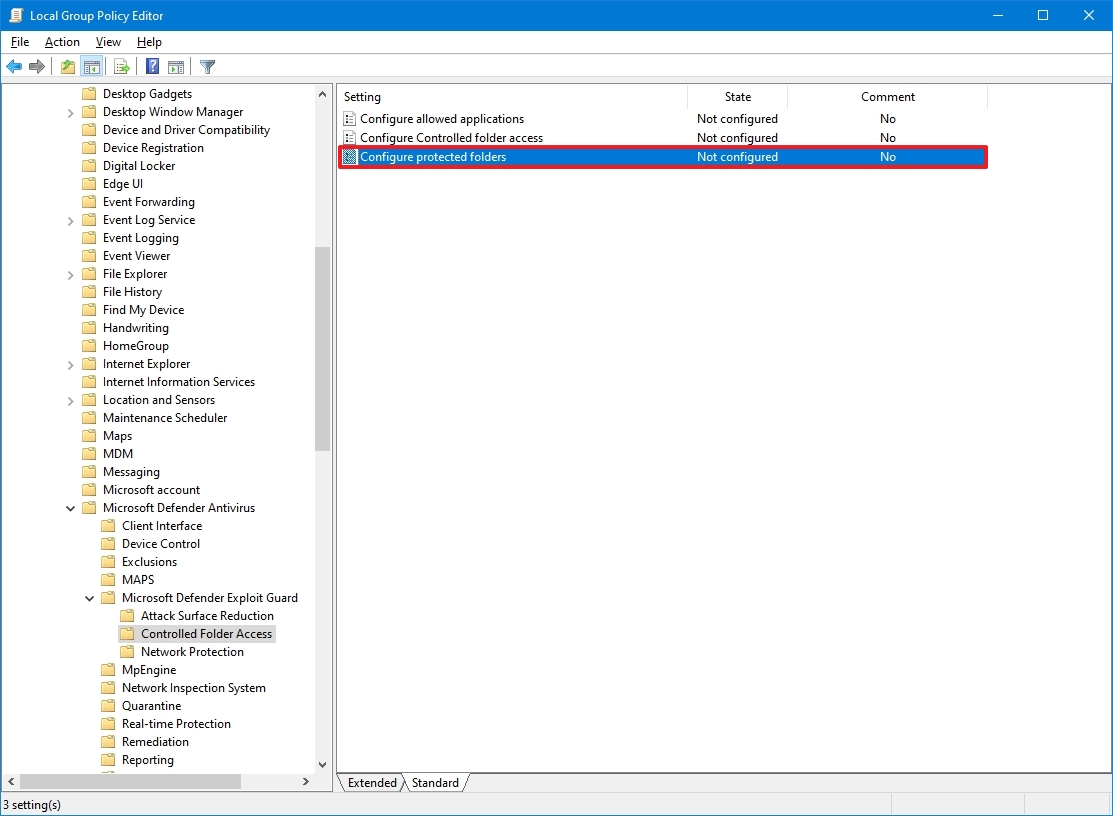
- Browse the following path: Computer Configuration > Administrative Templates > Windows Components > Microsoft Defender Antivirus > Microsoft Defender Exploit Guard > Controlled Folder Access
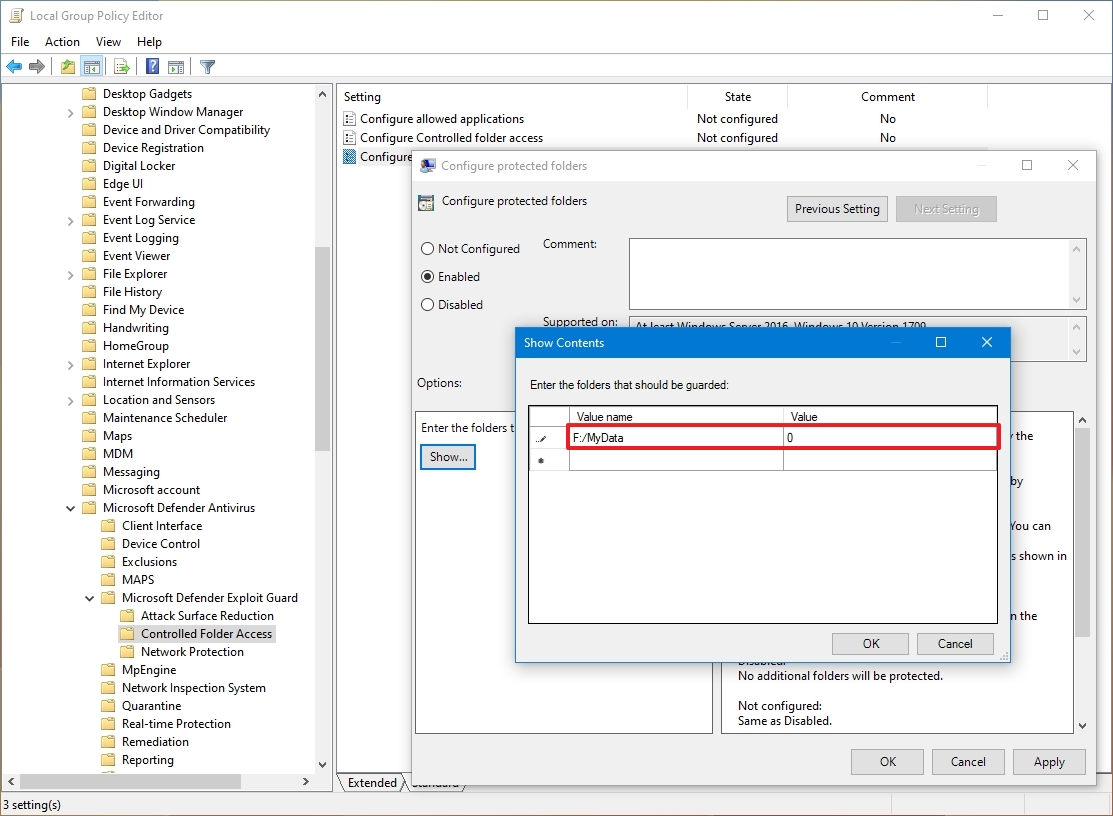
- Double-click the "Configure protected folders" policy on the right side.
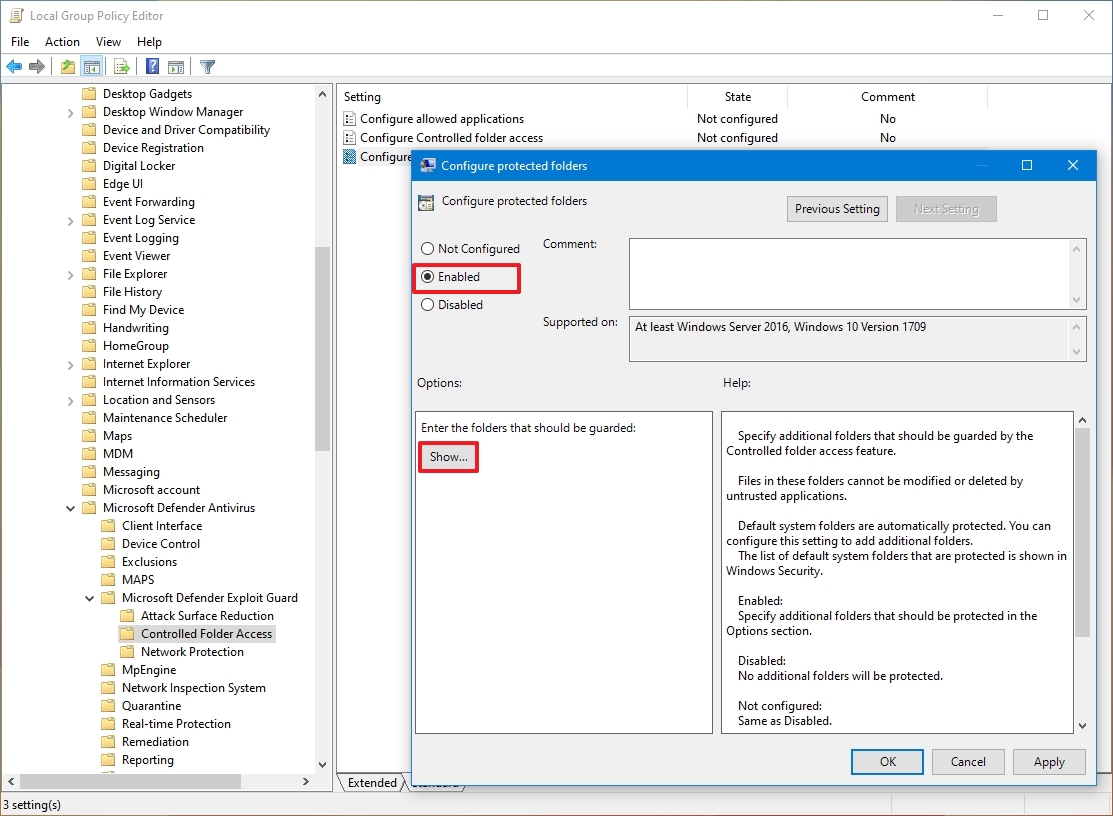
- Select the Enabled option.
- Click the Show button under the "Options" section.
- Specify the locations you want to protect by entering the path of the folder in the "Value name" field and adding 0 in the "Value" field. This example adds the "MyData" folder in the "F" drive for protection:
F:\MyData
- Repeat step 7 to add more locations.
- Click the OK button.
- Click the Apply button.
- Click the OK button.
Once you complete the steps, the new folder will be added to the protection list for controlled folder access.
To revert the changes, use the same instructions, but in step 5, select the "Not Configured" option.
Whitelist apps with Controlled folder access
To whitelist an app through the anti-ransomware feature on Windows 10, use these steps:
- Open Start.
- Search for gpedit and click the top result to open the Local Group Policy Editor.
- Browse the following path: Computer Configuration > Administrative Templates > Windows Components > Microsoft Defender Antivirus > Microsoft Defender Exploit Guard > Controlled Folder Access
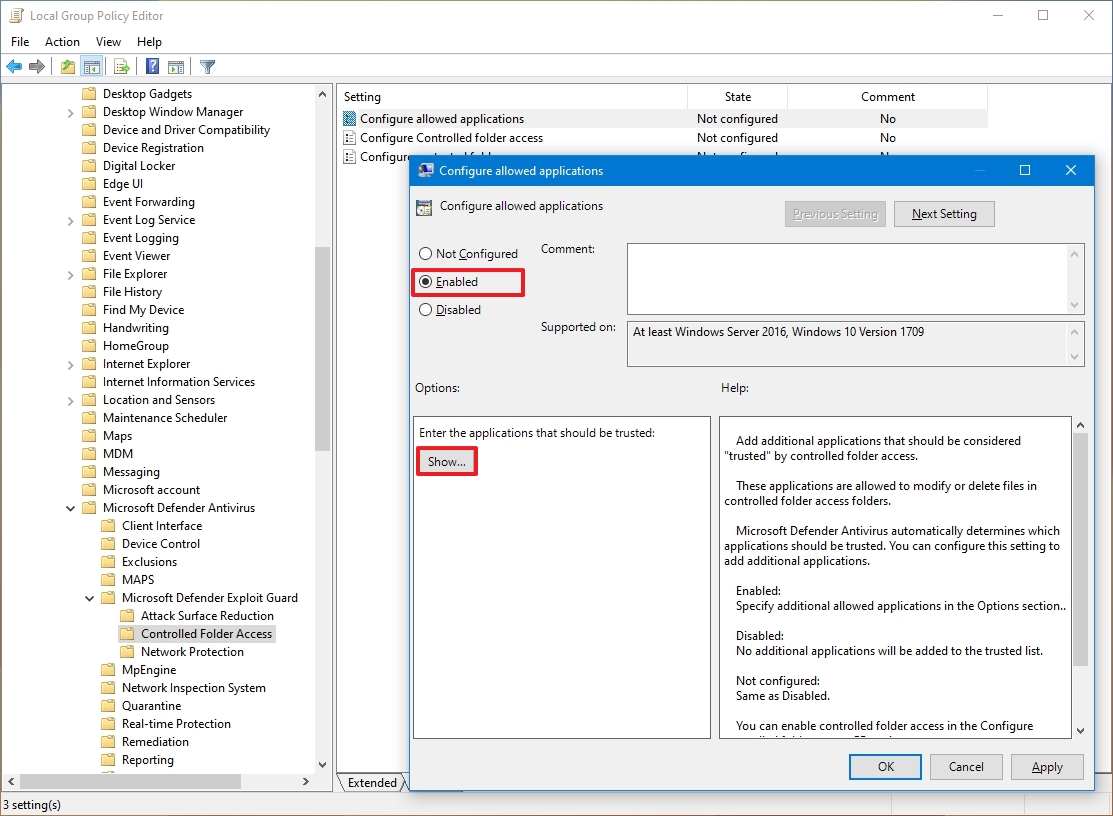
- Double-click the "Configure allowed applications" policy on the right side.
- Select the Enabled option.
- Click the Show button under the "Options" section.
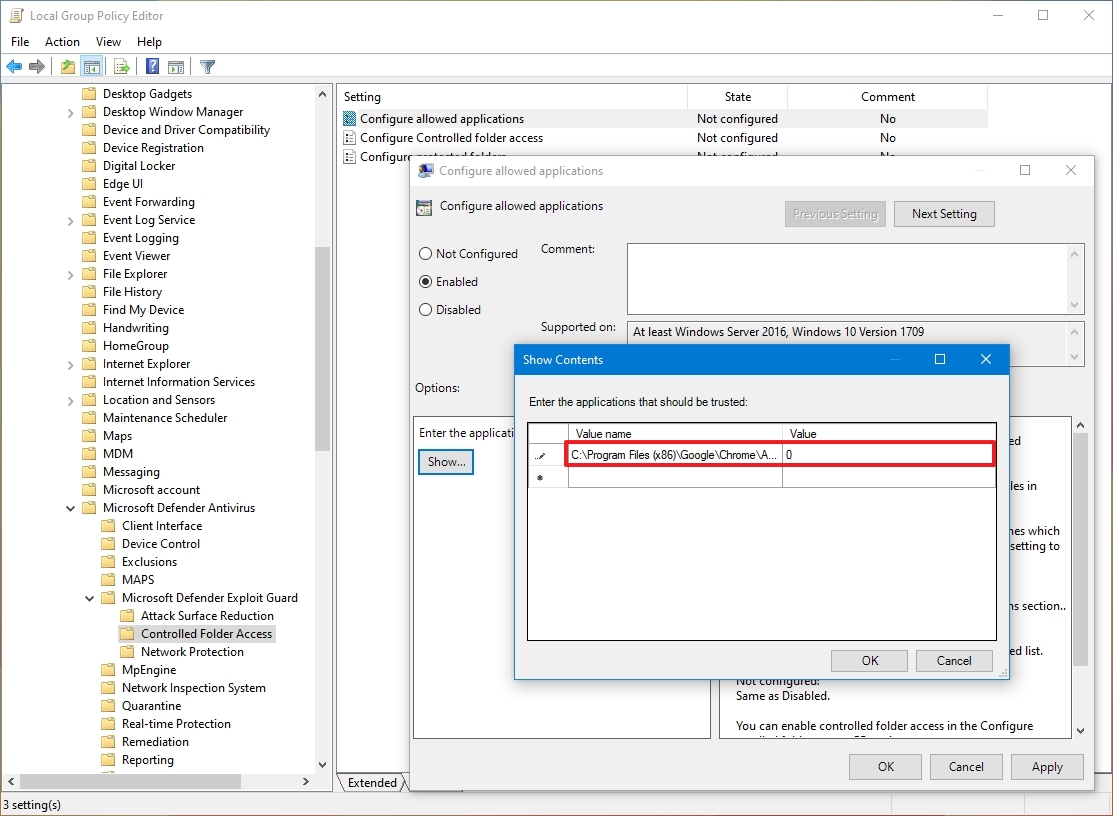
- Specify the location of the .exe file for the app (such as
C:\path\to\app\app.exe) you want to allow in the "Value name" field and add 0 in the "Value" field. This example allows the Chrome app when Controlled folder access is enabled: C:\Program Files (x86)\Google\Chrome\Application\chrome.exe
- Repeat step 7 to add more locations.
- Click the OK button.
- Click the Apply button.
- Click the OK button.
After you complete the steps, the app won't be blocked, and it'll be able to make changes to protected files and folders.
How to enable ransomware protection using PowerShell
Alternatively, you can also enable and configure Controlled folder access using PowerShell commands.
To enable Controlled folder access with PowerShell, use these steps:
- Open Start.
- Search for PowerShell, right-click the top result, and click the Run as administrator option.
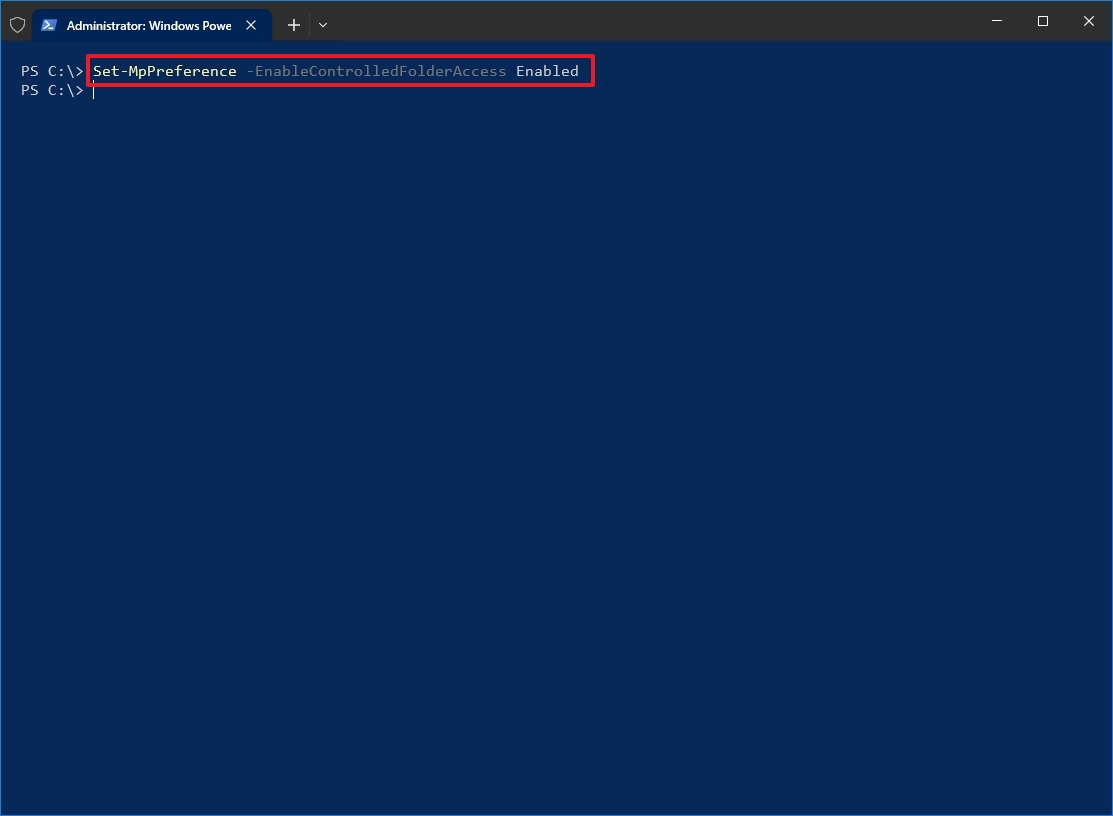
- Type the following command to enable the feature and press Enter: Set-MpPreference -EnableControlledFolderAccess Enabled
- (Optional) Type the following command to disable the security feature and press Enter: Set-MpPreference -EnableControlledFolderAccess Disabled
Once you complete the steps, Controlled folder access will enable on your computer to protect files and folders from ransomware attacks.
Add new location for protection
To allow Controlled folder access to protect an additional folder, use these steps:
- Open Start.
- Search for PowerShell, right-click the top result, and click the Run as administrator option.
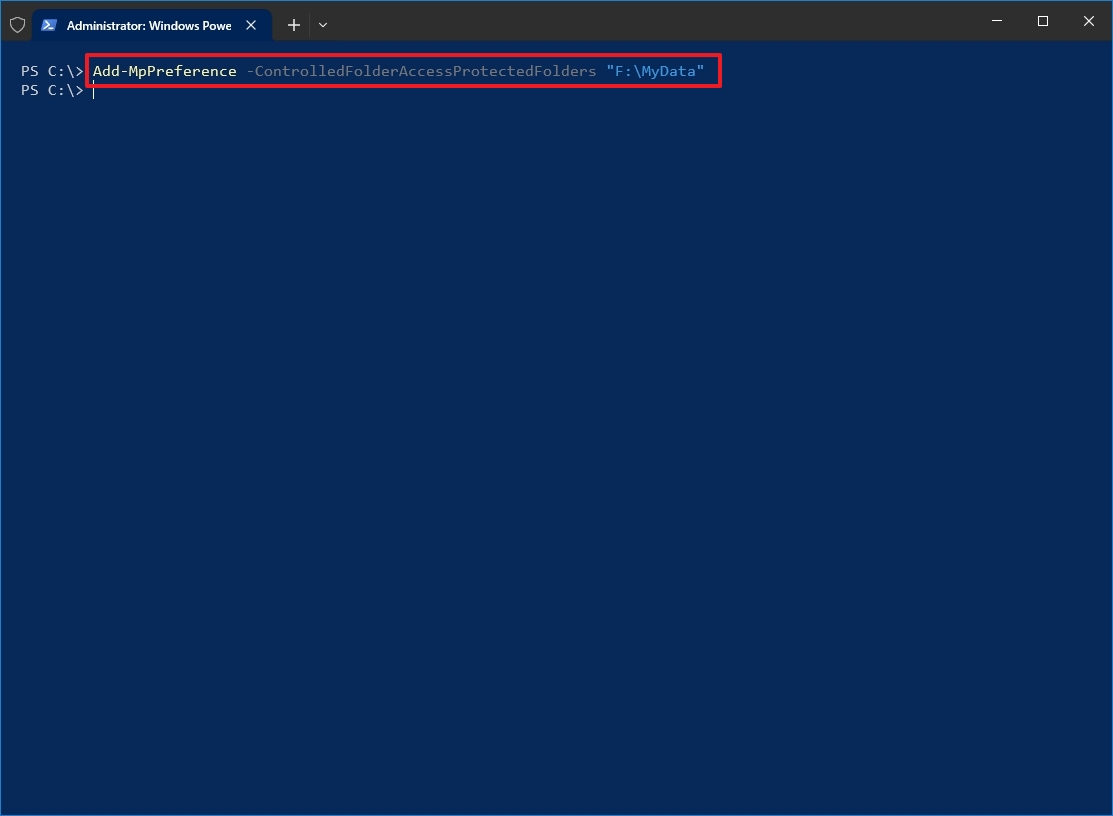
- Type the following command to add a new location and press Enter: Add-MpPreference -ControlledFolderAccessProtectedFolders "F:\folder\path\to\add"
In the command, make sure to change the path for the location and executable of the app you want to allow. For example, this command adds the "MyData" folder in the "F" drive to the list of protected folders: Add-MpPreference -ControlledFolderAccessProtectedFolders "F:\MyData"
- (Optional) Type the following command to remove a folder and press Enter: Disable-MpPreference -ControlledFolderAccessProtectedFolders "F:\folder\path\to\remove"
After you complete the steps, the anti-ransomware feature will protect the contents inside the new location.
Whitelist apps with Controlled folder access
To allow an app in Controlled folder access with PowerShell, use these steps:
- Open Start.
- Search for PowerShell, right-click the top result, and click the Run as administrator option.
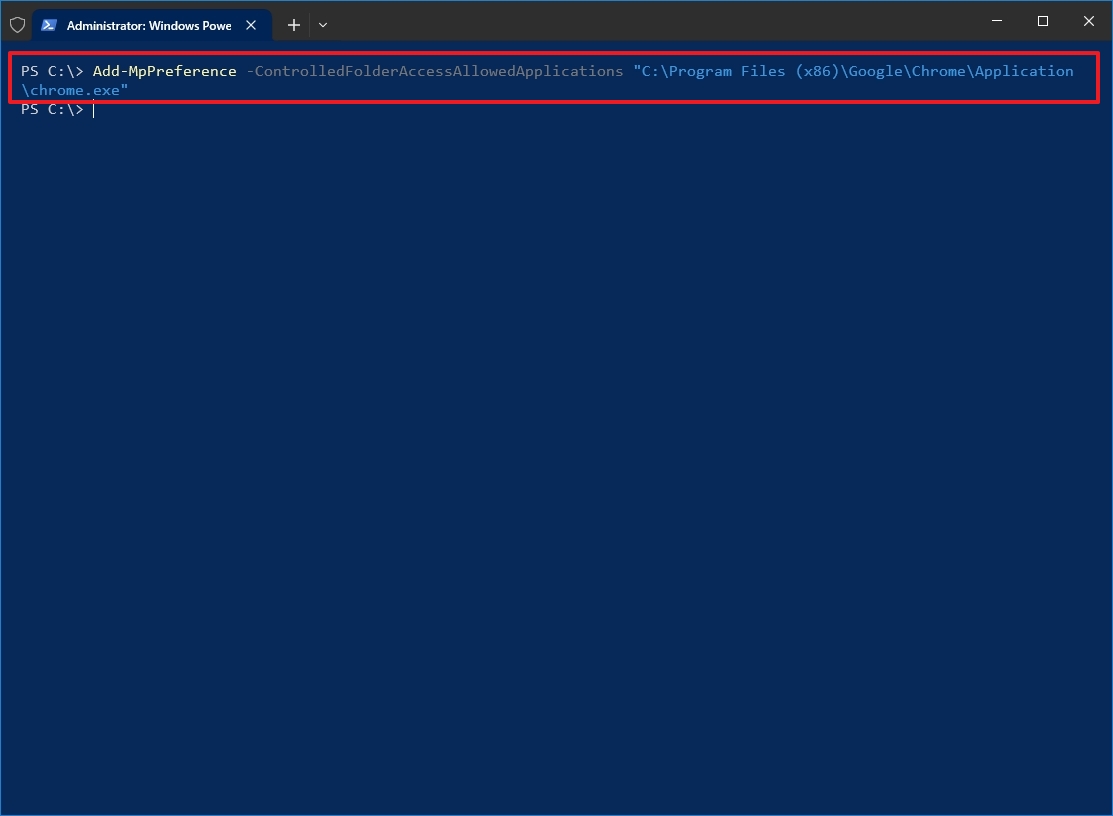
- Type the following command to allow an app and press Enter: Add-MpPreference -ControlledFolderAccessAllowedApplications "F:\path\to\app\app.exe"
In the command, make sure to change the path for the location and executable of the app you want to allow. For example, this command adds Chrome to the list of allowed apps: Add-MpPreference -ControlledFolderAccessAllowedApplications "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe"
- (Optional) Type the following command to remove an app and press Enter: Remove-MpPreference -ControlledFolderAccessAllowedApplications "F:\path\to\app\app.exe"
Once you complete the steps, the app will be allowed to run, and changes to your files will be made when the feature is available.
Controlled folder access is one of the intrusion-prevention features of the Microsoft Defender Exploit Guard, which is part of the Microsoft Defender Antivirus. This means that the security feature won't be available if you use a third-party antivirus.
More resources
For more helpful articles, coverage, and answers to common questions about Windows 10 and Windows 11, visit the following resources:
- Windows 11 on Windows Central — All you need to know
- Windows 10 on Windows Central — All you need to know

Mauro Huculak has been a Windows How-To Expert contributor for WindowsCentral.com for nearly a decade and has over 22 years of combined experience in IT and technical writing. He holds various professional certifications from Microsoft, Cisco, VMware, and CompTIA and has been recognized as a Microsoft MVP for many years.