How to improve Windows 11 security using Administrator Protection — shielding your PC with a switch buried in its settings
Windows 11 adds an extra layer of security, but you have to enable it manually. Here's how.
All the latest news, reviews, and guides for Windows and Xbox diehards.
You are now subscribed
Your newsletter sign-up was successful
On Windows 11, Administrator Protection is a new security feature arriving with the November 2025 Patch Tuesday Update that adds an extra layer of security by prompting an authorization dialog using Windows Hello when an unsigned or untrusted app requests elevation.
The feature may seem similar to User Account Control (UAC), but it works differently. The account control feature is designed to prevent unwanted system changes by showing a consent dialog whenever an action requires administrative rights.
In this process, the UAC feature creates two tokens at sign-in, including a standard user token and an administrator token. When an elevated action is required, the system uses the administrator token. However, since both tokens share access to the user profile, this design can be exploited as a potential security vulnerability.
On the other hand, Administrator Protection handles this limitation with a more advanced approach. Instead of relying on tokens tied to the active user, it generates an isolated, hidden system-managed account to take elevation requests. During the prompt request, the system creates this temporary account on demand, uses it to perform the elevated action, and then deletes it once the task is complete.
In this how-to guide, I'll outline the steps to enable the Administrator Protection feature on Windows 11.
This is a friendly reminder that editing the Registry is risky and can cause irreversible damage to your installation if you don't do it correctly. Before proceeding, it's recommended that you make a full backup of your PC.
How to configure Administrator Protection using Group Policy on Windows 11
To use the new Administrator Protection security feature, use these steps:
- Open Start.
- Search for Group Policy Editor and click the top result to open the app.
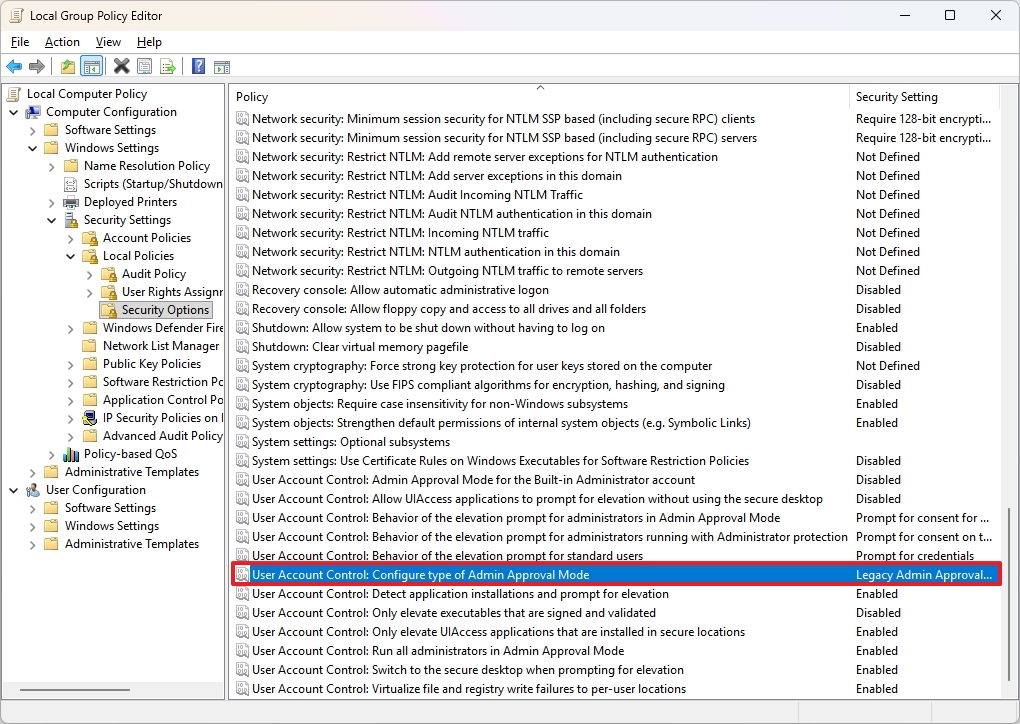
- Open the following path: Computer Configuration > Windows Settings > Security Settings > Local Policies > Security Options
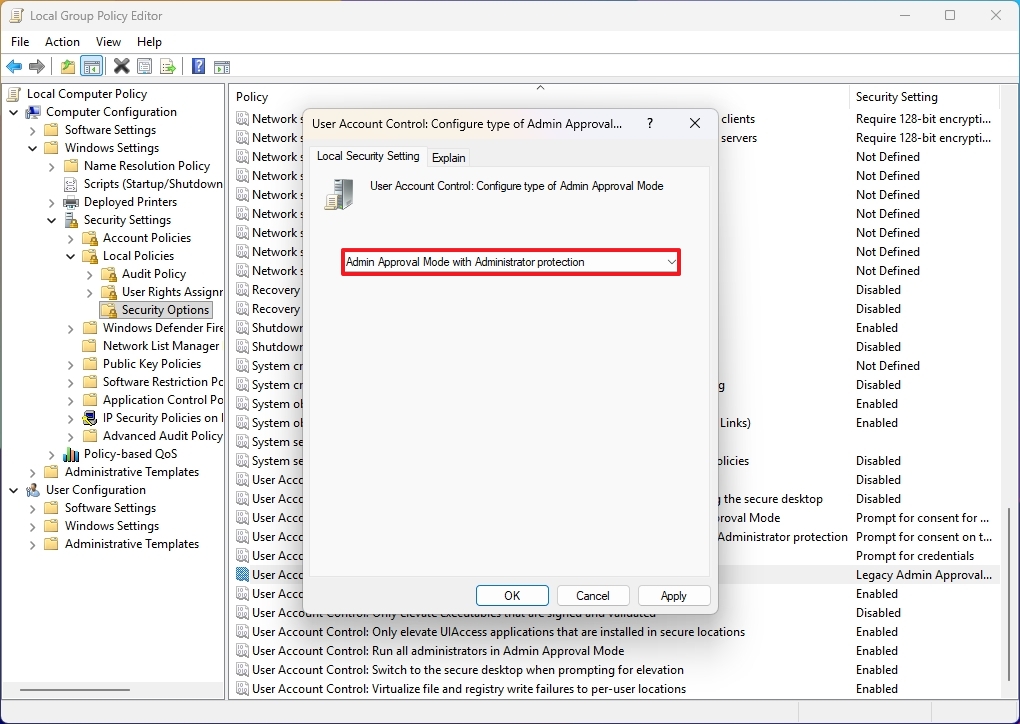
- Double-click the "User Account Control: Configure type of Admin Approval Mode" policy.
- Click the "Local Security Setting" tab.
- Select the "Admin Approval Mode with Administrator protection" option.
- Click the Apply button.
- Click the OK button.
- Reboot your device to apply the changes.
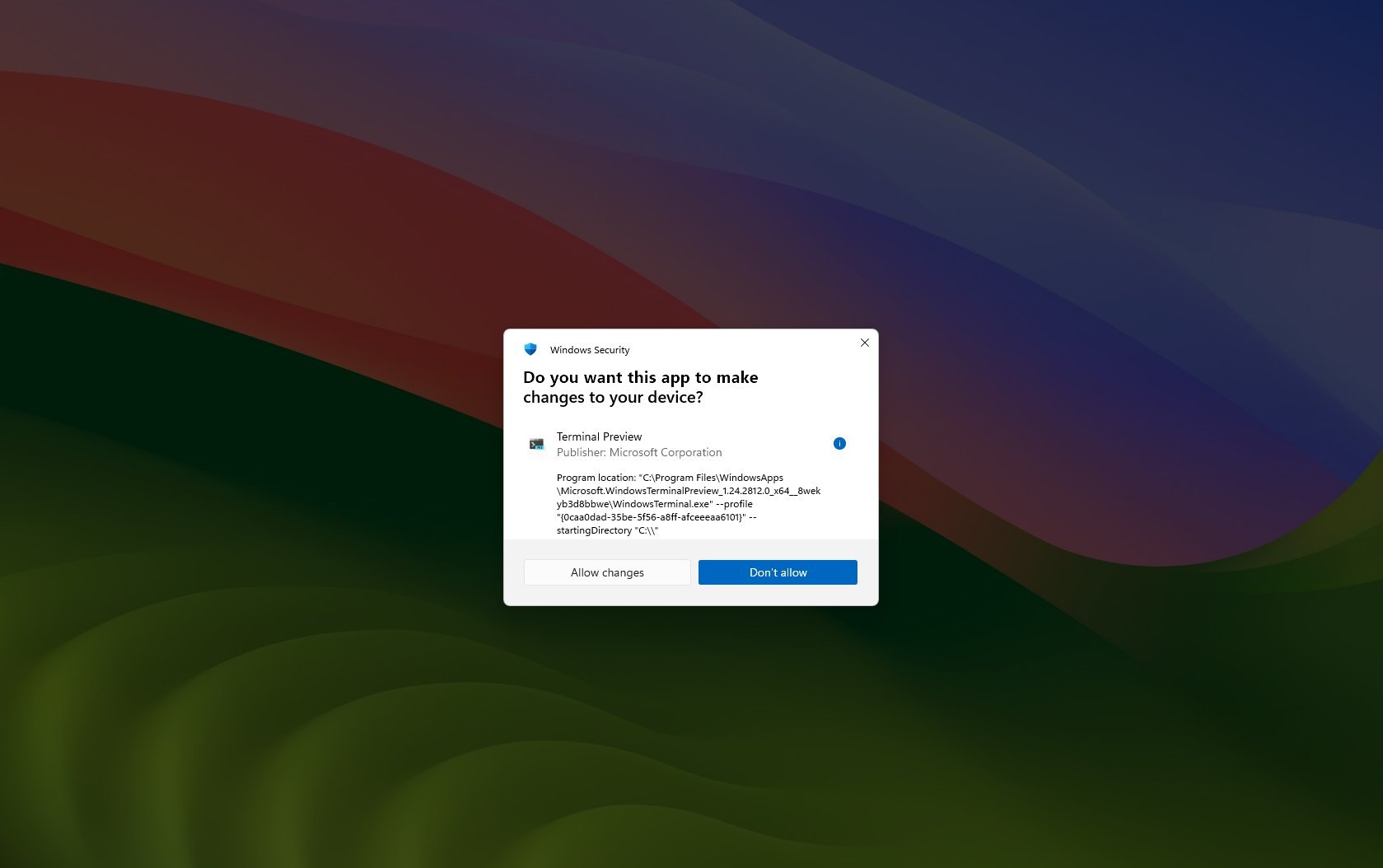
Once you complete the steps, the next time you try to run a command or open a setting or an app that requires elevation, you will receive a Windows Security consent using the new security feature instead of the User Account Control (UAC) prompt.
If you want to disable the feature, you can use the same instructions, but on step 6, make sure to select the "Local Admin Approval Mode (Default)" option.
How to configure Administrator Protection using Registry on Windows 11
To enable the Administrator Protection feature using the Registry, use these steps:
- Open Start.
- Search for regedit and click the top result to launch the Registry Editor.
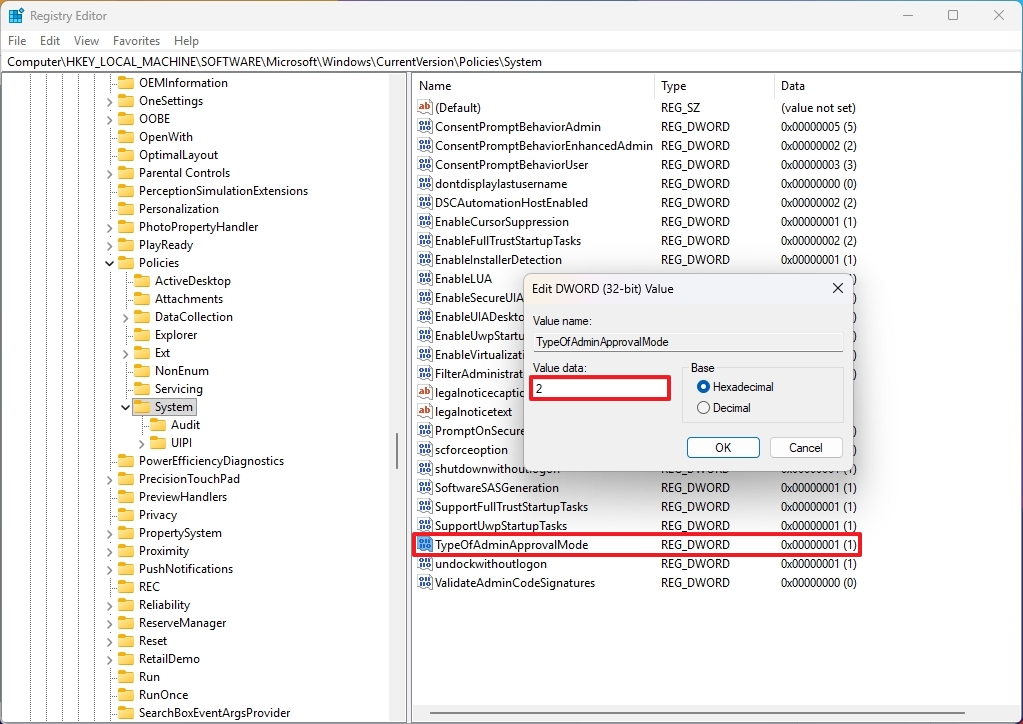
- Open the following path: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
- Double-click the TypeOfAdminApprovalMode key and change its value to 2 to enable the feature.
- Click the OK button.
- Reboot your device to apply the changes.
After you complete the steps, the feature will turn on for commands, settings, and applications that require elevation.
If you want to revert the changes, use the same steps outlined above, but in step 4, set the value to 1.
The Registry methods should work on Windows 11 Pro and Windows 11 Home.
More resources
Explore more in-depth how-to guides, troubleshooting advice, and essential tips to get the most out of Windows 11 and 10. Start browsing here:
- Windows 11 on Windows Central — All you need to know
- Windows 10 on Windows Central — All you need to know

Follow Windows Central on Google News to keep our latest news, insights, and features at the top of your feeds!

Mauro Huculak has been a Windows How-To Expert contributor for WindowsCentral.com for nearly a decade and has over 22 years of combined experience in IT and technical writing. He holds various professional certifications from Microsoft, Cisco, VMware, and CompTIA and has been recognized as a Microsoft MVP for many years.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.